- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Global Protect, use custom port for portal, followed the tutorial on paloaltonetwork
- LIVEcommunity
- Discussions
- General Topics
- Global Protect, use custom port for portal, followed the tutorial on paloaltonetwork
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Global Protect, use custom port for portal, followed the tutorial on paloaltonetwork
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2018 12:10 PM
Hi,
I followed the tutorial : How to Configure GlobalProtect Portal Page to be Accessed on any Port but it's not working.
When I connect using browser I get an error. I see in monitor that the port is accessed and I see the rules for the nat as well, but in the application it's written "incomplete". How can I debug it further ?
Thanks for help.
Jon
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2018 12:26 PM
HEllo,
I would start by looking at the logs to see if/where the traffic is getting blocked. My guess is that its probably a typo somewhere and its causing a block?
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-22-2018 09:22 AM
There is no typo.
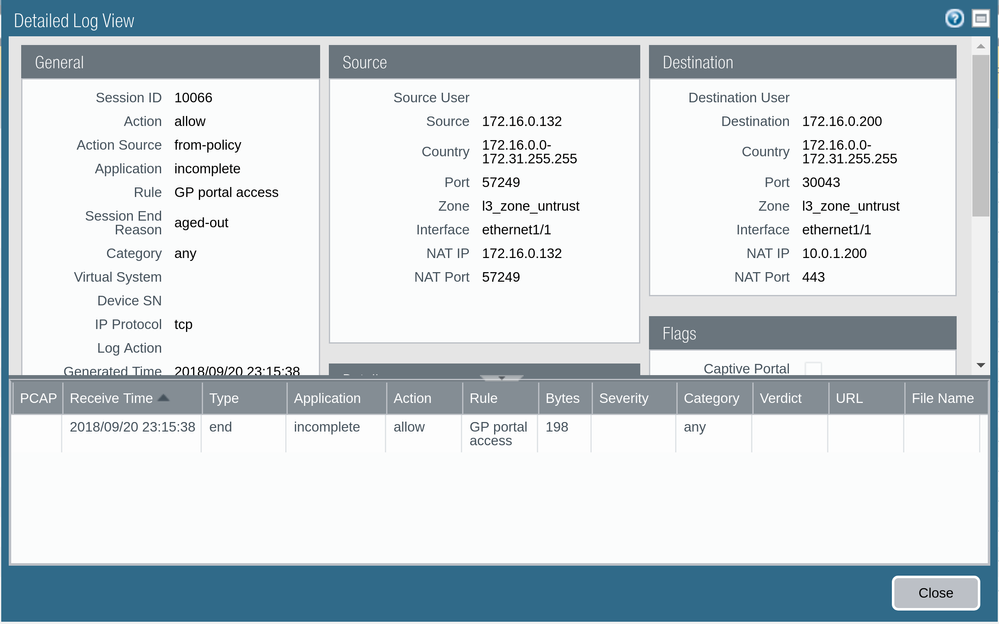
Here is the screenshot of the monitor:
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-22-2018 09:28 AM
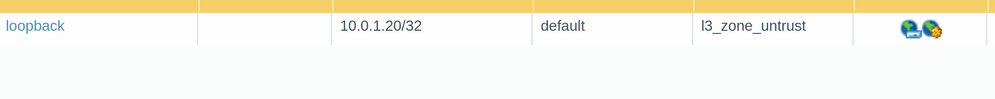
pics of loopback:
screen of nat:
security rules:
We see that all rules has count, means they are triggered...
And inside the monitr they are no block, I even override intra/interzone to show inside the logs.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-22-2018 12:12 PM
I would take a look at your routing with that NAT statement in place. Your logs don't seem to show it due to where you cut them off, but are you showing any received traffic at all or just sent?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-22-2018 12:19 PM
there is no routing, only default route 0.0.0.0/0 on the next hope, and if I remove loopback, nat and loopback ip on the portal/ge, the portal is working from outside using port 443.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2018 11:50 AM - edited 09-25-2018 12:44 PM
Just to add some new information.
After applying the NAT rules, I see on the other router ARP message like this: Broadcast ARP Gratuitous request for 172.16.0.254 ( duplicate use of 172.16.0.254 detected).
172.16.0.254 == my second router IP and the configured nextHop on the palo.
The network diagram is the following:
palo with ip internal 192.168.200.1 and ip external 172.16.0.200 connected to a router with ip 172.16.0.254.
I'm wondering why adding the nat rules make this message appears.
After doing packet capture on the palo, I can see in the DROP pcap, SYN from 172.16.0.144 (ip where i connect to the portal on port 30043) on port 443, on RECV pcap, I can see SYN on port 30043 from ip 172.16.0.144.
Question is why traffic is dropped on 443 ? I have rules like in the tutorial for it.
- 3555 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!