- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
File Blocking process
- LIVEcommunity
- Discussions
- General Topics
- File Blocking process
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-27-2011 01:37 PM
How does Palo Alto identify files, such as ".exe" when we have a rule set to block the download? What is the process that Palo Alto uses?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2011 04:17 PM
We use signatures to identify the file type. We do not use the extension type.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2011 04:17 PM
We use signatures to identify the file type. We do not use the extension type.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-03-2011 10:25 AM
What are the signatures based upon?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-03-2011 11:56 AM
The system is looking at the file header and MIME type which are determined at file creation. This prevents the obfuscation of the the file by changing the extension to .txt.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2017 10:35 PM - edited 09-12-2017 04:45 AM
Can someone please refer me to an official document (a technical one) by Palo Alto clearly explaining how the file types will be detected (signature in oppose to extension checks). Will greatly help when it comes to cutomers and references.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2017 01:58 PM - edited 09-05-2017 02:00 PM
Binary files have signatures in the beginning of the file.
You can verify if you open file with HEX Editor.
Startingpoint might be here: https://en.wikipedia.org/wiki/List_of_file_signatures
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-12-2017 01:56 PM - edited 09-12-2017 01:56 PM
I haven't seen a highly technical document that really dives into exactly how the file blocking engine works. There's some mention of it in the official documentation. I also found mention of it being based on the content/file type and not just on a file extention in this document:
- https://www.paloaltonetworks.com/resources/techbriefs/content-id-tech-brief
It's easy to validate this functionality for yourself. Configure a "file blocking" profile with action=alert for all applications and all file types. Attach that to a security policy that permits a test machine to use FTP. Take a pdf file and change the extension to .exe (or duplicate that file numerous times and also rename it to .bat, .jpg, .doc, .torrent, etc.). Use FTP to transfer these files through the firewall. Finally, look at the data filtering log to see the results.
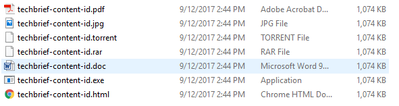
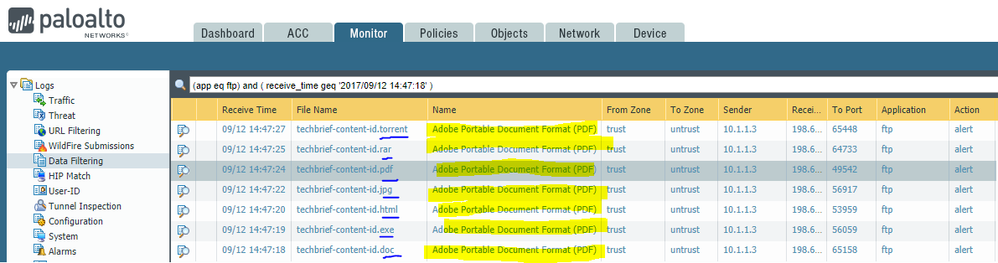
I took a copy of the PDF file linked above, duplicated it a few times, forged the extension on all but one of the samples, and then transferred it through the firewall using FTP. The first snip is the directory with the duplicated/renamed files (all same date and file size). The 2nd snip shows the firewall logging the forged filename while identifying the file type as actually being Adobe PDF.
- 1 accepted solution
- 8756 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Create a IOC without incident in Cortex XDR Discussions
- How do I access init-cfg.txt in VM-Series in the Public Cloud
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- identify for MS Office processes that write an executable file with BIOC or XQL in Cortex XDR Discussions
- How to create a support case without a TCF file in Next-Generation Firewall Discussions