- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
[ICMP Covert Channel] Allow only ICMP Ping packet that has specific payload.
- LIVEcommunity
- Discussions
- General Topics
- Re: [ICMP Covert Channel] Allow only ICMP Ping packet that has specific payload.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
[ICMP Covert Channel] Allow only ICMP Ping packet that has specific payload.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-05-2019 05:20 PM
Dear all,
I am using PA-8.0.0-ESXi virtual machine and I am trying to prevent covert channel communication using ICMP Payload.
For example, as captured using Wireshark, the default ICMP type 8 (Echo request) for Windows machine is abcdefghijklmnopqrstuvwabcdefghi or \x 61 62 63 64 65 66 67 68 69 6a 6b 6c 6d 6e 6f 70 71 72 73 74 75 76 77 61 62 63 64 65 66 67 68 69 x\ in hexadecimal. I only want to allow ICMP packet that has a specific payload pattern to go through the firewall. Therefore, other ICMP packet that has random payload value will be blocked.
Is there any way to do that on Palo Alto Firewall? I have tried to define custom applications with signature but I cannot get it working. I think I am missing something.
Any help would be appreciated.
Thank you,
Sincerely,
Bagus Hanindhito
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2019 11:58 AM
Hello,
So are you saying when you created a security policy that allowed 'ping', that policy also allowed data to be exfiltrated?
Please advise,
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2019 12:04 PM
What I mean is that the ping packet can contain a payload which can be set randomly. If we allow the ping to pass the firewall, someone can use the payload part of the ping packet to transfer the data in a covert channel. From outside, it is just an ordinary ping packet but with a payload that is designed to silently establish a communication channel with the outside world.
Therefore, I would like to keep the ping pass the firewall with an exception. If the payload does not match the standard payload for Windows ping or Unix ping, then the ping packet will not be able to go through the firewall. If the payload matches the standard payload, then it can go through the firewall.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2019 01:51 PM
Hello,
The PAN knows what the ping packet should look like. If it doesnt match the criteria, it wont be classified as ping and the security policy wont apply. Hopefully you have a eny all policy at the bottom to deny all other traffic.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2019 02:08 PM - edited 05-07-2019 02:08 PM
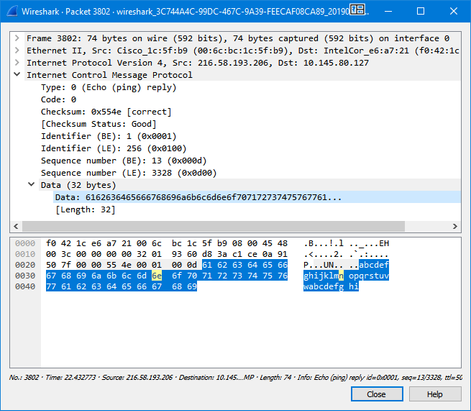
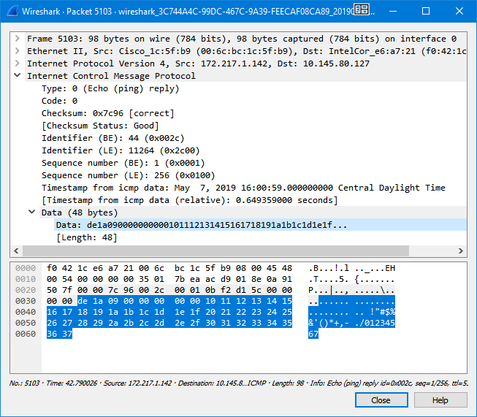
Look at two ping packets below.
1. This ping packet is generated on Windows by typing ping google.com in command prompt. Please pay attention to the Data (32 bytes) highlighted below.
2. This ping packet is generated on Ubuntu by typing ping google.com in bash shell. Please pay attention to the Data (48 bytes) highlighted below.
Both are valid ping packets and by default will be allowed to get through by the firewall although they have different data inside the packet.
My question is, how do I allow only the first type of Ping (i.e., Windows Ping) and block the second type of Ping (i.e., Ubuntu Ping)?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2019 02:11 PM
Hello,
In this case you might want to create a custom application for the Ubuntu ping and then use a security policy to deny it. However I think ping is a RFC standard so it might generate false postives/negatives? Also just a a security think, I never allow ping outbound or inbound, but thats just me.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2019 02:44 PM
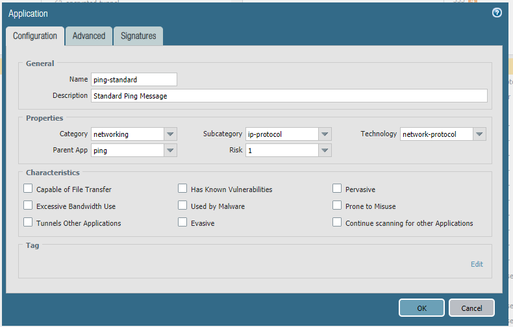
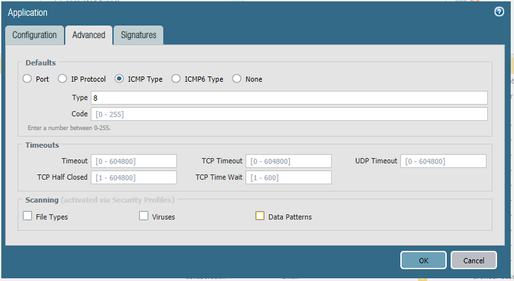
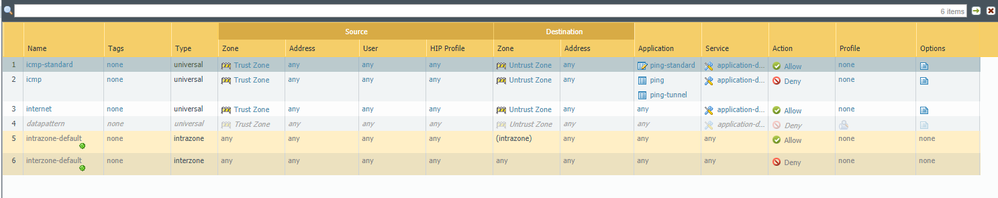
Okay, so firstly I block all of the ping application on my rule.
Then, I define new custom application as follows. I only want the Windows Ping to get through the firewall thus the pattern should be the same as Windows Ping data payload (in hexadecimal).
Then, I added the new application to my rule.
After committing, I see that both Windows ping and Ubuntu ping can still get through. I want to only allow the Windows ping.
Do I set the signature incorrectly for the new apps?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2019 02:44 PM
The best actually is as mentionned by @OtakarKlier : do not allow pings outbound. PaloAlto will identify the ping propery but the App-ID does not care what is inside the ping packet.
With a "harmless" ping it is not even possible to exfiltrate data, there is also software available that allows you to create a VPN connection over the icmp protocol.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2019 02:52 PM
I wish I could just block all of ping. But sadly, I cannot.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2019 02:54 PM
What about just from certain sources? i.e. IP address's or ranges? Perhaps just AD groups (if you use those)?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2019 02:59 PM
@hibagus wrote:I wish I could just block all of ping. But sadly, I cannot.
For what do you need the pings exactly? Maybe for some super-admins who blame you with a not properly working firewall/network when they are not able to ping whatever they want in the internet? Would it be possible that you allow some specific "trusted" destinations (destinations where you know that they don't do anything else than simply replying to the ping)?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-08-2019 09:34 AM
I am currently doing research on modeling security threats that uses ICMP to establish a covert communication channel.
I wish that I can use the deep packet inspection on the Palo Alto Firewall to inspect the ICMP packet.
Any help to define new application signature will be appreciated.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-08-2019 03:21 PM
Unfortunately what you're asking for is not possible. The signatures you can create do not allow you to do a pattern match on icmp-payloads - the decoder probably only checks icmp type and code and nothing else.
The only thing you can do so far is to create a feature request...
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-08-2019 03:36 PM
Thanks for replying.
One more question regarding this topic.
There is an application in Palo Alto Firewall called ping-tunnel as an addition to ping.
I have tried to read the documentation of the ping-tunnel and indeed it uses ICMP for tunneling.
How does the firewall differentiate the original ping and the ping-tunnel?
Maybe it is a good starting point for me.
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-09-2019 06:55 AM
Ho @hibagus
Only paloalto knows how this is done 😛
But I found something which may be useful for you: you cannot create an app to identify linux/windows pings, but you can create an app that checks the length of the ping payload. So maybe it works if you specify a length of 0 (<1) and allow only that. This way not the default pings are allowed but you could make sure that there is no data sent put of your network.
- 12358 Views
- 15 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Need to know different metrics part of network_point_metrics_bw API in Prisma SD-WAN Discussions
- How to trigger a "Response page" on Palo Alto NGFWs using URL filtering & Decryption in Next-Generation Firewall Discussions
- Build in tool to test throughput in General Topics
- Using the REST API to create a bunch of Address Objects in General Topics