- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Best practices for implementing access to Office 365?
- LIVEcommunity
- Discussions
- General Topics
- Best practices for implementing access to Office 365?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Best practices for implementing access to Office 365?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2013 12:58 PM
Does PAN offer any formal guidance for implementing access to Office 365, specifically for Outlook access to Exchange Online?
We have, via trial-and-error, enabled this access using the newly-minted AppID for Office 365, but are seeing occasional Outlook session disconnects.
Microsoft is, predictably, telling us that none of their other customers see this problem, and are vaguely suggesting it's our firewall.
Does Palo Alto Networks have any recommendations on how to best enable Exchange Online? Anyone have any positive experiences to share? (I can also share some of our pains in reverse-engineering the O365 service, if there is interest...)
Thanks!
- Labels:
-
App-ID
-
Configuration
-
Set Up
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2013 01:34 PM
Hello,
A quick suggestion I would give here is to first make the rules simple between the source and destination and allow the traffic to pass properly and completely as expected.
Now if monitor Traffic logs for this period of testing ( Filter traffic for security rule, time frame of the event tested, source and destination IPs ) we would find all the apps seen on the PAN and all the ports which allowed the traffic.
If some of these ports or apps were missed that would narrow down the issue for us.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2013 03:28 PM
Hello KGC,
You can get more information about the application on Application Research Center in order to get more control over traffic.
Detailed information about dependent applications etc. And accordingly you can configure the PAN firewall.
Example:
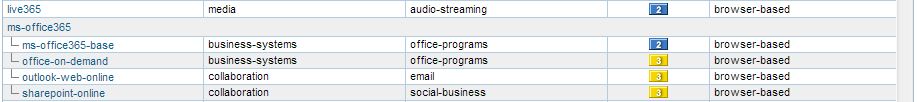
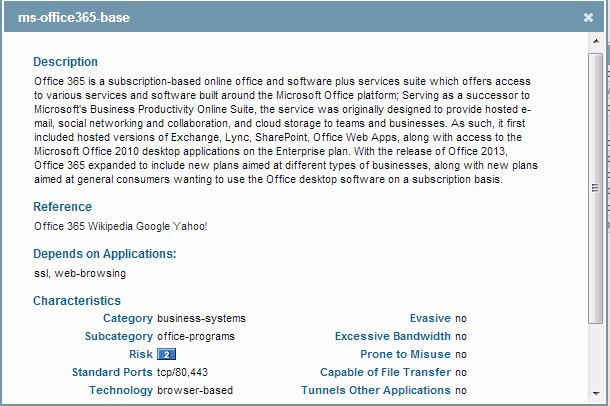
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2013 08:43 AM
Did you just starting seeing the issue after the app-id's were created. Also verify that no session is being denied for the ports or apps that are needed for the application.
While you are having issue you can do the following to narrow down the issue.
1. Need to setup the filters for the traffic we are interested in. To do this, execute the following steps:
Navigate to Monitor--Packet Capture
Click 'Manage Filters'
Set Filter ID 1 to be the source IP and destination IP of traffic you feel is affected ( leave all other fields blank )
Set Filter ID 2 to be the exact inverse of what you did in step 3 (destination IP in source field, Source IP in destination field)
2. Setup up the captures
Create and name the file stage for a packet capture on all the stages (receive, transmit, firewall and drop)
3. Enable filters and captures
debug dataplane packet-diag set filter on
debug dataplane packet-diag set capture on
4. open 2 CLI windows
on 1 run the following command to look at the counter ( make sure it run this command once before running the traffic)
show counter global filter packet-filter yes delta yes
on the 2nd window run the following command to look at he sessions
show session all filter source <ip address> destination <ip address>
After your test has been done stop all the captures and filters and see if global counter show you anything why it is dropping the traffic or if you have getting pcap with drop stage.
This will help you narrow down the issue.
Let us know if this helps you resolve the issue.
Thanks
Numan
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-01-2013 02:03 PM
These are all great suggestions in general for simple straightforward applications, however the way MS implements Exchange Online is anything but simple or predictable. I will try to address these individually:
- Challenge with packet capture method: the sessions are sometimes very long, lasting hours if not days, generating massive amount of data. Besides, I am pretty sure that PAN identifies the application correctly. The disconnects look just like a normal finished TCP session, there are no denys in the logs.
- Challenge with watching traffic between source and destination: what is the destination? MS publishes lists of public IPs which are supposed to correspond to the various cloud services they offer, however these lists are not well-maintained and change rapidly. Some of the MS cloud addresses are on a 2-min TTL. We also observed a number of IPs serving Exchange Online which were outside the published ranges.
- Challenge with allowing all traffic and then narrowing it down to just the application: MS serves a lot of different products on the same IPs and ports, including some we do not want to enable (e.g. Sharepoint Online, aka SkyDrivePro.) The AppID is really the best and only effective way to enable just the app you want.
For the most part we have the service enabled, however there are still some minor challenges (e.g. occasional disconnects) which is why I was hoping that PAN offered a formal tested and recommended guide for implementing O365.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-13-2016 12:11 PM
Some good info here. We are getting ready to configure some security policies and I was hoping to see how others were handling it.
One of my thoughts was / is ....
Well we are getting ready to implement Panorama, so I was thinking that we could setup a global rule that is application based and then a local rule that is URL based, then monitor traffic and see which way is the most effective.
- 10115 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Scanning for Misconfigured Endpoints in Cortex XDR in General Topics
- globalprotect client VPN - Nat rules in Next-Generation Firewall Discussions
- Blocking PowerShell While Allowing Certain Powershell Scripts in Cortex XDR Discussions
- Need Help on Configuring GlobalProtect VPN in GlobalProtect Discussions



