- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
GlobalProtect OCSP URL location with Offline Root CA and Enterprise Subordinate CA
- LIVEcommunity
- Discussions
- General Topics
- Re: GlobalProtect OCSP URL location with Offline Root CA and Enterprise Subordinate CA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-31-2017 07:20 PM
Hi guys,
We are using Certificate Authentication Profile for Pre-Logon and then Username and Password before VPN can be established.
GP is working fine and we would like to validate when certificate is revoked, it will stop the machine from connecting.
In our environment we have an Standalone Root CA and Enterprise Subordinate CA and the URL locations for OCSP and CDP are pointing to LDAP.
CDP
[1]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=ldap:///CN=Ent-CA,CN=ServerName,CN=CDP,CN=Public Key Services,CN=Services,CN=Configuration,DC=X,DC=local?certificateRevocationList?base?objectClass=cRLDistributionPoint (ldap:///CN=Ent-CA,CN=ServerName,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=X,DC=local?certificateRevocationList?base?objectClass=cRLDistributionPoint)
AIA (OCSP?)
[1]Authority Info Access
Access Method=Certification Authority Issuer (1.3.6.1.5.5.7.48.2)
Alternative Name:
URL=ldap:///CN=Ent-CA,CN=AIA,CN=Public Key Services,CN=Services,CN=Configuration,DC=X,DC=local?cACertificate?base?objectClass=certificationAuthority (ldap:///CN=Ent-CA,CN=AIA,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=X,DC=local?cACertificate?base?objectClass=certificationAuthority)
Which URL do i need to set up under the Certification Profile Default OCSP URL?
Do i also need to enter the Root CA OCSP URL?
Thanks for the input.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2017 10:22 AM
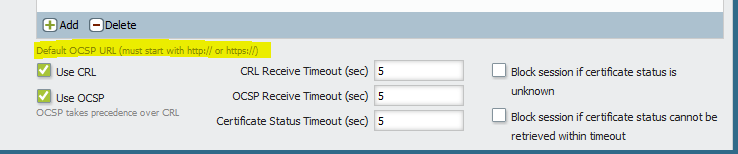
If the url is included in your certificate then it will be enough if you simply click the checkboses for "Use OCSP" and "Use CRL". OCSP is always the preferred one.
In the url's you only need the url for your intermediate CA, because this is the one which signs your client/user certificates.
Ok, the inermediate can be revoked too but if you ever run into a problem with this one revoked then you need to manually change the cert on the firewall anyway. But if you simply import the root cert to your fw cert store, the fw will also get revocation information for that cert and likely mark your inermediate as invalid if it is revoked, but I did never test this.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2017 08:53 PM - edited 06-01-2017 08:56 PM
thanks @Remo
I have simply checked the Use OCSP and Use CRL Checkboxes.
i have since revoked a certificate, and Delta CRL is set to be updated everyday. Is there a way to check if GP is checking the CRL?
I just also noticed that the Default OCSP URL must start with http or https
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2017 10:22 AM
If the url is included in your certificate then it will be enough if you simply click the checkboses for "Use OCSP" and "Use CRL". OCSP is always the preferred one.
In the url's you only need the url for your intermediate CA, because this is the one which signs your client/user certificates.
Ok, the inermediate can be revoked too but if you ever run into a problem with this one revoked then you need to manually change the cert on the firewall anyway. But if you simply import the root cert to your fw cert store, the fw will also get revocation information for that cert and likely mark your inermediate as invalid if it is revoked, but I did never test this.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2017 08:53 PM - edited 06-01-2017 08:56 PM
thanks @Remo
I have simply checked the Use OCSP and Use CRL Checkboxes.
i have since revoked a certificate, and Delta CRL is set to be updated everyday. Is there a way to check if GP is checking the CRL?
I just also noticed that the Default OCSP URL must start with http or https
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-02-2017 09:26 AM
- Search in your system logs: (description contains 'CRL')
- Try to connect with a computer which has a revoked certificate
- https://live.paloaltonetworks.com/t5/Management-Articles/View-Delete-CRL-and-OCSP-cache/ta-p/59286
- less mp-log sslmgr.log
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-10-2017 05:59 PM
I confirm that LDAP CRL works as well.
I revoked a certificate from CA and deny re-enrollment.
When trying to connect to the GP Portal with the revoked cert - the client is showing "Required client certificate is not found"
- 2 accepted solutions
- 6891 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- The user information linked in the CIE does not match the match criteria in the GP's application settings. in Prisma Access Discussions
- Administrator Login using Azure Groups through Cloud Identity Engine in General Topics
- SAML - Integration - Globalprotect Azure-AD-EntraID - Policy Based Groups Azure-AD for GP Zone in General Topics
- GlobalProtect prelogon and internal gateway detection in General Topics
- Gateway Unresponsive or unreachable. in GlobalProtect Discussions