- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Can't join Windows Updates server, application "not applicable"
- LIVEcommunity
- Discussions
- General Topics
- Re: Can't join Windows Updates server, application "not applicable"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 02:04 AM
Hi !
I'm trying to connect the server to the Internet in order to download and to install updates. My server is a Windows Server 2016, so i'm trying to reach Windows Updates servers.
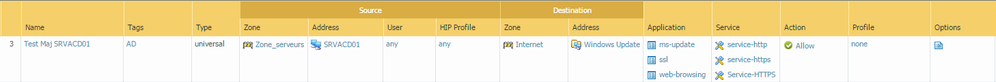
In order to do that, I created a rule in the firewall :
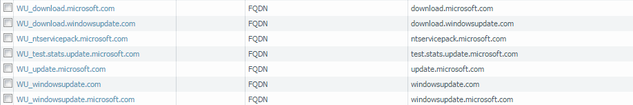
The address group contain theses addresses :
To verifiy that my server can reach Windows Update server, I checked the logs.
I've got in Application field "not applicable" :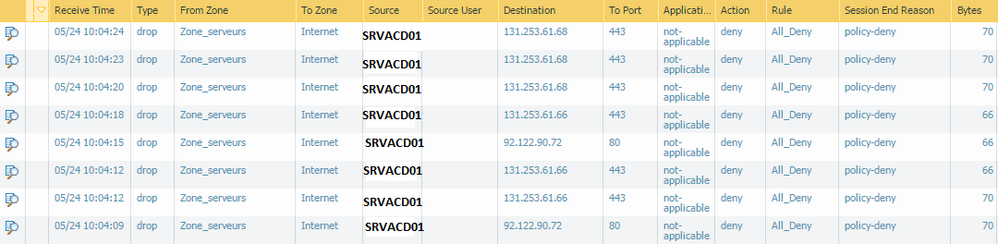
Support says : "Not-applicable means that the Palo Alto device has received data that will be discarded because the port or service that the traffic is coming in on is not allowed, or there is no rule or policy allowing that port or service"
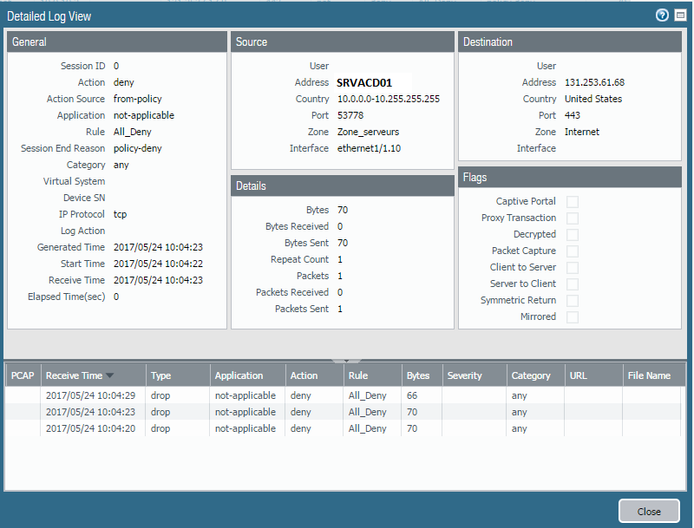
Here is an example of a detailed log :
Do you have any idea to solve the problem ?
Best regards,
Alexandre
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 02:37 AM
Those sessions' destination IPs are not matching the FQDN objects you created so the connection bypasses the security policy and hits the deny_all instead.
At this point, APP-ID is not going to try and identify the application (as the session is getting discarded by policy anyway) so the app is labeled as not applicable
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 02:27 AM
Your traffic is not hitting your policy. Instead it is hitting All_Deny rule
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 02:37 AM
Those sessions' destination IPs are not matching the FQDN objects you created so the connection bypasses the security policy and hits the deny_all instead.
At this point, APP-ID is not going to try and identify the application (as the session is getting discarded by policy anyway) so the app is labeled as not applicable
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 02:40 AM
Taking "off" FQDNs from the policy should allow you to get updates.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 02:46 AM
You could use a custom URL category where you enter the fqdn's which you now have configured as address objects. After that remove all the address objects from your security policy and add the custom URL category to this rule. (no URL filtering license required)
This way it should be able to limit the access to only the Microsoft Update Servers while not having problems with FQDN objects (where it is, specially with CDN's, likely that the firewall does not resolve the FQDN to the same ip as your internal server)
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 02:53 AM
Thanks all. It was FQDN the problem !
I will create addresses object, and I will see what IP are used, to modify the rule.
Have a good day ! Thanks !
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 03:38 AM
In this case I would not recommend doing that. Create the rule either only application based as @TranceforLife proposed or limit it by using a custom URL category.
But because Microsoft distributes the updates with a CDN you will most likely end up with often changing your security policy (adding new ip's regularly; deleting old ones; and not to forget to troubleshoot everytime to find out which ip really belongs to this FQDN's and which ones are just traffic you don't want to allow)
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 03:56 AM - edited 05-24-2017 04:22 AM
Hey,
Totally agreed. Anyway, sometimes FQDNs just simply fail to refresh.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 06:10 AM
So I created an URL category, and it works ! I have "deny" for some IP, but I can have updates !
Thanks all !
- 1 accepted solution
- 6127 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Outlook and mapi-over-http in General Topics
- Windows-Remote-Management & Implicit Use of Web-Browsing in General Topics
- New articles about how to create signatures without or with AI (ChatGPT/OpenAI) in Custom Signatures
- Security Policy with Destination Criteria in Strata Cloud Manager
- Detect RC4 traffic in Strata Logging Service Discussions