- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
DNS tunneling seems it's not recognized as "tcp-over-dns"
- LIVEcommunity
- Discussions
- General Topics
- DNS tunneling seems it's not recognized as "tcp-over-dns"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
DNS tunneling seems it's not recognized as "tcp-over-dns"
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-23-2016 12:46 AM
Since some weeks, we are suspecting DNS Tunneling usage.
We saw a specific "application" being present on applipedia for this kind of action: tcp-over-dns
Applipedia description states:
"DNS Tunneling is a technique to encapsulate any binary data within DNS queries and replies and tunnel it to any remote system and the Internet. There are several tools currently available on the Internet that perform DNS tunneling. This application identifies traffic from the following tools, tcp-over-dns, dns2tcp, Iodine, Heyoka, OzymanDNS, and NSTX."
But on our firewall with PAN-os version 6.0.9 we did not find that application "recognized":
a) from suspected networks we do not find any "tcp-over-dns" reference inside logs (only plain "dns")
b) explicitly testing from a PC behind our firewall with both "dns2tcp" and "Iodine" tools no "tcp-over-dns" reference is recognized
c) in both previous cases we found instead presences about strangely big DNS sessions
Any kind of suggestions related to the functionality from Applipedia "tcp-over-dns" application?
Thanks in advance
Luca
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-23-2016 01:37 AM - edited 08-23-2016 04:57 AM
Hi Luca,
Have you tried updating your apps & threats to make sure it is running on the latest version?
Also as you are seeing only DNS application traffic then it is possible that the firewall is detecting the tunnelled application of DNS after protocol decoding and putting this into the session end app, you could try setting your security rule to log at session start as well and see if there is an initially discovered application of tcp-over-dns. Though watch out on turning this on as it will increasing your logging a fair bit.
If you still have trouble with the firewall not recognising the app then it would be worth opening a support case for further investigation.
hope this helps,
Ben
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-23-2016 07:12 AM
Hi @bmorris1,
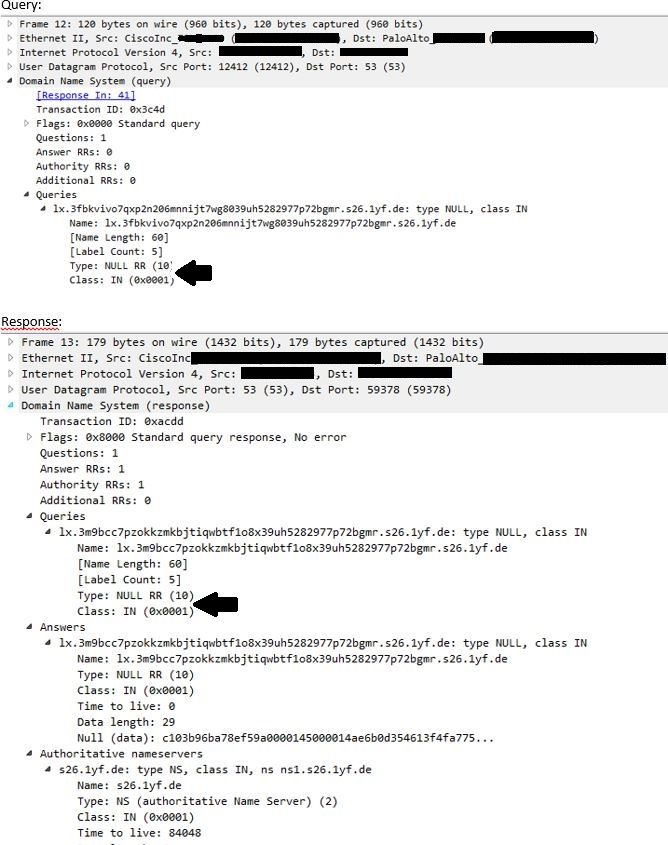
We have collected a pcap and we found that there a lot of TYPE NULL queries.
In your opinion is it possible to block this type of query creating a custom-app?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-23-2016 07:37 AM
Hi @TheRealDiz,
Yes I reckon if you create two conditions matching on the contexts of 'dns-req-section' & 'dns-rsp-queries-section' and the pattern of the string 'TYPE: NULL RR' (not 100% sure on the pattern, would need to test) then you could block/identify this traffic.
Check out this doc for more context defintions if you want to increase the conditions in the signature:
hope this helps,
Ben
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2016 12:53 AM
Hi @bmorris1,
Thanks a lot for you response, I have tested better with another panOS and now it's recognized.
Probably this issue is due to panOS version (I have tested with 7.1.4-h2).
BR
Luca
- 3793 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- Palo Alto to Azure vpn tunnel fails at random in Next-Generation Firewall Discussions
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- Tunnel Monitoring in Next-Generation Firewall Discussions
- stream timeout in General Topics