- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Cant deny users from using remote desktop on non standard tcp port
- LIVEcommunity
- Discussions
- General Topics
- Re: Cant deny users from using remote desktop on non standard tcp port
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Cant deny users from using remote desktop on non standard tcp port
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-02-2019 08:09 AM - edited 01-02-2019 08:10 AM
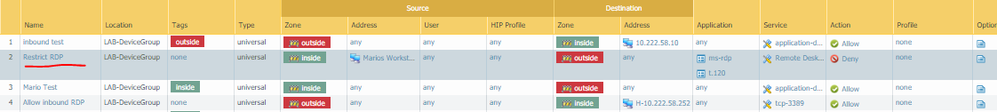
I am trying test app id & put a rule in (all the way on top) denying my work station from accessing RDP on machines in other zones. I have successfully blocked users from accessing RDP on standard port 3389 but can still access RDP on a machine that listens for RDP on a non standard port (tcp 51000). I did not specify the non standard port in the security policy like I did port 3389 but I did use app ID in the rule for "ms-rdp" and "t.120" and expected the app ID feature to catch the connection and deny it. What am I missing & why wont the PA deny the RDP connection using app ID on the non standard tcp port?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-02-2019 08:33 AM
your rule is set explicitly for port 3389. it doesn't matter what you have in any other of the boxes as it has to match 3389.
can you monitor the allowed traffic on port 51000, is it recognised as ms-rdp.
if not then you will have to rethink your policy but as it stands it can be either ms-rdp or t.120 but must be 3389 to be denied.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-02-2019 02:50 PM
You have to change Service field to "Any" to block ms-rdp on any port.
Palo Alto Networks certified from 2011
- 3197 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Windows-Remote-Management & Implicit Use of Web-Browsing in General Topics
- False positive (generic.ml): HelpDesk Viewer in VirusTotal
- On-Boarding of Cisco SDWAN to Prisma in Prisma Access Discussions
- Clientless VPN and Remote Desktop in Next-Generation Firewall Discussions
- False Positive: HelpDesk Viewer in VirusTotal