- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Decryption issue
- LIVEcommunity
- Discussions
- General Topics
- Decryption issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2021 11:51 AM
We have outbound decryption working but there are few sites that popup that donot work from time to time and have to add the to exceptions.
I am trying to investigate a recently highlighted website and to learn how to troubleshoot this better.
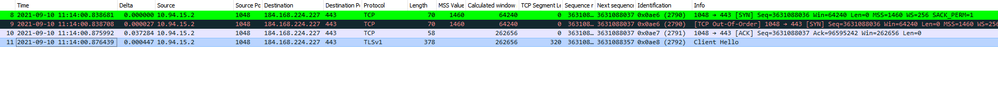
If I run this openssl command connection on the client is successful and wireshark output looks like this and client sees server hello.
-----------------------------------------------
.\openssl s_client -connect windowstechpro.com:443 -brief
depth=3 DC = ca, DC = abcdef, DC = abc, CN = ABC DEF - Root CA
verify error:num=19:self signed certificate in certificate chain
CONNECTION ESTABLISHED
Protocol version: TLSv1.2
Ciphersuite: ECDHE-RSA-AES128-SHA256
Peer certificate: CN = *.windowstechpro.com
Hash used: SHA256
Signature type: RSA
Verification error: self signed certificate in certificate chain
Server Temp Key: ECDH, P-384, 384 bits
-----------------------------------------------
but on PA capture looks like this.
When trying to open the website in browser in firefox it shows PR_END_OF_FILE_ERROR & in chrome "windowstechpro.com unexpectedly closed the connection."
On client wireshark shows like this and client never receives a server hello.
Firewall still looks the same
Profile settings
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2021 02:33 PM
Hello there.
Suggestions I have (not that I am fixing issue, but trying to understand what can/cannot be done)
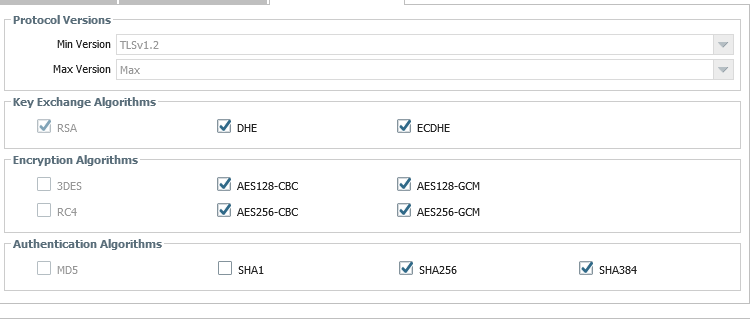
Go into your Decryption Profile and set the TLS to 1.2 to 1.2 (and not MAX)
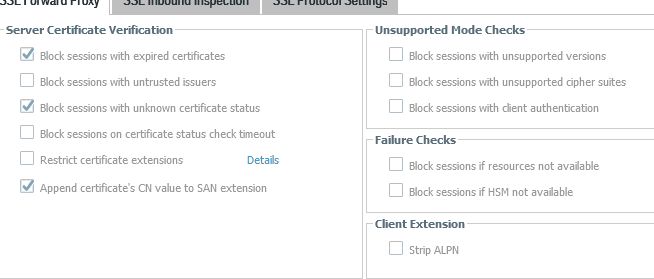
While in the profile (for tshooting only), uncheck the 3 checkmarks/boxes under Server Certificate Verification.
You should also look at the Traffic Logs for that specific session and provide the End Session Reason (was it tcp-reset-server or client, threat, decryption error, etc).
We need more information. It is possible that the site just cannot be decrypted and needs to have an exception generated for it. There are some limitations to how the server certificates are generated (think certificate key pinning or hair pinning) that could generate similar results.
Good luck and let us know.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2021 02:33 PM
Hello there.
Suggestions I have (not that I am fixing issue, but trying to understand what can/cannot be done)
Go into your Decryption Profile and set the TLS to 1.2 to 1.2 (and not MAX)
While in the profile (for tshooting only), uncheck the 3 checkmarks/boxes under Server Certificate Verification.
You should also look at the Traffic Logs for that specific session and provide the End Session Reason (was it tcp-reset-server or client, threat, decryption error, etc).
We need more information. It is possible that the site just cannot be decrypted and needs to have an exception generated for it. There are some limitations to how the server certificates are generated (think certificate key pinning or hair pinning) that could generate similar results.
Good luck and let us know.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2021 10:16 AM - edited 09-13-2021 10:32 AM
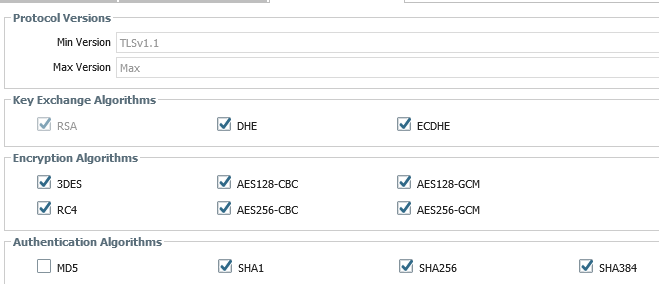
@S.Cantwell I had not done basic troubleshooting and straightaway went for packet captures. Couple of websites I know that were recently highlighted both worked after I broadened the scope of TLS and set minimum to 1.1 with less preferable algorithms.
I still want to ask what was the rational behind behind suggesting to set max version to 1.2 instead of max, doesn't both mean the same as 1.3 is not supported.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2021 02:57 PM
So, what I understand, based on your settings, is that you have Users or Servers on the internet, that are not following the recommended patch releases to deprecate TLS 1.1 and lower. In Feb/March 2020, the 3 big browser companies (Microsoft, Mozilla, Google) agreed to DEPRECATE support for TLS 1.0 and 1.1. Today's modern browsers support TLS 1.2 and 1.3.
You have run into a situation where the WEBSITE on the Internet is NOT TLS 1.2. It seems to not have been patched to deprecate support for TLS 1.0 and 1.1. So you needed to modify your security configuration to allow 1.1.
You should create 2 decryption profiles. One that support TLS 1.2 to 1.2, and then other one, for this specific destination server, to use this (not recommended) profile of TLS 1.1.
As for my suggestion about TLS 1.3 As I just explained.. the FW CAN support TLS 1.3... but if the Website does NOT.. then you will have problems with decryption, because of TLS mismatch. TLS 1.3 can be backward compatible to TLS 1.2. So... on the off chance a TLS 1.3 server talks to to a TLS 1.2 end point, your FW can allow the traffic. It is just a recommendation from PANW.
- 1 accepted solution
- 6304 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex XDR 8.9 Non-Persistent Citrix Servers and Cache Write Issue in Cortex XDR Discussions
- Windows Installer DB: Current agent installation is missing in Cortex XDR Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- About PAN-183404 in Next-Generation Firewall Discussions
- About PAN-293673 in Next-Generation Firewall Discussions