- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Flags field in csv file
- LIVEcommunity
- Discussions
- General Topics
- Re: Flags field in csv file
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-01-2018 11:50 PM
i have a question about flags in csv log.
do you know what does mean Flags 0x19?
in NTP OR DNS logs, flag is 0x19.
Thanks.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2018 02:07 PM
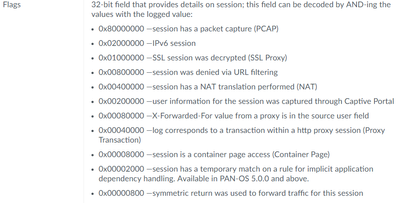
The operation is to apply a bitwise AND operation to the number logged (0x19) with each value from the documentation image posted. If the bitwise AND result is 0, then then the documentation detail is false. If it's 1, then it's true.
0x19 AND 0x00400000 = 0 (no NAT applied)
0x19 by itself doesn't mean anything, it's just a value that can be ANDed to produce a result of zero for each of the types there are.
As @Remo mentions, another set of flags will produce a different result. On my logs, I have NAT enabled, so my logs flags are:
0x400019. When I do a bitwise AND operation on that and 0x00400000 I get a non-zero result, meaning it's "true".
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-05-2018 01:25 PM
That's what I thought but it's good to know we can always count on @gwesson to know all that more technical answers. I don't go playing this far deep in the syslog values often; and you won't see the flag value when you look in the CLI or GUI, pretty much only going to see them looking at the CSV values or the straight Syslog if you forward it to some type of collector.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-02-2018 06:48 AM
0x19 is essentially saying "Okay close the socket". Essentially if you send a UDP request and a response comes back, it's likely to have the 0x19 flag so that the return traffic knows "Okay we're done" and that it can close it's side of the connection.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-02-2018 05:25 PM
Hi BPry.
Thanks for your reply.
Do you know what does 0x19 have to do with AND-ing?
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2018 09:31 AM
I'm not entirely sure what they want you to AND the value with to be honest; AND works like this:
A B =
0 0 0= off
0 1 0= off
1 0 0= off
1 1 1=ON
So essentially unless the binary lines up '1' with '1' you get 0 (or off).
So you would have to convert 0x19 to binary and then convert (I assume) the values that they listed to binary and use AND-ing to combine them. This should give you a binary that once convirted should match one of the listed values? Honestly, not sure.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2018 01:35 PM
Hi @hbshin
I actually don't know what this 0x19 means as this does not matches one of the values in the documentation. Maybe support could tell you more ...
@BPry how or from where do you know what this 0x19 means? Is there somewhere a documentation page that shows more of these values?
Back to the question: this value in the flag column should be ANDed with the values from the documentation: for example the value 0x400019 means there was NAT applied:
10000000000000000011001
10000000000000000000000 (0x00400000 = NAT applied)
= 10000000000000000000000
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2018 02:07 PM
The operation is to apply a bitwise AND operation to the number logged (0x19) with each value from the documentation image posted. If the bitwise AND result is 0, then then the documentation detail is false. If it's 1, then it's true.
0x19 AND 0x00400000 = 0 (no NAT applied)
0x19 by itself doesn't mean anything, it's just a value that can be ANDed to produce a result of zero for each of the types there are.
As @Remo mentions, another set of flags will produce a different result. On my logs, I have NAT enabled, so my logs flags are:
0x400019. When I do a bitwise AND operation on that and 0x00400000 I get a non-zero result, meaning it's "true".
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-05-2018 01:22 PM - edited 08-05-2018 01:22 PM
Flags in my experiance isn't really documented at all in any official Palo Alto documentation.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-05-2018 01:25 PM
That's what I thought but it's good to know we can always count on @gwesson to know all that more technical answers. I don't go playing this far deep in the syslog values often; and you won't see the flag value when you look in the CLI or GUI, pretty much only going to see them looking at the CSV values or the straight Syslog if you forward it to some type of collector.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-17-2018 01:24 PM
Hi,
I was also looking at this, Can you clarify the query.
Is this anyway related to the TCP control flags like for 0x19 which is in binary 0001 1001, If we relate it to the TCP header options, the packet will have FIN-PSH-ACK bit set.
Similary for 0x53, in binary 0101 0011. This will have FIN-SYN-ACK-ECN bits set.
I didnt run tcpdump or wireshark. but trying to understand it from the firewall logs.
- 2 accepted solutions
- 12158 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- User-id with GP client certificate authentication in GlobalProtect Discussions
- How to trigger a "Response page" on Palo Alto NGFWs using URL filtering & Decryption in Next-Generation Firewall Discussions
- ERROR DURING THE BOOT PROCESS( Suggest the resolution) in Next-Generation Firewall Discussions
- How to upload CSV string containing \n to XSOAR? in Cortex XSOAR Discussions
- AcrobatDCx64Manifest3.msi from Akamai 23.200.196.138 detected as ml-virus in Advanced Threat Prevention Discussions