- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Global protect firewall behavior after reaching max users
- LIVEcommunity
- Discussions
- General Topics
- Global protect firewall behavior after reaching max users
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2020 09:31 AM
Hello Community,
Looking for more details on firewall behavior after reaching max-users limit on Global protect.
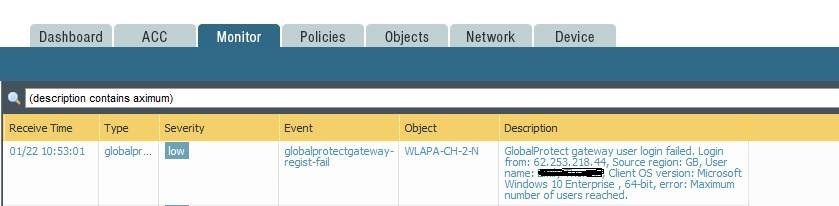
For example, Assume a portal with 4 gateways in different regions. If one of the gateway(Lets assume PA-3020) which has capacity of 1024 concurrent connections, reached its maximum limit. what will happen if user 1025 tries to reach 3020 during latency calculations.
Will GP client receive a response to TLS/SSL negotiation or will it not respond to the request.
Looking for details. Tried to find more details but no luck. Any help is appreciated.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2020 09:30 PM
Yes you are correct regarding certificate auth. As user has no input.
this will be the same for 2fa to the portal with authentication override cookies to the gateways.
I’m not sure regarding 2fa to the gateway as we don't use it but going by the system logs i would guess that the auth will be accepted but then the gateway will fail as above it’s limit, the user would then be asked to re auth to next gateway.
if any of our devices max out i will test this theory but it may be a while and somebody else may have the answer.
i cannot understand why a gateway would offer itself as available when over its limit. Perhaps that needs to be requested or perhaps they should be monitored better to prevent such an event. We use PRTG and API’s for this but setting gateway priorities is still done manually.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2020 09:47 AM
the ssl handshake still takes place and the gateway is still given the same priority, so if the user tries to connect then the below happens and the next gateway in the priority is used.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2020 10:25 AM
Great. Thank you for quick response.
Couple of questions.
If user-authentication is transparently happening(lets assume certs are being used), then users will not see "authentication failed" message and move forward with associating to next gateway. ?
If gateways are doing second factor (token for example), then would that 1025th user, who reaches an already maxed-out gateway, see an option to enter 2fa-token (or) not.?
If yes, and 2FA-input is provided, will the user then see an "authentication failed" message from the maxed-out gateway and then GP-client will move on to next gateway.?
Please let me know if I am not clear.
Thanks Again.
-Surya
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2020 09:30 PM
Yes you are correct regarding certificate auth. As user has no input.
this will be the same for 2fa to the portal with authentication override cookies to the gateways.
I’m not sure regarding 2fa to the gateway as we don't use it but going by the system logs i would guess that the auth will be accepted but then the gateway will fail as above it’s limit, the user would then be asked to re auth to next gateway.
if any of our devices max out i will test this theory but it may be a while and somebody else may have the answer.
i cannot understand why a gateway would offer itself as available when over its limit. Perhaps that needs to be requested or perhaps they should be monitored better to prevent such an event. We use PRTG and API’s for this but setting gateway priorities is still done manually.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2020 09:24 AM
Great explanation @Mick_Ball . Thank you so much for your help.
- 1 accepted solution
- 9837 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PAN-OS 11.1.13 Predefined reports displaying IPv4 addresses in IPv6 format in General Topics
- Windows Clients – Captive Portal Not Triggering with GlobalProtect Always-On Enabled in General Topics
- DHCP Relay over SDWAN issue in Advanced SD-WAN for NGFW Discussions
- Enterprise firewalls need to be opened for new Redirector IP addresses on ports 443/TCP and 3851/UDP in General Topics
- Issue with PA-445 Failover - Interface Reset in General Topics