- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Global protect certificate
- LIVEcommunity
- Discussions
- General Topics
- Re: Global protect certificate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-11-2014 12:57 PM
What I meant to say in my last comment is what do you enter for the FQDM since that PA is not a server. It was pointed out to use during a security audit that we were using a self signed certs and one of my tasks is to put a more secure 3rd party cert on the global protect clients.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-11-2014 01:09 PM
It should be a domain name, which will resolve to PAN public IP address (portal address). You can specify the IP address of that interface also.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-11-2014 01:11 PM
Well I don't have any records in DNS for the PA and it has more than one ISP address
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-11-2014 01:13 PM
You may specify the GP-portal IP address.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-11-2014 02:03 PM
So would it be the 66.94.208.114 address indicated in the pic that I have uploaded with this message and also what if I have a secondary ISP that I fail over too. Will global protect still work? Do I need another cert for that secondary ISP address?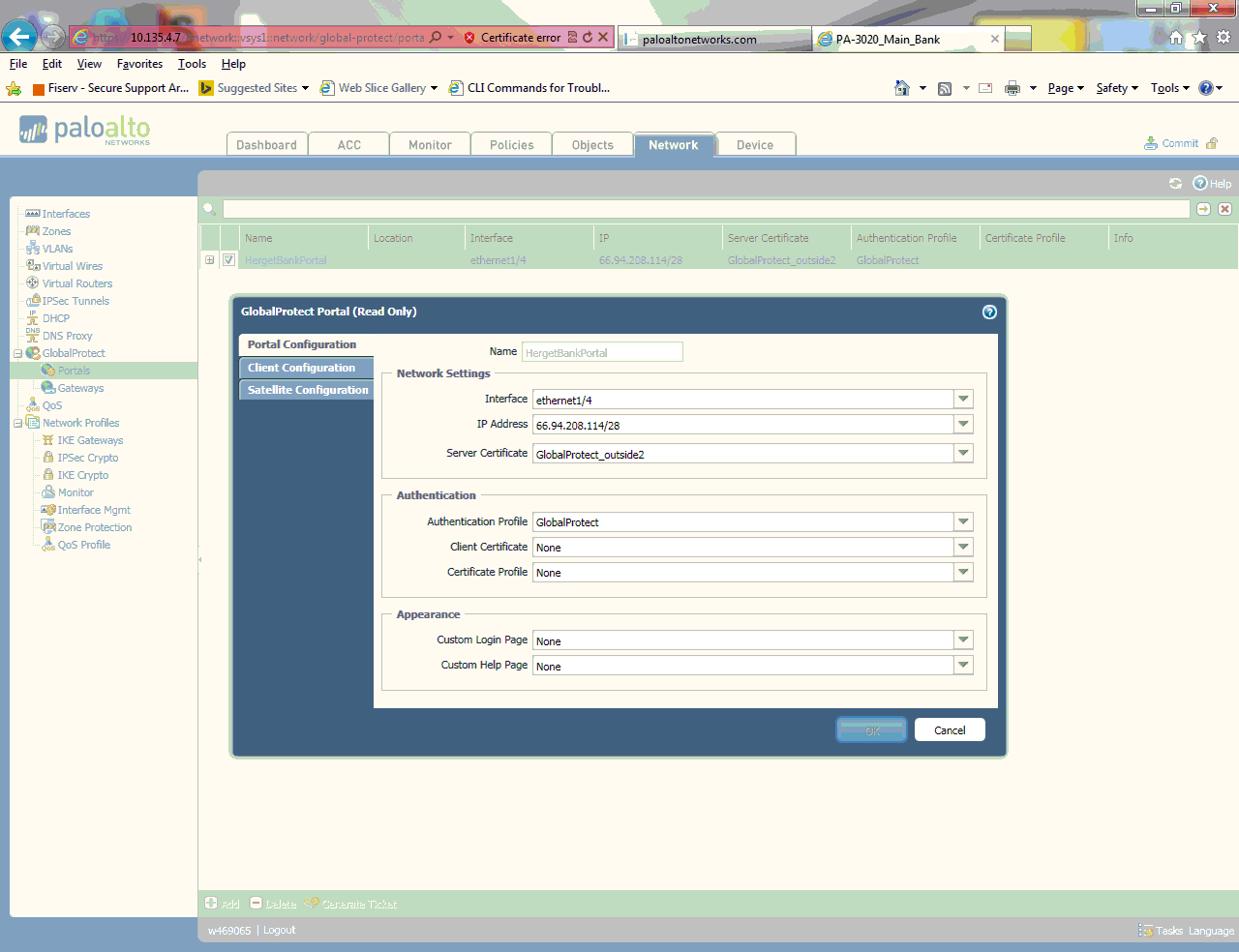
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2014 02:46 PM
The FQDN will be the DNS name you want the users to use for access to the Global portal. For this to work you also need to create that DNS record on your domain DNS server so that the text url will match the certificate FQDN.
Your users CANNOT use the ip address or they will get a the red certificate error.
FQDN examples
vpn.company.com
remote.company.com
access.company.com
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-21-2014 08:42 AM
I just reread this
Your users CANNOT use the ip address or they will get a the red certificate error.
So can they still get in just using the IP address?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-21-2014 01:18 PM
If you use the ip address instead of the certificate name, you will need to accept the certificate warnings issued by the browser to continue the connection attempt. If you get past the warnings, then the connection can continue.
The certificate check consists of three parts. If any of the three fail you will get the certificate warning:
1-FQDN match - the name used in the URL must match the name configured on the certificate
2-Trusted authority - the CA (certificate authority) that issued the certificate must be trusted by the browser. This means one of the public trusted authorities or one where the CA chain has been installed into the browser like a domain authority in Active Directory.
3-Valid date - there is an expiration date on the certificate and this must be valid for the day of the check.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-22-2014 12:40 PM
So Steve really a SSL cert is no more secure than a self signed cert, it doesn't keep you from getting in it just keeps you from getting the cert error.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-23-2014 10:40 AM
It depends on how you define secure. Certainly the encryption provided by a self-signed certificate is no different than that of an official certificate authority.
But the whole reason we have certificate authorities is to vet entities that provide SSL connections. In order to get the official certificate you have to demonstrate to the authority who you are. They in turn are then vouching for you to the general internet public.
This ultimately prevents bad actors from impersonating legitimate businesses by pretending to be your bank or other trusted entity.
We ask user not to ignore certificate warnings. And the modern browsers are making these warnings increasing prominent and more difficult to ignore. This gets users used to not going forward with untrusted certificates and decreases our overall security risk. If we ask users to ignore certificate warnings for our own company sites, they get used to ignoring the warnings when they really do apply and become victims to phishing scams.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-25-2014 06:12 AM
Explain to me what this really mean
"In order to get the official certificate you have to demonstrate to the authority who you are. They in turn are then vouching for you to the general internet public." What is it they do to prove who you are and assure that its not someone else?
Global protect is not a web page and I get the cert error every time I try to login to the console for PA.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-25-2014 01:55 PM
Global protect uses SSL and certificates in exactly the same way the web pages do. Global protect is a web server.
Certificate authorities require a company to provide information to prove their identity as an organization. This prevents anyone from pretending to be a company and getting a FQDN certificate in the name of that company. Thus the Certificate Authority helps us know that a web site really is the property of who they claim to be.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 06:24 AM
So are you saying that global protect can be spoofed?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 08:35 AM
Any public SSL certificate can be trivially spoofed by any of the organisations with a cert in your "Trusted Root Certificates" store. As the name suggests; you're just running on trust that they don't do this. An insane arrangement in my opinion....
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 08:55 AM
So ajbool you don't see any real benefit to adding a 3rd pary cert to global protect over a self signed cert? I also don't understand how you can spoof a global protect client anyway.
- 13151 Views
- 35 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect Portal / Clientless VPN does not recognize SAML username after update to 10.1.14-h20 in GlobalProtect Discussions
- recv rst from server or recv from zero win from server in General Topics
- Global Protect Connectivity Issue in GlobalProtect Discussions
- Palo Alto does not support global certificates. Is there a solution? in Next-Generation Firewall Discussions
- MANDATORY ACTION REQUIRED: Device Certificate Enforcement affects PA-440 in General Topics



