- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
GRE protocol traffic
- LIVEcommunity
- Discussions
- General Topics
- Re: GRE protocol traffic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2013 03:49 AM
Hello to All,
I noticed some strange behavior regarding GRE protocol, and try to explain what exactly is strange:
Customer has unfortunate GRE VPN tunnel and in one policy "Public_ulaz_GRE" they stated to pass only GRE and NVGRE protocol respectively. (following picture)

But, when you filter traffic by mentioned policy, you can see that beside legitimate, bunch of non-gre traffic are allowed by this policy!??
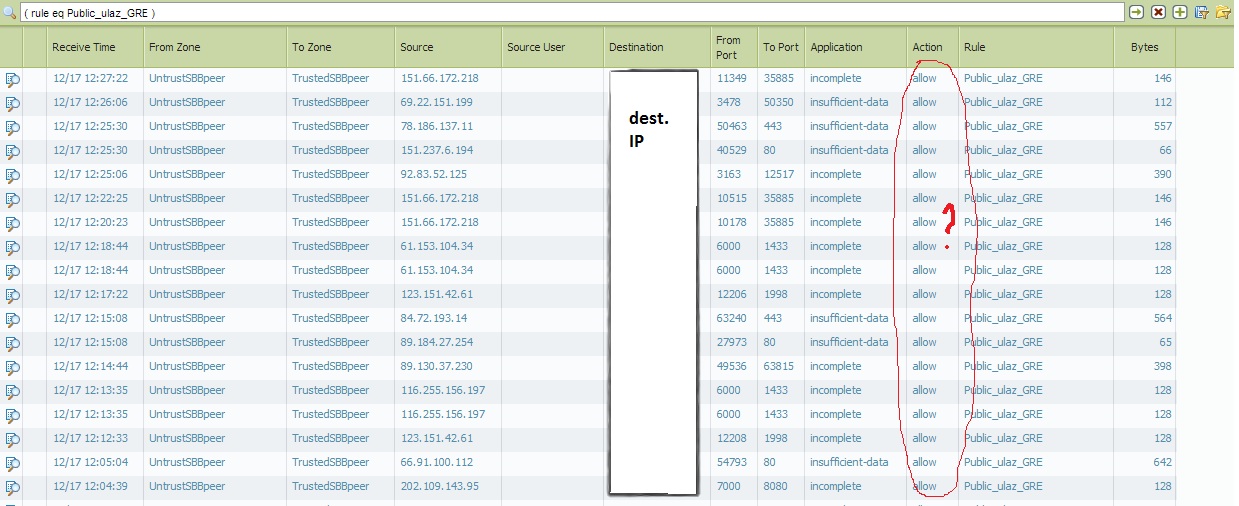
Is someone have reasonable explanation for this behavior?
Regards,
Tician
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2013 09:22 AM
Hello Tician,
Yes this is expected if "Public_ulaz_GRE" lies at the top of your security rules . Before the 3-way handshake completes and the session's application is detected as incomplete/in-sufficient data, the security policy lookup for the session will match the first security policy which matches all attributes except application. Once the 3-way handshake completes and the firewall sees a data packet which can be used to identify the app the session will shift the application to the appropriate value and do another security policy lookup.
Because the application is not known, when the SYN packet is received, the application portion of the security policies can not be applied. As a result, the security policy lookup is performed against the 6 tuples of the session, source and destination IP and port, ingress interface (actually zone) and protocol. The first policy which matches these 6 tuples will be used to allow the SYN and any additional packets that traverse the firewall before the application is identified.
Hope that helps!
Thanks and regards,
Kunal Adak
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2013 09:22 AM
Hello Tician,
Yes this is expected if "Public_ulaz_GRE" lies at the top of your security rules . Before the 3-way handshake completes and the session's application is detected as incomplete/in-sufficient data, the security policy lookup for the session will match the first security policy which matches all attributes except application. Once the 3-way handshake completes and the firewall sees a data packet which can be used to identify the app the session will shift the application to the appropriate value and do another security policy lookup.
Because the application is not known, when the SYN packet is received, the application portion of the security policies can not be applied. As a result, the security policy lookup is performed against the 6 tuples of the session, source and destination IP and port, ingress interface (actually zone) and protocol. The first policy which matches these 6 tuples will be used to allow the SYN and any additional packets that traverse the firewall before the application is identified.
Hope that helps!
Thanks and regards,
Kunal Adak
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2013 03:28 PM
Hello Kunal,
yes this is very helpful answer, thank you...
- 1 accepted solution
- 6310 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Log Collector Redundancy in Panorama Discussions
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Palo Alto FW manage by SCM - problem with HA in Strata Cloud Manager
- Stealth Rule Question in Next-Generation Firewall Discussions



