- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
GRE over IPSec with NAT
- LIVEcommunity
- Discussions
- General Topics
- Re: GRE over IPSec with NAT
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-27-2021 08:24 AM
hello everyone
I am here again.
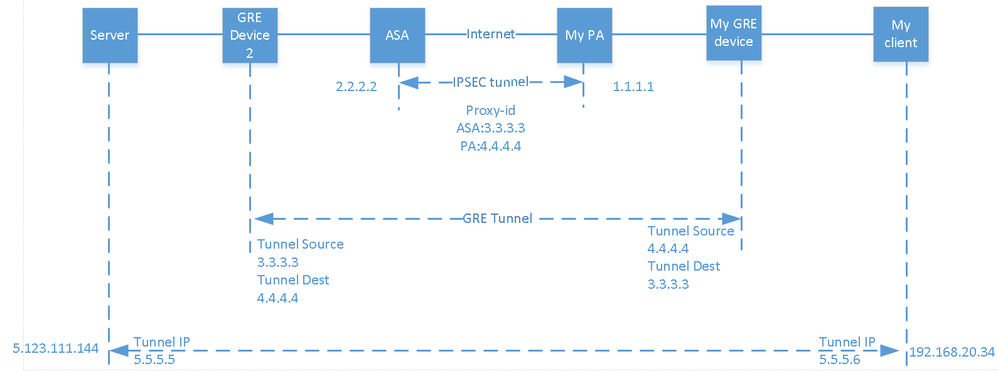
Referring to the following diagram, My client need to talk with the server 5.123.111.144.
stage 1, to get the GRE tunnel working.
My current is
1. the IPSec tunnel is up.
2. I am using a Cisco router as the GRE device, the tunnel config is
interface Tunnel2
description GRE
ip address 5.5.5.6 255.255.255.0
tunnel source 192.168.55.250 >>>>>>>>>>>>>this IP will be natted to 4.4.4.4
tunnel destination 3.3.3.3
3. the security policy for the GRE tunnel is
trust zone > ipsec zone, source IP 192.168.55.250, dst IP 3.3.3.3
ipsec zone > trust zone, source IP 3.3.3.3, dst IP 192.168.55.250
4. NAT policy
trust zone > ipsec zone, source IP 192.168.55.250 source NAT to 4.4.4.4, bi-direction is yes.
till now, when I ping the tunnel dst 3.3.3.3 with source IP 192.168.55.250, I can see the ping log on the PA and the log showing 192.168.55.250 is being translated to 4.4.4.4, but the ping is failed. I cannot see any packet from 3.3.3.3 in the log. what the issue could be?
stage 2, get my client be able to talk with the server 5.123.111.144.
whats the security and NAT policy should be?
Thank you.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-30-2021 03:04 AM - edited 04-30-2021 06:28 AM
hello @aleksandar.astardzhiev
hello @AlexanderAstardzhiev
"The PAN FW has nothing to do with 5.5.5.x addresses, isn't this the whole purpose of the GRE tunnel?
- Packets from the client will enter the router
- Which will add GRE encapsulation, which boilse down to a new IP header
- Now the outer IP header (that is used for routing decisions) is has different source and destination addresses - more specifically your GRE tunnel addresses, right?
- When the packet reaches the PAN FW and if you don't apply any tunnel content inspection it will see only the 3.3.3.3 and 192.168.55.250."
---------------This is exactly what I thought.
When 192.168.20.34 sending a packet to the 5.123.111.144, the traffic flow should be (my understanding, please correct if anything wrong)
Original packet send to GRE device
S:192.168.20.34
D:5.253.111.144
GRE tunnel encapsulates the original packet by adding an extra header, so the source/destination IP in the packet changes to
S: 192.168.55.250 192.168.20.34
😧 3.3.3.3 5.153.111.144
My firewall NAT the 192.168.55.250 to 4.4.4.4 then send the packet towards to the IPsec tunnel, ipsec tunnel add extra header
S: 1.1.1.1 4.4.4.4 192.168.20.34
😧 2.2.2.2 3.3.3.3 5.153.111.144
The ASA removes the IPSec header and delivers it to the other side GRE device
S: 4.4.4.4 192.168.20.34
😧 3.3.3..3 5.153.111.144
The other side GRE device removes the GRE header and delivers the original packet to the server
S: 192.168.20.34
😧 5.153.111.144
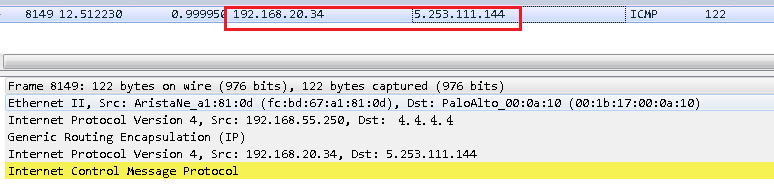
I thought we should be able to see the log on PA from 192.168.55.250 to 3.3.3.3 but I cannot. Why?
I took a pcap on the PA, the packet I got is, but cannot see it in the log
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-28-2021 12:01 AM
Hi @DongQu ,
Your NAT for the "stage1" seems fine. The outbound rule also seems ok, but it the inbound rule is incorrect.
I used to look at my notes every time when I was about create NAT rule:
"NAT rule must be configured with pre-NAT zones (zones matching the addresses before the NAT)
Security rule must be configured with pre-NAT addresses, but post-NAT zones"
This means that your inbound rule should be:
ipsec zone > trust zone, source IP 3.3.3.3, dst IP 4.4.4.4 (dst zone after the NAT, but dst IP before the NAT)
Unfortunately this will not solve your ping problem. The inbound rule will allow you remote site to initiate traffic, but should not have any effect on the return traffic for your outbound pings. If you see the "allow" log with correct NATed source it sound your rule, nat and route are correct (if the route was not correct I wouldn't expect rules to match the dst zone)
- Do you see the counter for encrypted packets increasing while you are pinging? What about the decrypted packets?
- In the traffic log what is the counter of "packets send" and "packets received"?
- Can you check on the ASA if the counters of encrypted and decrypted packets are increasing?
About the second part of your question - I really don't understand what you want to achieve... From the diagram I understand that you will bring GRE tunnel between two Cisco routers. This traffic will be routed through IPsec tunnel between ASA and PAN FW. What I don't understand is what are "tunnel IP 5.5.5.5" and "tunnel IP 5.5.5.6". Is this another tunnel inside the GRE? Or your want to "hide" the client ip behind 5.5.5.6 and the server behind 5.5.5.5?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-28-2021 04:08 AM - edited 04-28-2021 04:29 AM
hello @aleksandar.astardzhiev
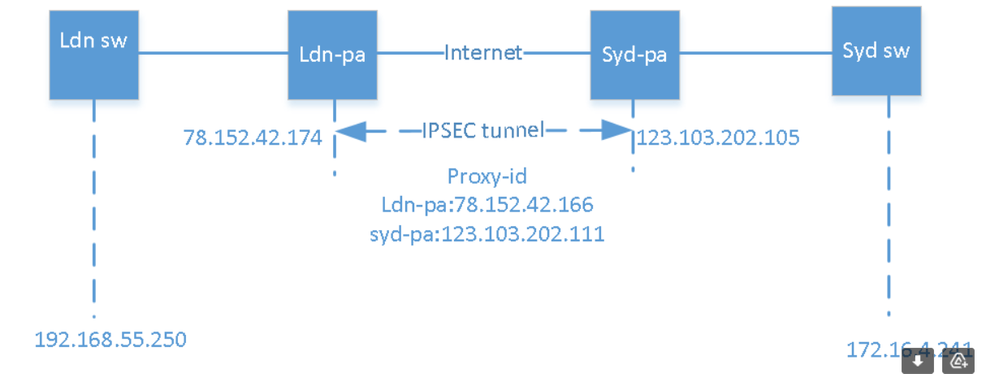
for stage 2, what I want to achieve is
1. the tunnel IP can ping each other, 5.5.5.6 <> 5.5.5.5
2. the client 192.168.20.34 is able to ping 5.123.111.144
for 1:
I need to add static routing on PA for dest 5.5.5.5, point to the ipsec tunnel interface and add static for my side tunnel IP 5.5.5.6, point to internal interface, as before adding the routing entry, the PA goes to 5.5.5.0/24 via the default route to the internet
So the outbound security policy should be
trust zone > ipsec zone source 5.5.5.6 to dest 5.5.5.5
inbound security policy should be
ipsec > trust zone source 5.5.5.5 to des 5.5.5.6
is this correct?
for your question about stage2
Or your want to "hide" the client ip behind 5.5.5.6 and the server behind 5.5.5.5? --- exactly.
I have static routing "ip route 5.123.111.144 255.255.255.0 tunnel 2" on my switch, so when my client 192.168.20.34 pinging 5.123.111.144, the GRE switch will add extra header S:5.5.5.6 D:5.5.5.5 before the raw packet header S:192.168.20.34 D 5.123.111.144
So I dont need to create policy for 192.168.20.24 <> 5.123.111.144 as the packet header has been changed after the packet leaving the tunnel towards to PA.
I hope I am making sense(excuse for my bad English)
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-29-2021 01:10 AM
Hi @DongQu ,
I am probably missing something... The PAN FW has nothing to do with 5.5.5.x addresses, isn't this the whole purpose of the GRE tunnel?
- Packets from the client will enter the router
- Which will add GRE encapsulation, which boilse down to new IP header
- Now the outer IP header (that is used for routing desicion) is has different source and destintion addresses - more specificaly your gre tunnel addresses, right?
- When the packet reaches the PAN FW and if you don't apply any tunnel content inspection it will see only the 3.3.3.3 and 192.168.55.250.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-30-2021 03:04 AM - edited 04-30-2021 06:28 AM
hello @aleksandar.astardzhiev
hello @AlexanderAstardzhiev
"The PAN FW has nothing to do with 5.5.5.x addresses, isn't this the whole purpose of the GRE tunnel?
- Packets from the client will enter the router
- Which will add GRE encapsulation, which boilse down to a new IP header
- Now the outer IP header (that is used for routing decisions) is has different source and destination addresses - more specifically your GRE tunnel addresses, right?
- When the packet reaches the PAN FW and if you don't apply any tunnel content inspection it will see only the 3.3.3.3 and 192.168.55.250."
---------------This is exactly what I thought.
When 192.168.20.34 sending a packet to the 5.123.111.144, the traffic flow should be (my understanding, please correct if anything wrong)
Original packet send to GRE device
S:192.168.20.34
D:5.253.111.144
GRE tunnel encapsulates the original packet by adding an extra header, so the source/destination IP in the packet changes to
S: 192.168.55.250 192.168.20.34
😧 3.3.3.3 5.153.111.144
My firewall NAT the 192.168.55.250 to 4.4.4.4 then send the packet towards to the IPsec tunnel, ipsec tunnel add extra header
S: 1.1.1.1 4.4.4.4 192.168.20.34
😧 2.2.2.2 3.3.3.3 5.153.111.144
The ASA removes the IPSec header and delivers it to the other side GRE device
S: 4.4.4.4 192.168.20.34
😧 3.3.3..3 5.153.111.144
The other side GRE device removes the GRE header and delivers the original packet to the server
S: 192.168.20.34
😧 5.153.111.144
I thought we should be able to see the log on PA from 192.168.55.250 to 3.3.3.3 but I cannot. Why?
I took a pcap on the PA, the packet I got is, but cannot see it in the log
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-30-2021 06:33 AM - edited 04-30-2021 06:33 AM
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-03-2021 07:25 AM - edited 05-03-2021 07:26 AM
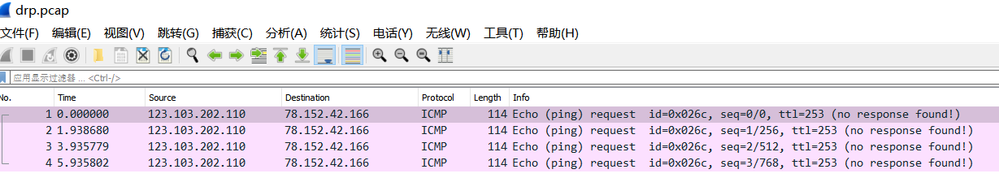
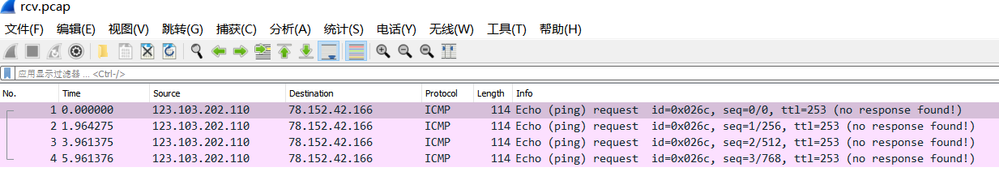
I've no idea where the issue is...
- 1 accepted solution
- 7128 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- Connectivity with Panorama in VM-Series in the Public Cloud
- Performance impact of using higher DH group for site-to-site VPNs in Next-Generation Firewall Discussions
- GlobalProtect VPN Client windows 11 crash in GlobalProtect Discussions