- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Configuring XFF logging without a URL Filtering License
- LIVEcommunity
- Discussions
- General Topics
- Re: Configuring XFF logging without a URL Filtering License
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Configuring XFF logging without a URL Filtering License
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-15-2018
07:27 AM
- last edited on
12-06-2018
12:59 AM
by
![]() reaper
reaper
1. Create a Custom URL Category with * under ‘sites’ (Objects >> Custom Objects >> URL Category >> Add)
2. Create a URL Filtering Profile & set your Custom Category action to “alert” (Objects >> Security Profiles >> URL Filtering >> Add)
Tick the box to log XFF on the ‘URL Filtering Settings’ tab…
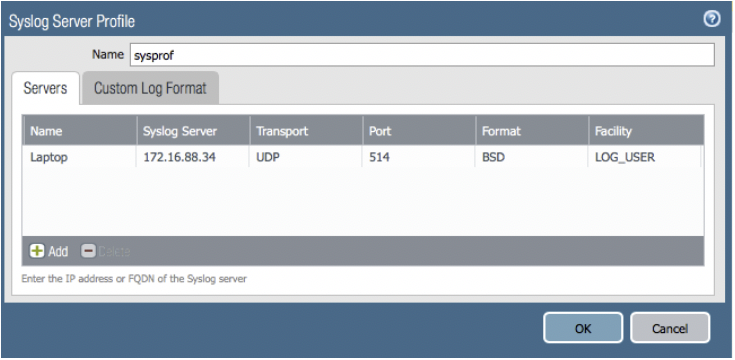
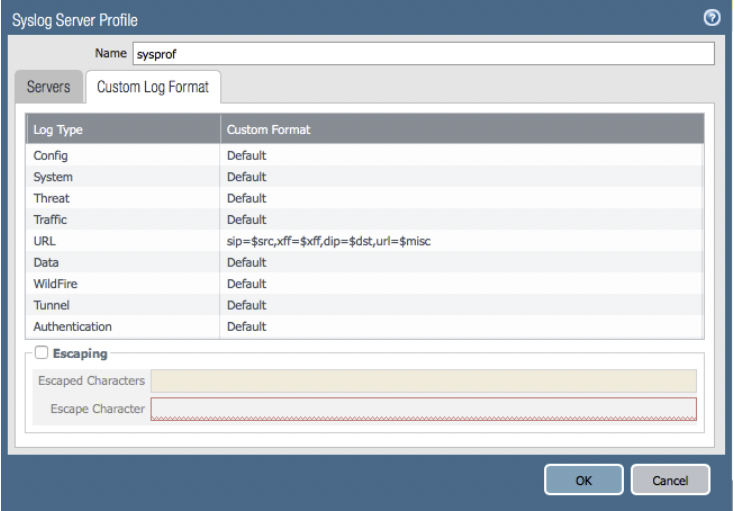
3. Create a syslog server profile & modify the custom log format settings for URL (Device >> Server Profiles >> Syslog >> Add)
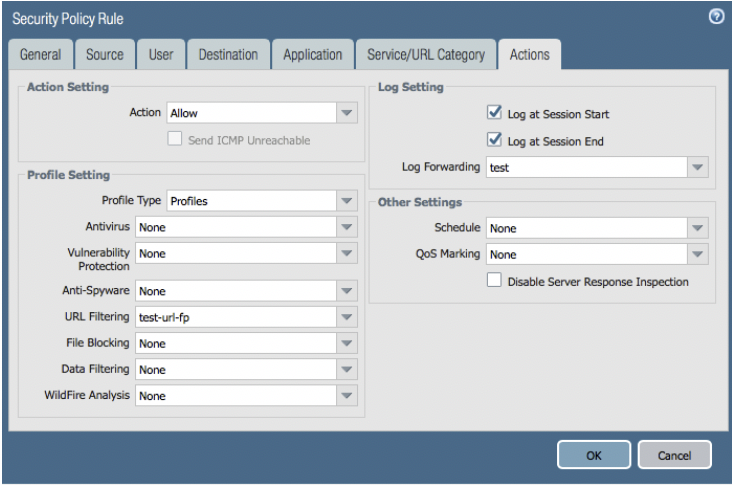
4. Create a Log Forwarding Profile & point it at your syslog server (Objects >> Log Forwarding >> Add)
Make sure your Log Type is ‘url’…
5. Apply both the URL Filtering & Log Forwarding Profiles to your Security Policy rules (Policies >> Security)
6. Commit your configuration, and observe this expected warning message
7. To test, you can use a free extension to Firefox called “Modify Header Value (HTTP Headers) by Milen Monrov. Type ‘about:addons’, click on ‘More’ & scroll down. You will have an opportunity to setup a header insertion rule like I have…
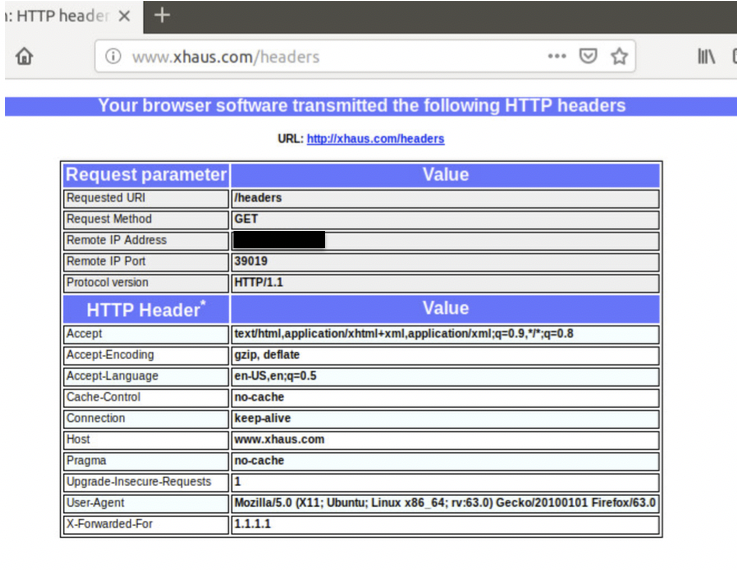
If I scroll to the right, you can see I am inserting a value of 1.1.1.1…
8. Pick a cleartext site against which you can validate that the header insertion is working (I use http://www.xhaus.com/headers)
9. Validate that the log data being sent by the firewall includes your expected values (ultimately this will match the string setting from step #3 above, which in my case is sip=$src,xff=$xff,dip=$dst,url=$misc). you can apply the wireshark display filter 'syslog' to match only what we are after...
NOTE: Your browser will likely be sending traffic in the background that does not fire the XFF extension tool (safe browsing, etc.). Do not be alarmed if this type of traffic does not display an XFF value.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-10-2018 11:29 PM
Great artical! Very useful.
One small note - on step 6 I believe you got the wrong screenshot. I guess you wanted to should the warning for the no valid URL filtering during commit?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-30-2018 12:57 PM
To prevent additional information leakage of the IP address, you should enable this option (Device>Setup>Content-ID>X-Forwarder-for Headers):
- 8283 Views
- 2 replies
- 4 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- When will the Legacy URL Filtering license be transitioned to the A-URL license? in Advanced URL Filtering Discussions
- About the output of the "show ctd-agent status security-client" command in Next-Generation Firewall Discussions
- AWS sites categorized as "unknown" in URL filtering logs and blocked in Advanced URL Filtering Discussions
- Newsletter: Cloud Delivered Security Services, Aug-Sep, 2025 in Advanced WildFire Discussions
- PA outbound security policy - Terraform to AWS console in Next-Generation Firewall Discussions