- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Accessing web systems using main office's IP trough IPSec tunnel
- LIVEcommunity
- Discussions
- General Topics
- Accessing web systems using main office's IP trough IPSec tunnel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Accessing web systems using main office's IP trough IPSec tunnel
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-06-2013 04:46 AM
Hello.
We have a few IPsec S-2-S tunnels with different devices on other side and all works nice, but in one of them is required, that users on other side can use internet resources (to get this sides WAN IP address and access few web systems that with restricted usage by IP's) trough main office.
What would be the correct or at least theoretical configuration to get such thing work? I've done some sloppy testing with routes but usually connection and tunnel just drops dead or nothing happens.
One way, of course, is proxy (install local server on main side and just configure other sides browsers network configuration) and it's the easy way for me, but not for the users. They would have to turn proxy settings on or off, it they wanted to use their local internet resources for casual internet browsing.
Device on other side is a Microtik router.
Besides that, tunnel works nice. I can join domain and do stuff as usual.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-06-2013 05:18 AM
Hi,
IF you've got no palo on remote site, in my mind you have to modify:
- Proxy ID (subnet) on both remote and central Palo
- Be sure that security rule on your central palo allow traffic from this remote site to internet (Zone + Subnet)
- Be sure that your internet NAT rule match for remote subnet and remote VPN zone.
After that, should be ok
v.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-06-2013 06:29 AM
In PA side, i have interface, that is dedicated for VPN and policies that provides access to internal resources: VPN_POLICY - LAN_POLICY and rule for access to internet (if its correct): VPN_POLICY - WAN_INTERFACE.
As goes for NAT rules or any other configuration besides IPSec's on Mikrotik side, i will add some pictures. Route is default to provide that connection works.
pics ->here<-
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-06-2013 06:42 AM
Hi,
In your print screen, on the paloalto, you configure just proxy-ID with just two subnets, maybe you have to configure on palo local subnet 0.0.0.0/0.
Let me know
V.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2013 04:46 AM
I played a little with proxy ID's on both sides (changes sources, destinations and stuff), but with no real result.
What would be the correct way to configure such thing if i would have PA devices on both sides? Maybe according to such configuration, i could get to work that mikrotik router and see if i did something wrong in previous config tests.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2013 06:22 AM
If you have palo on both side, on remote, you just have to create a default route like
destination: 0.0.0.0/0
interface: tunnelX
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-04-2013 01:51 AM
I'm practicing necromancy by bring up this old post of mine. Then I settled with using proxy and all is acceptable, but for some trial time i got an CheckPoint SG80 device with OS version R75 with plans to get the same - get all traffic trough VPN so users behind CP device can use Web apps with PA external IP. Creating VPN is easy, bet when i active on CP "Route all traffic trough this site"
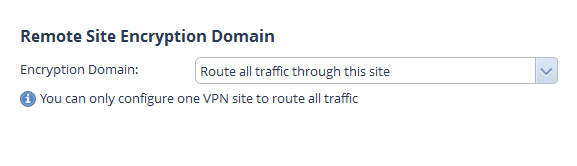
and set proxy ID on PA like local: 192.168.0.0/24 and remote: 0.0.0.0/0 tunnel partially goes down. I can ping from PA to CP, but can't ping from CP to PA.
System log shows, where *.*.*.118 is CP external IP:
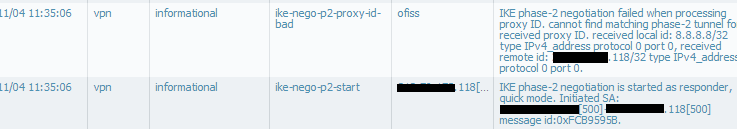
Does this "error" shows that computer behind CP is sending dns requests to google dns server but PA does not know what to do whit that? What would be proxy ID if on the other side would be an PA device with config like VinceM previously given?
- 4590 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- We enable the virtual system on firewall and facing the "No Accessible virtual system" in Next-Generation Firewall Discussions
- SYSTEM ALERT : medium : Could not access threat vault in General Topics
- Website Access Issue from one of branch office in General Topics
- provide temporary internet access for some systems at specific period(1day) in Next-Generation Firewall Discussions



