- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Agentless USER-ID - rules
- LIVEcommunity
- Discussions
- General Topics
- Re: Agentless USER-ID - rules
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-14-2016 06:43 AM
Good Day
I'm testing user-id in policy-rules and its not working the way I thought it would.
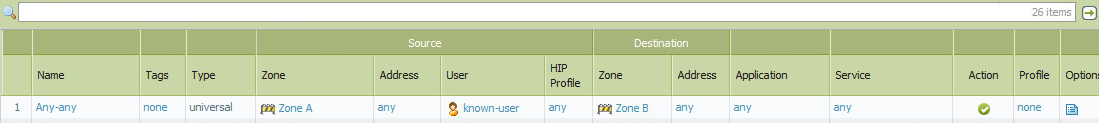
Example Rule
src zone/ip - Zone A/any
dst zone/ip - Zone B/any
user - gdc\test.user
application - any
service - application-default
action - allow
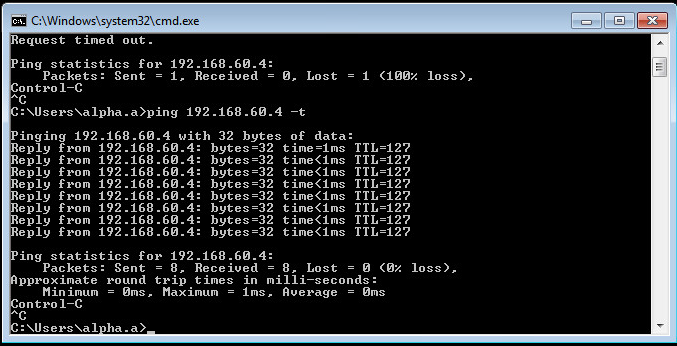
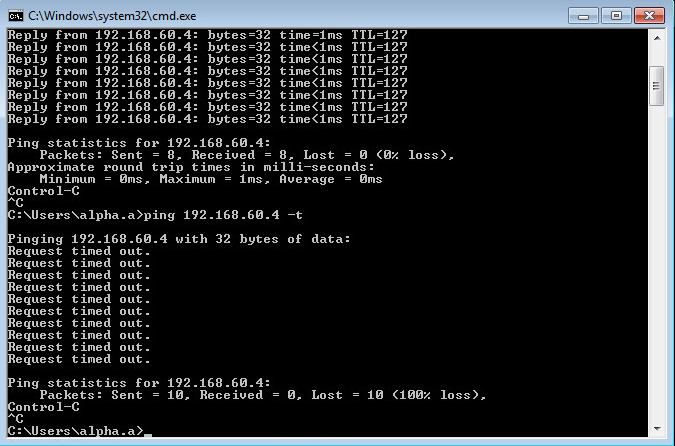
I start a ping to a server/workstation from Zone A to Zone B and I get request timeout, but if I remove the user the ping works.
This is not how I thought it would work, I thought if I'm pinging from a workstation logged in as test.user that in the rule if I added the user it would ping throw, but it isn't.
Can you tell me why this is happening?
Dana
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-14-2016 07:01 AM
have you validated that the firewall has a mapping of the IP to User?
Do you see a deny log showing the ICMP request with the source user the traffic is being generated from?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-14-2016 07:04 AM
Yes it connects to the AD brings back the userid mappings, and yes it is dropping the ICMP ping, but as I mentioned if I delete the user the ping works.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-14-2016 09:00 AM
Hello,
When you are lookigng at the logs, Click the maginifying glass on the far left and see if its picking up the username.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-14-2016 09:13 AM
When you say "it brings back the user id mappings." Does it actually provide the IP to User ID mapping for the source user in question?
In the deny log, does the denied ICMP request show the source user ID that you're expecting?
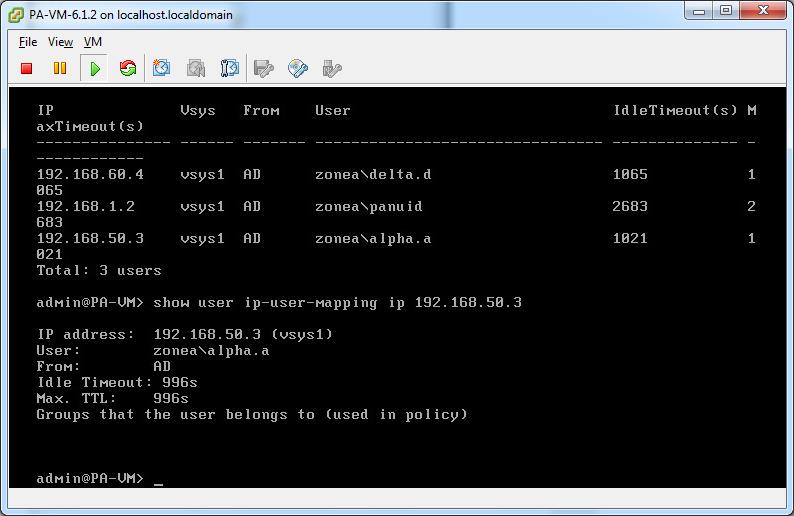
You should see something like this:
ME@FIREWALLNAME(active)> show user ip-user-mapping(mp) ip (USER IP 1.1.11)
IP address: (USER IP 1.1.1.1) (vsys1)
User: (USER ID)
From: UIA
Idle Timeout: 3371s
Max. TTL: 3371s
Groups that the user belongs to (used in policy)
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-15-2016 08:18 AM
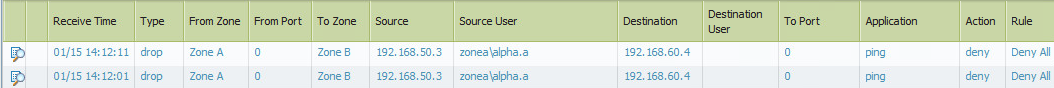
Yes I get the correct user mapping. The rule is jump and go to the deny all rule a the bottom of the rules set... which is wierd, but if I set the User tab to "known-user" it works..... but not if I choose select and put in the group.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-15-2016 08:28 AM
@burtond some screen shots might be helpful for us...Rule/Logs
Also if you're using a "group" in the rule do you have that group in the "Group Mapping?" In the user identifcation in the "Group Include List?"
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-15-2016 08:35 AM
Yes, I've even removed the User Identification setting commited and configured it again and still the same issue
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-15-2016 11:58 AM
Networking
Groups
User Mappings
User
All the groups
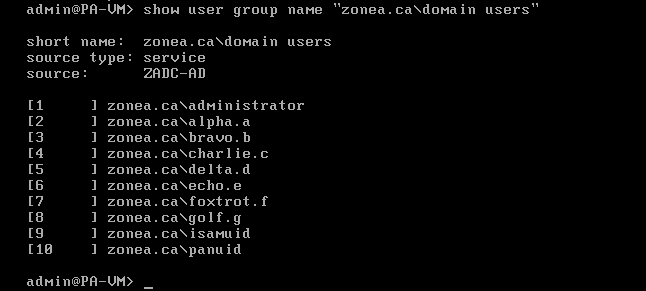
Group Domain Users
Rule that works
Ping to Zone B
Ping Allowed
Rule that doesn't work
Ping to Zone B 2
Ping dropped
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2016 11:50 PM
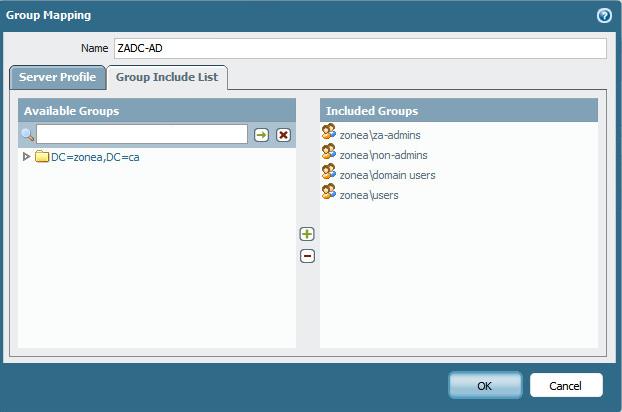
Hi
In your group mapping, the users are mapped as 'zonea.ca\user' while in the user mapping, the user is 'zonea\user'
This means the mapping information from the group is set to the FQDN while the uidagent collects the netbios domain
this causes a mismatch when your security policy is set to a group
you can resolve this issue by setting the group mapping user domain to the netbios version:
once this is committed, refresh your group mapping
> debug user-id reset group-mapping all
> debug user-id refresh group-mapping all
afterward your users should start showing up in the group listing as zonea\user1 zonea\user2 etc
hope this helps
Tom
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-18-2016 04:52 AM
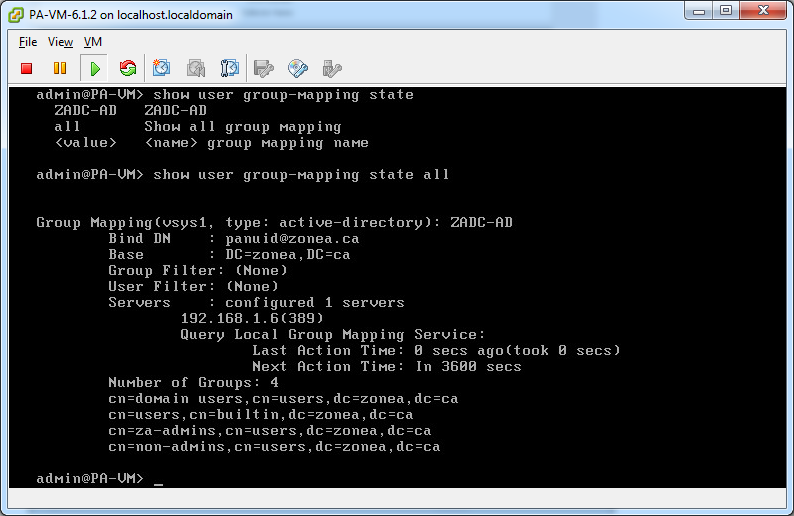
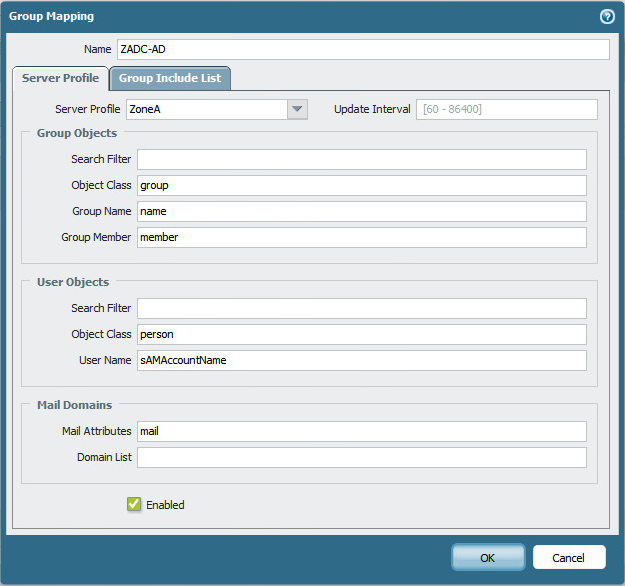
I'm running PAN-VM version 6.17 so the Group Mapping - Server Profile tab looks like this
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-18-2016 04:55 AM
I found it, it is under the Server Profile - LDAP, thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-18-2016 05:04 AM
Thanks Reaper, worked like a charm....very cool
- 1 accepted solution
- 6982 Views
- 12 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access CIE and User-ID mapping not working for groups in Prisma Access Discussions
- UserID mapping flags user unknown with single digit timeout secs in Next-Generation Firewall Discussions
- Upgrade DCs to W2019 stop working Palo Alto agentless in General Topics
- Food for Thought - Data Redistribution during HA Failover - User-ID in General Topics
- Root Partition Full in Next-Generation Firewall Discussions