- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
commit status warning on rules that are working the way I want them too
- LIVEcommunity
- Discussions
- General Topics
- commit status warning on rules that are working the way I want them too
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
commit status warning on rules that are working the way I want them too
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 08:48 AM
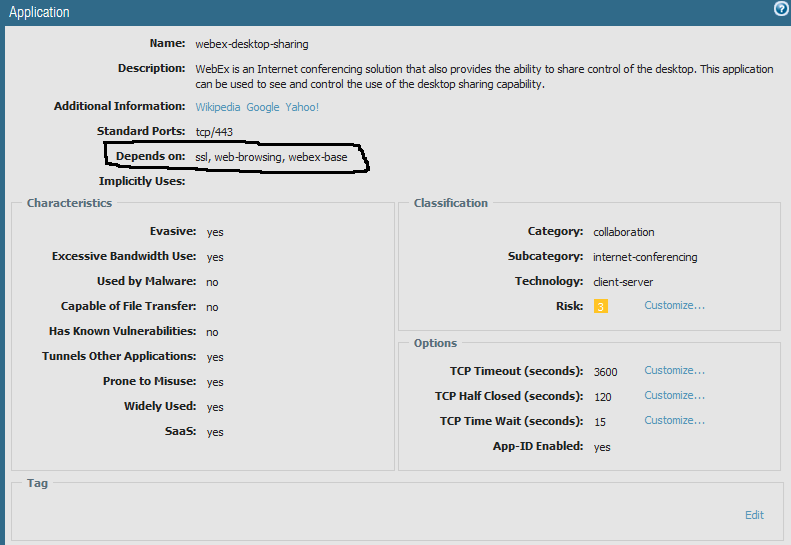
I have a rule that has webex enabled but dones not have ssl enabled and i keep getting a warning on that rule when i commit that says "Applicaiton 'webex-desktop-sharing requires ssl be allowed? But I don't want to allow ssl, so how can I get rid of these warnings so i can tell when i have a legitimate commit warning?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 09:09 AM
I hope there is a solution but I asume there isn't ... some applications simply have a dependency to others. So even if it works in most cases there might be some edge cases where the firewall first sees ssl and after some more packets thw app changes to webex. So in these cases it could be that it won't work with allowing only webex...
Hopefully there is a way, cause the commit warnings I have are growing and growing ...
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 09:09 AM
ssl is a dependency of the webex desktop sharing application...
according to this doc... https://live.paloaltonetworks.com/t5/Learning-Articles/Tips-amp-Tricks-What-is-Application-Dependenc...
it states...
If you do not allow the application and its dependency through the Palo Alto Networks firewall, then the application will not work.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 09:10 AM
sorry, answered after @Remo...
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 09:20 AM - edited 03-29-2018 09:27 AM
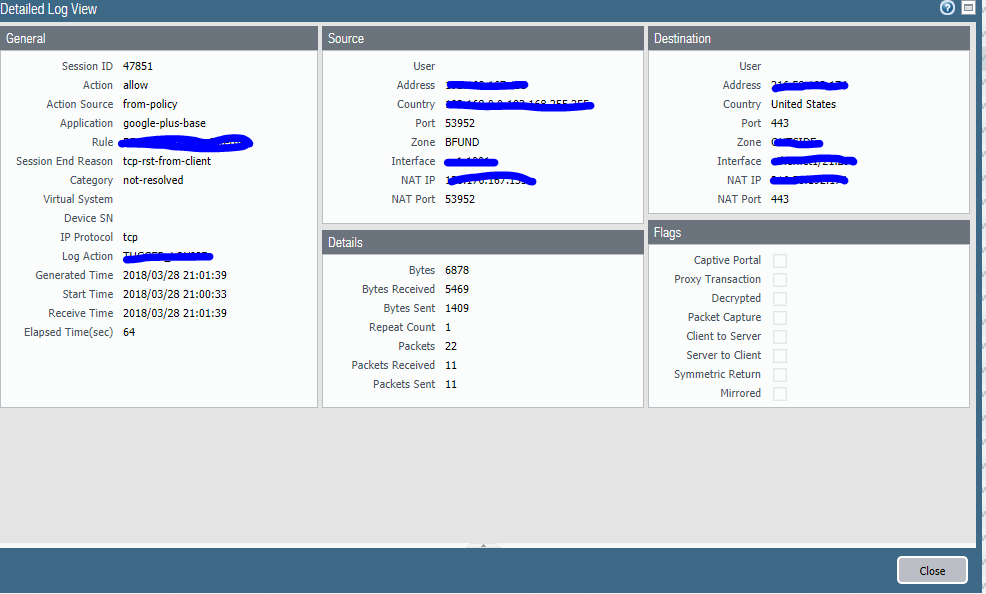
thing is it does work and I would think it shouldn't , for instance this is in the commit warning
- Application 'google-plus-base' requires 'google-base' be allowed
And this is what it says in the applicatiion info - google-play standard ports 443,5227,80,tcp,udp
Then I look in the traffic and unless I am reading this wrong it is work even though ssl is not allowed so to speak
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 09:28 AM
I know it works, thats why I have endless commit warnings 😛
Exactly like your initial example. You only want to allow webex but not general ssl access to everywhere ...
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 09:30 AM - edited 03-29-2018 09:32 AM
Yeah and the impression from the commit warning is that it should not work without ssl but it does, because the ssl port 443 is allowed, from what I see
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 09:53 AM
So I guess I want away to clean up my commit status errors without having to add ssl to a rule that I don't want ssl enabled on.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 09:54 AM
ok so having added the dependencies to the webex desktop sharing policy, the warnings have gone...
is this a problem, will it not only use these dependencies for webex desktop and nothing else...
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 09:57 AM
I know that giving it what it wants to make the commit status errors go away but I don't want ssl on those rules at all
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 10:08 AM
No, if you add these dependencies then the firewall also allows these apps independently.
So ...
- Allowing just webex --> working solution but commit warning
- Allowing webex with dependencies --> webex works but also general webaccess and the commit warning is gone
Or ...
- Secure solution --> commit warning
- Insecure solution --> no commit warning
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 11:09 AM
@jdprovine, @Remo. Sorry... its been a long day.... i feel so stupid.
i thougt i was adding the dependencies into a different section of the policy, not into the same app section of the policy as webex desktop...
i feel this will not be marked as a solution.....
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2018 11:57 AM
OK, we see this all the time. One thing to keep in mind is the application/traffic may work without the dependencies *but* some components of it may not work and you may not notice or the app may fall back onto something else if it fails one piece.
Here is what we try to do and a lot of people forget they can do this:
* Setup your security policy and add the dependencies
* validate the commit does not have any dependenciy warnings
* Scope the policy down to specific destinations (if possible) or use a URL category in the policy, using a URL category will at least make it so users will not hit this policy for all web browsing and hopefully only hit it for the application/URL catgories specified
for example we have exceptions to allow people to hit online file storage junk (box, dropbox,etc) so aside from the user having to be in the proper AD group for the exception the destination also has to be one related to the exception and/or the URL category has to match, otherwise they will hit the standard web traffic policy.
the web-browsing and ssl applications will be a pain no matter what (try locking down slack and have fun)
- 10702 Views
- 40 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Struggling to Unset Virtual Router from Interface via API – Manual Works, API Always Fails in General Topics
- SCM IOT device details not showing Utilization tab in Strata Cloud Manager
- How to Get All Filter Parameters for Cortex XDR Incident or Alerts URL? in Cortex XDR Discussions
- Redistribution UIA not working...... INTERNAL ERROR in General Topics
- TACACS authentication with Cisco ISE not working in General Topics