- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
ADFS SAML Configuration
- LIVEcommunity
- Discussions
- General Topics
- Re: ADFS SAML Configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
ADFS SAML Configuration
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-24-2017 06:54 PM
Hi all
I need help to configure ADFS SAML with global-protect.
i have successfully imported the metadata.xml from adfs into palo.
But now i can't export the metadata from paloalto.
Whats the correct identifiers and endpoints urls for global-contect clientless? I have no idea, what i must configure in adfs.
Can anyone help?
I use panos 8.0
regards
Benjamin
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-28-2017 06:23 AM
I solved the issue with the cli and now i have a connection from adfs to palo. But i can't login with adfs to palo alto. Has anyone experience with adfs -> saml palo alto?
i don't know what username attribute i must use for saml.
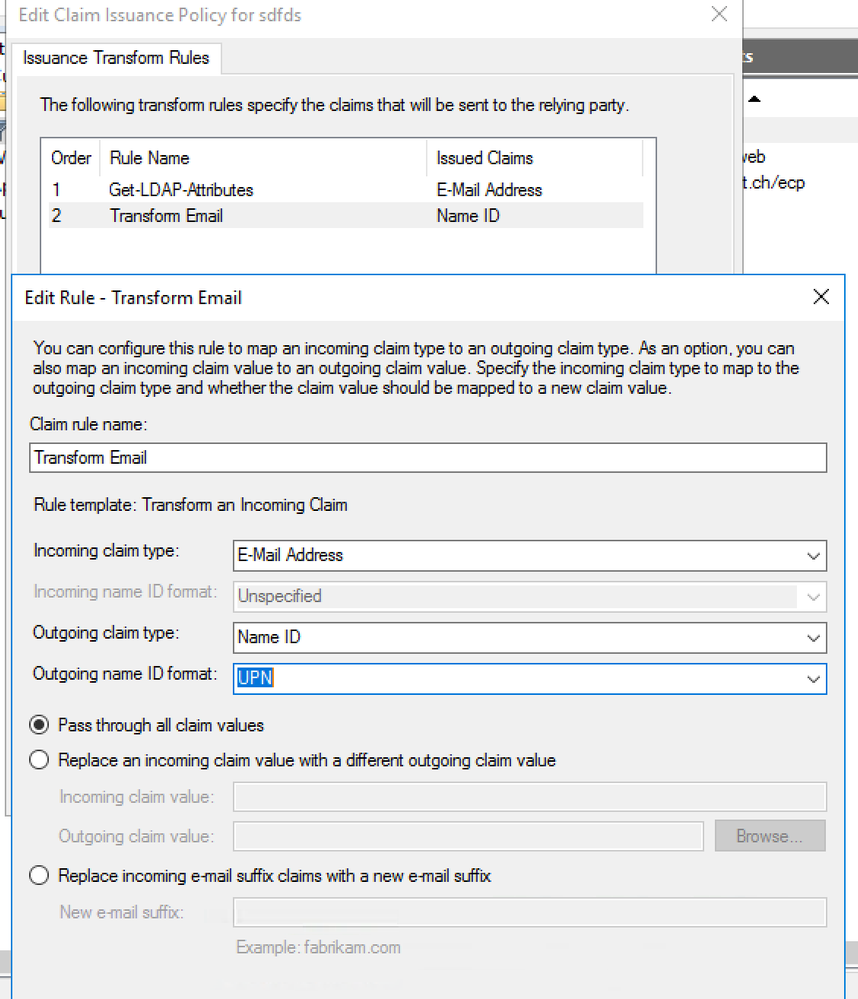
I created this rule in the adfs:
Palo Alto Saml Profile:
Could anyone help me?
Regards
Benjamin
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-28-2017 03:54 PM
Hello,
While I have not set this up before, I am familiure with ldap. For the User attriobute, have you tried sAMAccountName?
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2017 12:18 AM
Yes, i tested with sAMAccountName but it doesn't work. Login failed.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2017 11:56 AM
If you havent already, I would recommend opening a support ticket.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-02-2017 12:26 AM
Yes, i think i must open a ticket for this case. Thanks for your help.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-10-2017 02:50 PM
Looking at the transforms in ADFS that are populating your SAML Response, you probably want to use NameID as the username attribute in your configuration on the PAN-OS side.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-15-2017 10:19 PM
Hi Benjamin,
Did you ever get this sorted out. What was the trick?
Regards, Malcolm
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-03-2017 06:38 AM
Hi Malcolm
No, it doesn't work.
I will spend more time in this task in 2-3 weeks.
It's not a high prio task for us.
regards, Benjamin
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2017 07:46 AM
Hi @benjaminsutter,
i would please like to know whether you were able to solve this problem
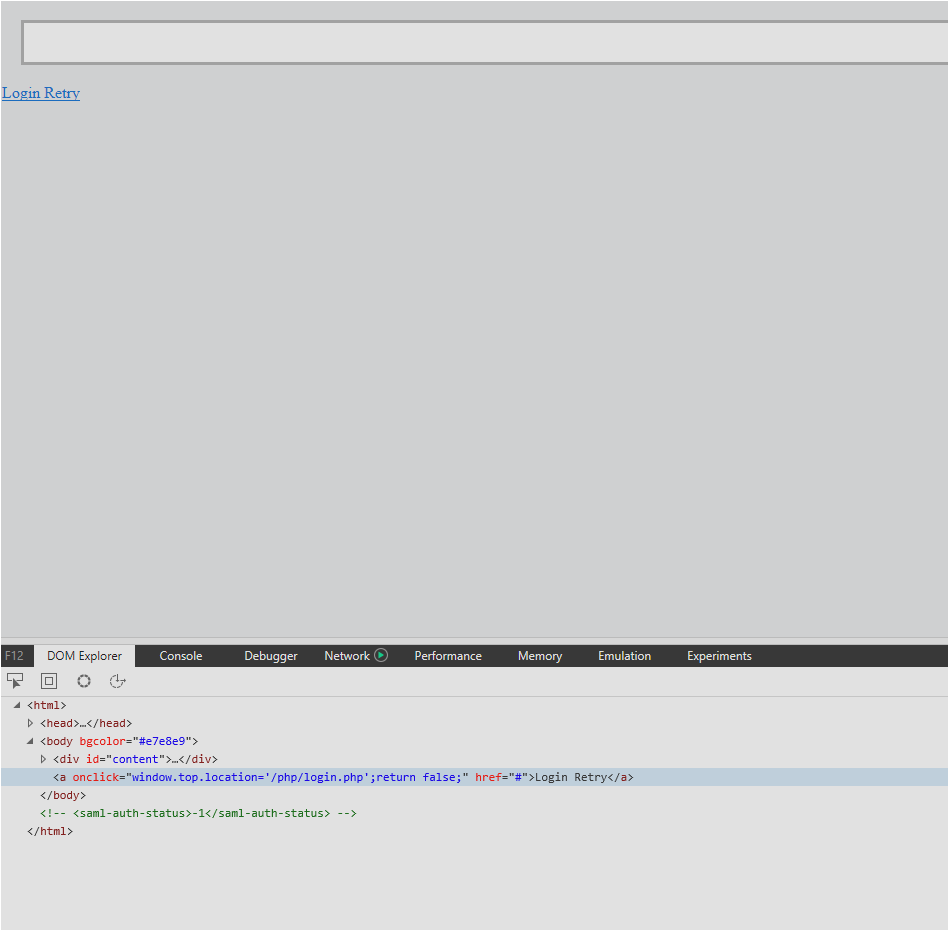
as am now facing the same Issue with SAML and AD FS (Login Retry)
I think the piece that is actually missing are Username Attribute and User group Attribute.
What parameters did you use for Username Attribute and User group Attribute?
I will deeply appreciate any hints on this matter.
kind regards,
Gilo
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2017 06:55 AM
I just recently was able to get GP to authenticate to ADFS using SAML with the help of support. Here are some hints that worked for me.
1. GP 4.0.3 has a bug, so I needed to use either GP 4.0.2 or GP 4.0.4
2. ADFS is configured with a Custom Claim Rule, a Transform rule to map SessionID to NameID (using transient identifier) and another Transform rule to map Windows Account Name to username
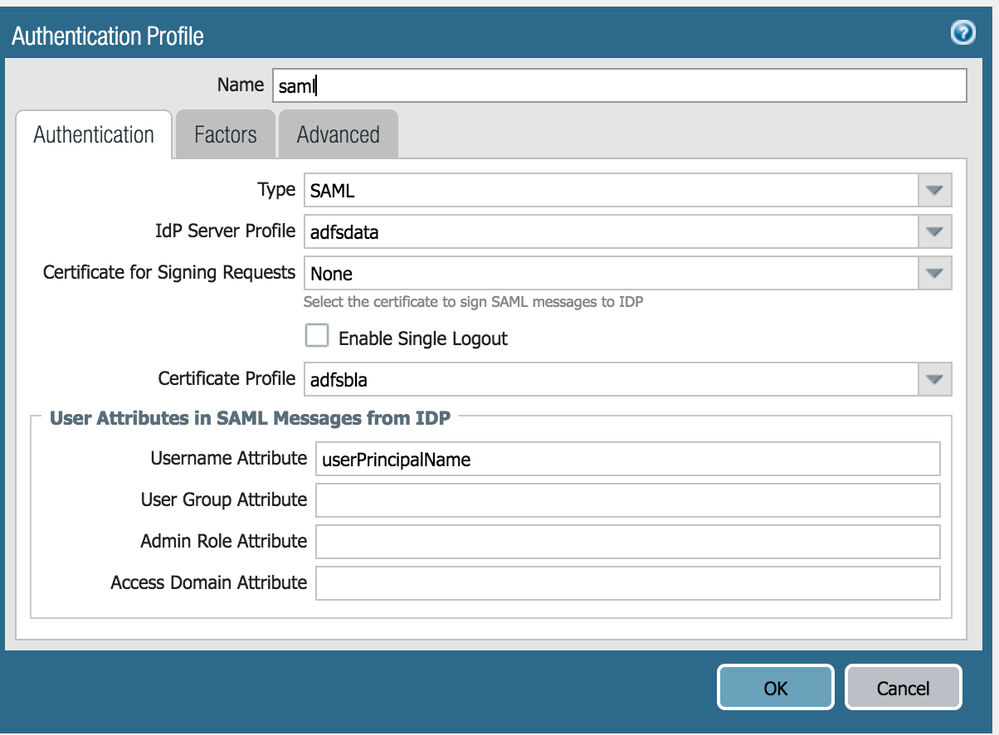
3. username is used for Username Attribute in the SAML auth profile
Let me know if that helps you.
Ian
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-03-2017 01:45 AM
Hi,
can you add a screenshot of your rules?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-10-2017 09:04 PM - edited 11-10-2017 09:55 PM
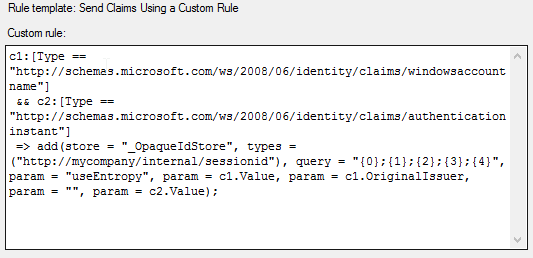
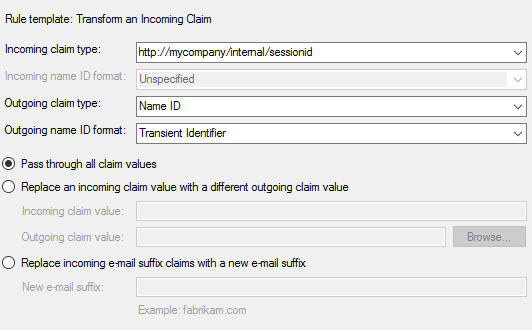
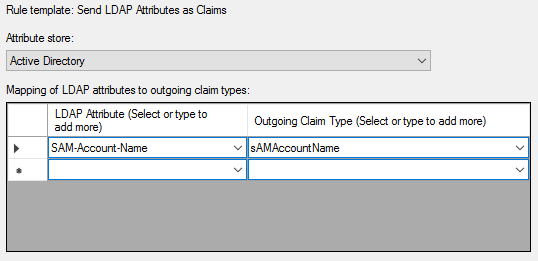
After a lot of trying I'm at the point that I can login via SAML to global protect. I'm using three rules in ADFS configuration:
1. Rule:
c1:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname"]
&& c2:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationinstant"]
=> add(store = "_OpaqueIdStore", types = ("http://mycompany/internal/sessionid"), query = "{0};{1};{2};{3};{4}", param = "useEntropy", param = c1.Value, param = c1.OriginalIssuer, param = "", param = c2.Value);2. Rule:
3. Rule:
I use sAMAccountName instead of username in my Authentication Profile.
For just logon to global protect via SAML that seems ok.
But I want to use Clientless VPN with apps that also do a SAML authentication. At the moment the situation is the following:
I open the global protect portal and get redirected to the ADFS logon site (external Form authentication). I logon and get redirected to the Clientless VPN portal.
Then I click on one app which also uses SAML authentication. I expect that the app will just open because I'm already authenticated via SAML BUT I get another ADFS authentication window (internal Windows Authentication) and have to logon again.
When I then open another app from clientless vpn portal then this works via SSO.
I think that happens because ADFS cannot map my session after I'm authenticated to the global protect portal so I think there is still missing something in the configuration of the rules.
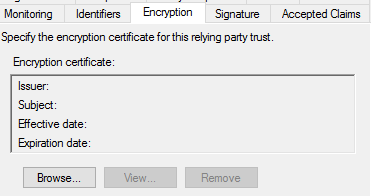
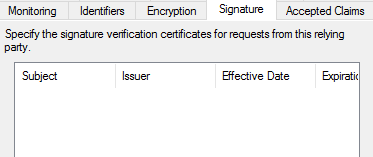
(Another information: I had to delete encryption and signature info in ADFS for the Clientless VPN party. I don't know why but I will check this later.
)
Any ideas?
Thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-13-2017 06:42 AM
I'm sorry, but I don't have any ideas for use with clientless vpn. I've only been focusing on GP. Right now I'm working through issues with the signing certificate verification and the signing of SAML requests to the iDP. Maybe my eventual findings here might help you with your last comment.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-13-2017 06:45 AM
But can you add screenshots of your ADFS rules?
Thanks!
- 13680 Views
- 15 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect Cert+SAML in GlobalProtect Discussions
- Global Protect Portal / Clientless VPN does not recognize SAML username after update to 10.1.14-h20 in GlobalProtect Discussions
- Global Protect Connectivity Issue in GlobalProtect Discussions
- [SOLVED] - NGFW The Connection To Global Protect On The IPads Times Out!! in GlobalProtect Discussions
- [Cortex XSIAM ] XDR Collector Collect Windows Security Log。XDR Collectors Administration Status display "Error". in Cortex XSIAM Discussions