- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Geo Blocking problem
- LIVEcommunity
- Discussions
- General Topics
- Re: Geo Blocking problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Geo Blocking problem
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-24-2020 08:01 AM
Hi, I am using Palo Alto (PA) firewalls hosting Software Version: 8.1.17 in AWS and need to configure Geo-Blocking so that only GB (United Kingdom) requests are permitted and all other requests denied.
The infrastructure setup is as follows:
FQDN => Internet Load Balancer => Palo Alto => Internal Load Balancer => EC2 instance
I have set up "security" policy 1 under the "policies" tab with the 2 x source addresses which belong to the subnets attached to the internet load balancer. See below:
I then set up a second security policy 2 with only "GB" in the source address and enabled the "negate" option (see below). I then placed policy 2 after policy 1 expecting all traffic other than GB to be blocked. This did not work because traffic permitted in rule 1 is obviously forwarding the load balancer IP and not that of the actual source address of the requestor.
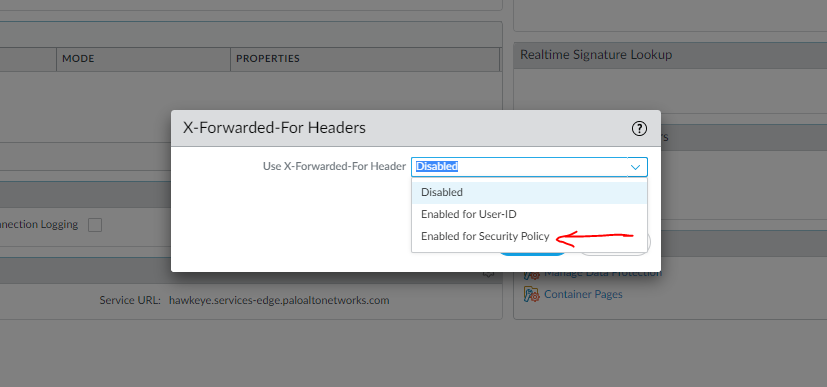
There is an x-forwarded for option (see below) but do I simply enable both checkboxes? Is there further configuration change required? Any help would be much appreciated.
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-24-2020 07:52 PM
Regarding Security policy to allow traffic only from GB you can configure this
Source region GB and destination address which you want and check they negate and then click on action as drop.
This will block traffic from all other countries other than GB for your destination address.
After this policy create another policy and put source IP which you want to allow and put the destination ip address which you want and
action as allow.
Regards
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-24-2020 08:19 PM
You'll want to be running PAN-OS 10 and use the following feature to make this work as best as possible.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-25-2020 06:13 AM - edited 11-25-2020 06:33 AM
Thanks for the info.
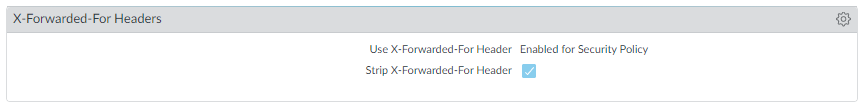
We've set up a dummy Palo Alto in a test environment with PAN-OS 10 to check out the options. See below.
I was hoping I wouldn't have to upgrade the PAN-OS but looks like it may be the only solution. So by enabling the x-forwarded for security policy option, it will be at root level on the PA so may affect other rules. I will have to go through all other rules before making changes. It would have been great if you were able to specify explicit security rules to which the x-forwarded option could be explicitly applied.
Are you aware of any breaking changes upgrading from PAN-OS version 8 to 10?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-25-2020 06:31 AM
@BPry that last response was meant for you. Thanks mate. I keep getting html errors when posting which is quite frustrating.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-25-2020 06:32 AM
Thanks for the help. I'm not entirely sure this will work reflecting on it? The URL that incoming traffic is received via is DNSd to the AWS classic internet load balancer. So all traffic must come via the load balancer, then traverse the Palo Alto and then be blocked if non-GB. That's why the first rule allows all traffic via the load balancer and i set up the second rule to block all non-GB traffic. I may have misunderstood your suggestion so please feel free to correct me. I am in no way a network/firewall expert so open to all suggestions. It would have been easier if i could have blocked all traffic excluding GB at the load balancer.
- 6668 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Palo Alto FW manage by SCM - problem with HA in Strata Cloud Manager
- Stealth Rule Question in Next-Generation Firewall Discussions
- HA ACTIVE firewall is failing when commit in General Topics
- Detect and Block Openclaw with XDR!? in Cortex XDR Discussions