- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Disable SSL - IPSEC only
- LIVEcommunity
- Discussions
- General Topics
- Re: Disable SSL - IPSEC only
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Disable SSL - IPSEC only
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-23-2014 06:31 AM
Hi,
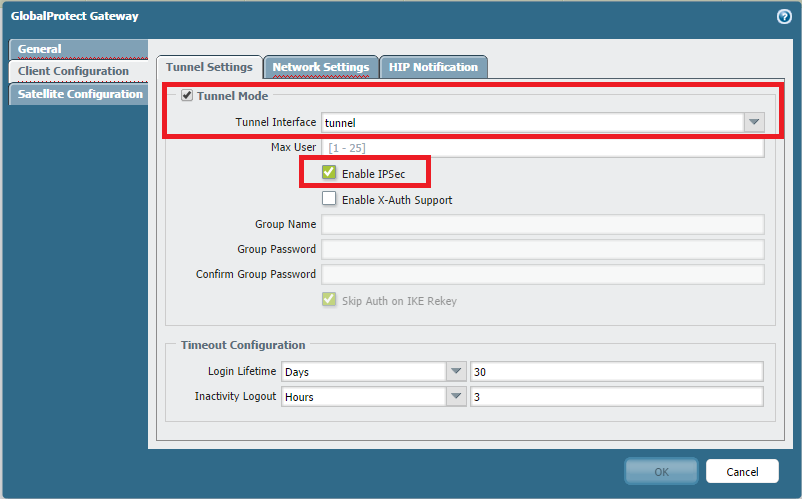
a quick one: is it possible to disable SSL VPN at GP? So users can only connect via IPSEC...
I know its possible to do it the other way but we like to have a IPSEC only portal/gateway.
- Labels:
-
Configuration
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-23-2014 06:38 AM
thanks,
I know, but the failover mechanism is still active (if IPSEC fails, GP is trying to connect via SSL).
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-23-2014 06:40 AM
Hi Hithead,
Than you can block SSL for Gateway IP address in Policy. That way failover will not take place in reality.
This will work only if portal is on another firewall.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-23-2014 06:48 AM
Hi Hithead,
Let me know if this helps, there is no inbuilt way or command to disable SSL.
I didnt find any existing Feature Request to disable SSL, I would suggest to contact Sales Engineer to open new Feature Request.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-23-2014 06:55 AM
Hi hshah,
Portal = Gateway in our installations. So not possible.
Will contact SE for a feature request. Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-23-2014 07:36 AM
only way for now, just to create GP , GW config(empty portal config) and make clients connect with cisco client,ort etc.instead of GP client.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-23-2014 11:53 AM
Hi HitHead,
In that case you can assign loopback IP to Portal and loopback should be part of untrust network.
Now you car restrict traffic on Gateway.
Let me know if thats a good work around.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2014 01:15 AM
sorry but how should that work?
(We have one public IP (gateway = portal) NATed to the Portal. At the Portal we configured the public DNS as gateway for the client config.)
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2014 01:27 AM
Do you have any free public IP from the pool. That can be configured on Loopback.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2014 01:43 AM
No sadly not.
But I really like to know, how the loopback config works...
As I know, we have to authenticate at the Portal and Gateway with SSL (client certificate authentication). So I have to open (and NAT) SSL to the Portal/Gateway IP (IP is the same; private range).
So, and if the Portal IP is the loopback interface in a untrusted zone and my client gets the IP or DNS name of the gateway from the portal, SSL is still required for the authentication at the gateway. SSL is still open. - Hope its clear enough...? Understood my concern?
THX
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2014 01:02 AM
HULK,
your answer is helpful but please correct me if I'm wrong or misunderstand the configuration:
Fist, a citation: " This request can be received either by Split tunnel on the physical interface ethernet 1/1, or by Full tunnel on the loopback interface by NATing 88.88.88.88:4501 to 1.1.1.1:4501. Both Split and Full tunnel cannot receive the IPSec request."
If I will configure our Portal/Gateway with the loopback solution, the authentication against the gateway is still necessary with SSL (port doesn't matter). Ok, my clients will connect with IPSEC but the SSL failover mechanism configured at the agent is still enable and also possible, because you have to authenticate against the gateway with SSL.
So in my opinion there is no way to disable a SSL tunnel, because of the SSL failover mechanism and authentication against the gateway.
Please correct me, if I'm wrong!
- 10116 Views
- 12 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Clone Rule as Disabled in General Topics
- Need help uninstalling Cortex XDR in General Topics
- Tuning Panorama HA Timers to Stop False HA1 Alerts over MPLS in Panorama Discussions
- Stealth Rule Question in Next-Generation Firewall Discussions
- global protect connection failed authentication failed !!! in GlobalProtect Discussions