- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Aruba Wireless Authentication User-IP Mapping Question
- LIVEcommunity
- Discussions
- General Topics
- Re: Aruba Wireless Authentication User-IP Mapping Question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Aruba Wireless Authentication User-IP Mapping Question
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2018 11:20 AM
Hi,
I have an Aruba Instant Cluster with an SSID set up to user a radius server to authenticate users. The cluster controller is configured to send syslog data to a Paloalto User Agent running on a Windows server. I've had this set up for a time but am now moving in to a updated OS (Windows 2016) and updated UA (8.0.10-7). My question revolves around wireless disconnects, when radius authenticated users leave the cluster or shut down their devices, I'd like the user-ip mapping to get deleted. In the syslog I get this to capture the authentication and mapping:
2018-09-26 11:12:36 Local1.Notice 10.54.132.240 Sep 26 11:12:36 2018 10.54.132.240 stm[2367]: <501199> <NOTI> <10.1.1.1 AC:A3:1E:C2:D2:9C> User authenticated, mac-a0:cc:2b:80:ad:bb, username-jsmith, IP-10.2.2.2, method-802.1x, role-PrivateSSID
But I don't see anything in the log that captures the disconnect that includes the user name. I do have this:
2018-09-26 11:13:39 Local1.Notice 10.54.132.240 Sep 26 11:13:39 2018 10.54.132.240 stm[2367]: <501217> <NOTI> <10.1.1.1 AC:A3:1E:C2:D2:9C> update_ip_mac_role_acl_vlan 15467: user entry deleted for 10.2.2.2-a0:cc:2b:80:ad:bb
But in building the syslog logoff filter in the UA GUI, it seems 'username' is required.
Anyone have suggestions on how I can build out a user agent logoff filter that can capture the wireless client disconnects?
Thanks.
Dan
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-27-2018 06:26 AM
We also have Aruba and Palo Alto, but we chose to have our wireless controllers (campus, not Instant) send syslog data directly to the firewall instead of to a Windows server. See if you can find the string 'User de-authenticated' in your controllers logs, those entries should include the user name.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2018 10:46 AM
are you using the built in user-id agent and sending the syslog data to that or are you using the API as BPry suggested above? If you're sending/using the syslog data are you doing a regex expression and might you be able to share what that looks like?
Thanks.
Dan
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2018 03:48 AM - edited 10-12-2018 05:52 AM
We are sending syslog from the controllers direct to our firewall. What you need to do is:
1. Go to Device -> User Identification and click on the Settings Button for Palo Alto Networks User-ID Agent Setup
2. Go to the tab called Syslog Filters and add the following two profiles:
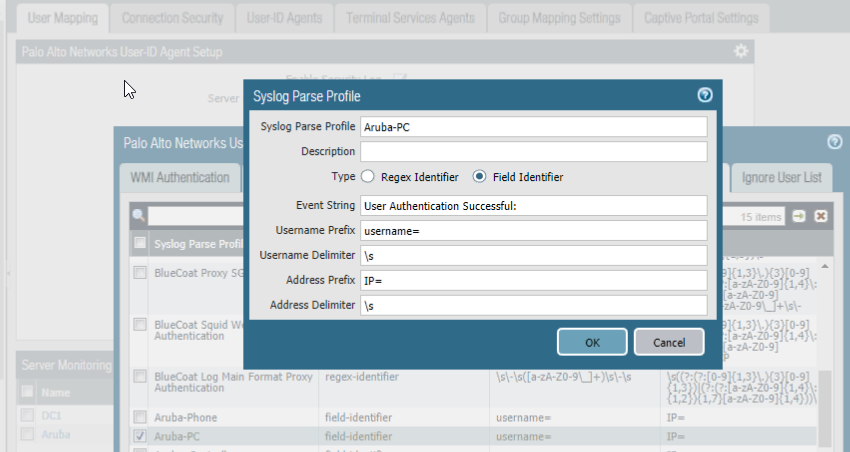
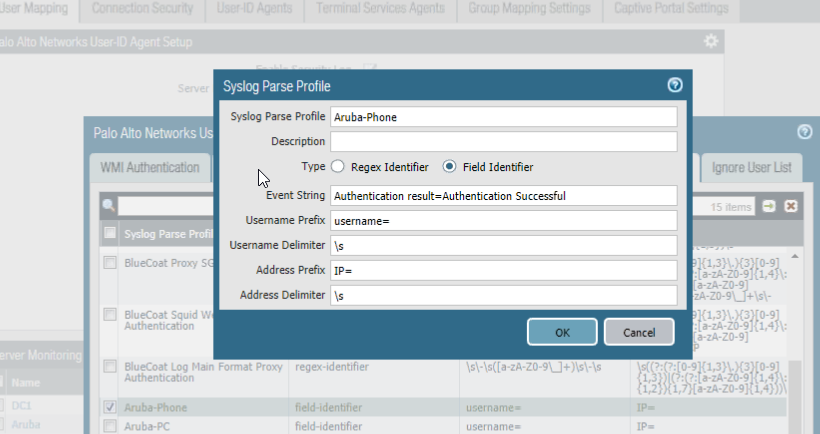
Syslog Parse Profile: Aruba Login Type: Field Identifier Event String: Authentication Successful Username Prefix: username= Username Delimiter: \s Address Prefix: IP= Address Delimiter: \s Syslog Parse Profile: Aruba Logout Type: Field Identifier Event String: User de-authenticated Username Prefix: name= Username Delimiter: \s Address Prefix: IP= Address Delimiter: \s
3. Add all your controllers and/or IAPs as Syslog Sender under Device -> User Identification -> Server Monitoring on PA. Set your AD domain as Default Domain Name and set the two Syslog Parse Profiles you added in step 2 as filter for events login and logout repsectively.
There are other steps you need to do also of course, like configure controllers/IAPs to send syslog to PA for user events. Let me know if you need more info.
PS! If I remember correctly the logout event (User de-authenticated) will be logged on controllers if the user manually disconnects from the wireless network. If the device is removed from the wireless network without disconnecting I don't think anything will be logged and the IP-user-mapping will timout on PA according to your setup.
Edit: I think support for the logout event came in PAN-OS 8. Earlier versions have only login events.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-18-2019 01:48 AM
Hi TerjeLundbo,
Please, could you post the syslog settings for an Aruba controller?
Many thanks
Andrew
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-20-2019 06:35 AM
This worked with me like a charm!
Regards,
Sharief
Sharief
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-21-2019 04:00 AM
On each wireless controller you need to enable logging of user authentications and you need to send each authentication event as syslog to the firewall. Commands are:
logging level notifications user process authmgr
logging <FW IP address> type user severity notifications facility local1 source-interface <mgmt vlan of the controller>
- 12743 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PAC Retention and URL Category Priority Behavior in Prisma Access in Strata Cloud Manager
- Why do the same Windows Server data collected using XDRC and WEC agents show different statuses in the following fields? in Cortex XSIAM Discussions
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- CIE for user/group mapping for firewall on-premise in General Topics
- PA-450 and ATT BGW320-505 in General Topics