- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
A little help with Subinterfaces and intraVLAN routing
- LIVEcommunity
- Discussions
- General Topics
- A little help with Subinterfaces and intraVLAN routing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-22-2017 07:40 AM
I have a PA-3020 with fairly typcial config with a L3 untrusted interface and several trusted sub interfaces. I have a couple questions.
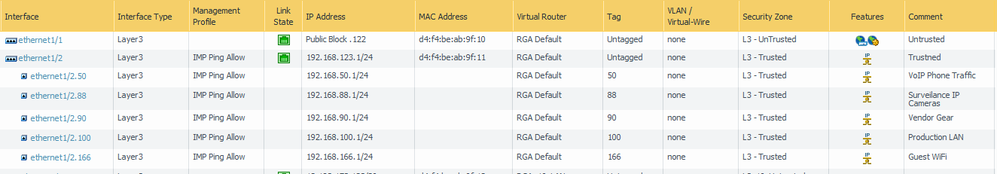
Prior to this, I was doing my intravlan routing on my core HP2920 switch. My 192.168.123.0/24 network is the native vlan 1 which I understand to be always untagged. The .123 is my "original" network before I outgrew it and had to vlan. All the subinterface training examples show multiple sub's but don't say anything about including untagged traffic. You can see in my pic that I put an IP address on the actual 1/2 interface as my solution to this.
The network is working but I'm getting random network connection errors, specifically for traffic between vlan 1/.123 traffic and vlan100/.100. I have a couple servers in the .123 and all the client pcs have migrated to vlan100. All my switches are in the 123 subnet and their gateways are the 192.168.123.1 interface 1/2 if that matters Do I need to move all my .123 gear into a vlan and add a subinterface with the 192.168.123.1 IP?
Does the security policy take care of all the intra-vlan routing? I'm used to having static routes in the "router" to the gateways of the vlans. I mainly ask this due to the above mentioned random network connection issues. I wasn't sure if I needed to add any routing due to the untagged nature of the .123 traffic coming into the interface?
I'm going to check the logs and do some testing to see if I can figure out the newtork issues. I've love some feedback on whether my network interface setup is solid before I spend a lot of time looking for zebras instead of horses. Thanks,
-Ralph
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2017 12:46 AM
You did the correct thing: untagged (or vlan 1) is configured on physical interface, VLANs are on subinterfaces.
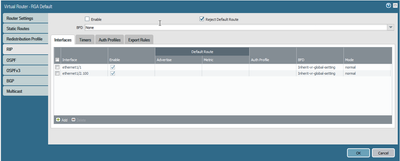
You don't need to do any routing, for these VLANs as all are connected networks.
Security profiles (IPS, AV..) are only enforced when traffic passes between security zones. So I would suggest replacing single zone 'L3 Trusted' with multiple zones like 'L3 Trusted LAN', 'L3 Trusted Servers', 'L3 Trusted MGMT'... as per your network segments.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2017 12:46 AM
You did the correct thing: untagged (or vlan 1) is configured on physical interface, VLANs are on subinterfaces.
You don't need to do any routing, for these VLANs as all are connected networks.
Security profiles (IPS, AV..) are only enforced when traffic passes between security zones. So I would suggest replacing single zone 'L3 Trusted' with multiple zones like 'L3 Trusted LAN', 'L3 Trusted Servers', 'L3 Trusted MGMT'... as per your network segments.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2017 05:44 AM
Thanks, I do have security zones ready for each of the vlans but when I ran into the question on what to do about my untagged traffic I just left then all in trusted until I understood it better.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2017 05:50 AM
When you will start implementing security zones keep in mind you also have to implement FW rules as traffic between different zones is dropped by default.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2017 09:39 AM
Ok, will make sure the create security policies as I go. Final question on the routing. I just noticed that RIP is on for two of the interfaces in my router. I don't recall ever turning that on, and it's only for one of my sub interfaces and my untrusted internet interface.
- 1 accepted solution
- 4732 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- AWS GWLB VPC Endpoint Associations no longer work post-upgrade in General Topics
- Layer 2 subinterfaces w/ Vlan interface for routing..... in General Topics
- Asynchronous Security Zones? in General Topics
- SSL Forward Proxy Configuration Question in VM-Series in the Public Cloud
- Palo Alto interfaces in Layer 2 - Portchannel - Log Monitor more details in General Topics