- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
HTTP Header - Logging NTLM Username
- LIVEcommunity
- Discussions
- General Topics
- HTTP Header - Logging NTLM Username
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
HTTP Header - Logging NTLM Username
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-29-2015 09:23 PM
My PA firewall inspects traffic between my users and proxy server. The proxy server provides NTLM authentication. Is there a way of logging the NTLM authenticated username within the http headers?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-29-2015 11:30 PM
Hello Ascit,
I am not clear, what you want to achieve. HTTP header is not having a field for user. Could you please explain your requirement here in details.
Check out this discussion thread:
Re: Captive portal, manage authenticated users
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-30-2015 06:06 AM
HULK, in this instance the PA is not acting as the proxy it sound like. The PA is in between the proxy and the user and is able to inspect that traffic.
ascit, I believe that the NTLM portion of the traffic is not within the HTTP header but in a separate NTLM header in the packet. I don't know if the PA would recognize the traffic separately once it ID's the traffic as HTTP.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-01-2015 09:51 PM
Correct, I'm hoping to some how log the NTLM User name field:
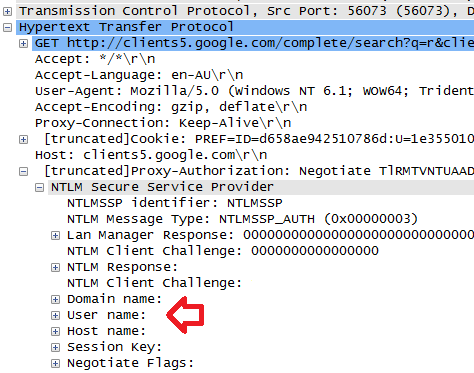
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-01-2015 11:29 PM
Hi Ascit
The firewall can not log this specific entry as a straight forward log option.
It can however be inspected to trigger a custom app or custom threat.
Through captive portal the firewall can also provide ntlm user authentication or could be configured to receive syslog from the proxy containing user information
How to Configure Captive Portal
How to Locate the Predefined Syslog Filters in PAN-OS
hope this helps
Tom
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-19-2015 01:52 AM
Hi ascit,
if you just want to identify the user coming from proxy, then there is a way to find out who it is.
Therefor the x-forwarded-for field has to be enabled on proxy and PA.
On PA:
to find out which ip-adress it is look into the URL-log:
to get filled the URL-log you need the URL-license. Maybe this result is not what you need but that is what is possible right now.
Regards,
Klaus
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-19-2015 03:16 AM
Hi ascit,
if you just want to identify the user coming from proxy, then there is a way to find out who it is.
Therefor the x-forwarded-for field has to be enabled on proxy and PA.
On PA:
to find out which ip-adress it is look into the URL-log:
to get filled the URL-log you need the URL-license. Maybe this result is not what you need but that is what is possible right now.
Regards,
Klaus
- 5227 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect Portal / Clientless VPN does not recognize SAML username after update to 10.1.14-h20 in GlobalProtect Discussions
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions
- Limit User-ID Agent queries to cerain Windows event-IDs in Next-Generation Firewall Discussions
- When web proxy will support XFF header insertion and web cache ? in Web Proxy Discussions
- Global Protect and User_ID/Group Mapping in GlobalProtect Discussions



