- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
GlobalProtect with NATet interface
- LIVEcommunity
- Discussions
- General Topics
- Re: GlobalProtect with NATet interface
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2014 11:36 AM
I have a PA200, and is using eth1 for outside (internet) and eth2 for inside. I'm NATing from eth2 to eth1, as normal.
Now i want to have the management https address on the eth1 for several reasons.
At home its just for testing, but at my office i have PA200 between subnets that is duplicate, and not nessesary to route to.
When i use a management profile with access to ping and https on eth1, it wont't work.
I suspect the NAT rule has something to do with it. Cause when i set it up in my lab with no NAT, it works.
Any tips for me please?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2014 12:25 PM
May be you are experiencing the land attack. When we access the external interface from outside the source will be external host public IP and destination will be your external interface IP. When the return traffic is sent out ( server to client s2c ) it exchanges the source and destination and gets stuck seeing the source and destination the same considers a land attack and drops.
If you do
"show counter global filter delta yes | match land"
If the counters are seen then that would prove it. We will have to change the nat slightly and it should start to work.
Details are mentioned in the below doc:
Unable to Connect to or Ping a Firewall Interface
Hope this helps !
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2014 11:56 AM
I got it working with a DNAT against the outside ip address. But is this needed?
Is there another way doing it? The IP is public and facing internet, i though a management profile would open anyway.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2014 11:53 AM
This is working as expected. If you are NATing 443 from the outside to an inside server you loose access to the management page. You can set up a loopback and NAT another port to 443 on the loopback with an management profile that allows HTTPS.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2014 12:25 PM
May be you are experiencing the land attack. When we access the external interface from outside the source will be external host public IP and destination will be your external interface IP. When the return traffic is sent out ( server to client s2c ) it exchanges the source and destination and gets stuck seeing the source and destination the same considers a land attack and drops.
If you do
"show counter global filter delta yes | match land"
If the counters are seen then that would prove it. We will have to change the nat slightly and it should start to work.
Details are mentioned in the below doc:
Unable to Connect to or Ping a Firewall Interface
Hope this helps !
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2014 02:43 PM
How to Access the WebUI when GlobalProtect Is Enabled
Your subject is about GP so just to remind you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2014 12:33 AM
I dont NAT anything from untrust to trust, i only have a overload nat from trust to untrust.
But it seams that it blocks everything, including ping, and https (thats why the GP wont connect).
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2014 12:43 AM
Thanks! I'll try that later today.
I got ping working if i add a roule thats like this:
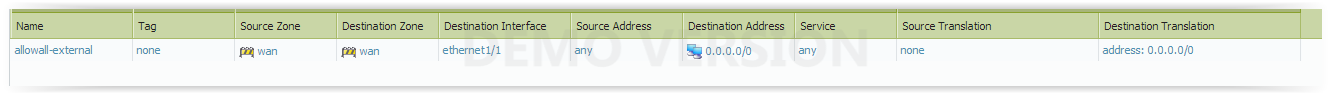
0.0.0.0/0 is just there to mas my origin public ip. The other rule is gone, as this is a test box at work.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2014 01:08 AM
This rule is not a need but your other NAT rules are important.you have any other NAT rule with source zone any ?
or just 1 NAT rule from trust to untrust ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2014 01:16 AM
Since im not home now, i cant confirm, but yes, i might have to rule setup with source any, and not pined down to my trust zones.
This is bad practice, i know. But is that the problem? I'll doublecheck when i get home.
The rule might be like this one, with source any.
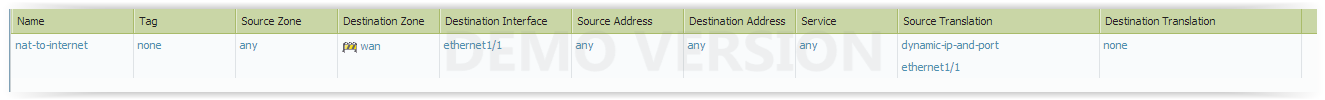
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2014 01:19 AM
Yes it will be a problem as Phoenix said.
Try to change it with Trust and then test again.
- 1 accepted solution
- 6057 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GloablProtect + Explicit Proxy blocks WSL traffic. in GlobalProtect Discussions
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions
- GlobalProtect Gateway on PA-820 Stopped Responding – Guidance Needed in GlobalProtect Discussions
- GlobalProtect on HA in General Topics
- LDAP Authentication works when testing it via SSH command but fails on web interface in General Topics



