- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
HA binding "both option" not working in NAT policy
- LIVEcommunity
- Discussions
- General Topics
- HA binding "both option" not working in NAT policy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
HA binding "both option" not working in NAT policy
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-01-2013 01:03 PM
Dear all,
I've configured my Palo Alto Cluster in a L3 Active / Active cluster setup.
While I was trying to implement a NAT policy (Source Address Translation), it turns out that the only options that are working are: "0" and "1", as a reference to the member of the active/active cluster which should take care of the Address Translation.
It turns out that the other option are not accepted by the PAN-OS while trying to push/commit the previously defined NAT policy (results in ERROR)
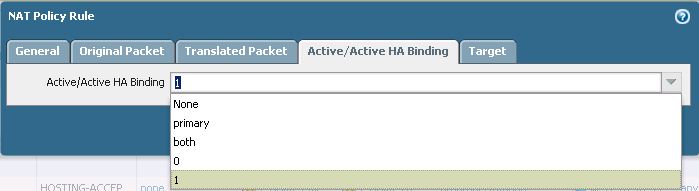
Would be works as designed?
Because, as a workaround I cloned the NAT rule, using either active/active binding to "0"
and
the exact same NAT rule, using active/active binding "1".
Seems to be working fine, although I can imaging that the option "PRIMARY" would allow us to create this NAT rule ONLY ONCE.
Thanks !
Kind regards,
Wim
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-06-2013 08:03 PM
In a A/A cluster, each device requires its own IP pool and is associated to a device-id. Hence for source translation, you will need two rules using the corresponding device-id, so when a new session is created, device binding determines which NAT rules are matched by the firewall (the device binding must include the session owner device to produce a match).
Refer to pages 25, 96 & 97 in the following article for more on NAT in A/A setup:
Configuring Active/Active HA PAN-OS 4.0
Hope that helps!
Aditi
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2013 01:22 AM
Meanwhile I also received feedback of our Palo Alto Networks local systems engineer.
Allow me to share this information, because it revealed to root cause / answer to our problem.
NAT device binding options include the following:
- Device 0 and Device 1—Translation is performed according to device-specific bindings only if the session owner and the device ID in the NAT rule match. evice-specific NAT rules are commonly used when the two firewalls use unique public IP addresses for translation
- Both—This option allows either device to match new sessions to the NAT rule and is commonly used for destination NAT
- Primary—This option allows only the active-primary device to match new sessions to the NAT rule. This setting is used mainly for inbound static NAT, where only one firewall should respond to ARP requests. Unlike device 0/1 bindings, a primary device binding can move between devices when the primary role is transferred
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-19-2014 01:29 PM
Can someone clarify for me the setup for a "dynamic-ip-and-port" source nat on an active/active cluster? The traffic for this particular rule must be source natted to a particular x.x.2.15 address when traversing through either device and should work when either member is down. Please specify the A/A bindings required for the rule, and scenarios with and without floating IPs on the outside. Thank you.
-Johnny
- 8042 Views
- 3 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- powered down V-wire port in General Topics
- Update PANOS to 11.2.3-h3 from 10.2.12-h2 in General Topics
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- "More runtime stats" not loading when Advanced routing is enabled in Next-Generation Firewall Discussions
- PA-415-5G not working with fresh T-Mobile SIM in General Topics



