- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Inter VLAN routing - best practices/suggestions
- LIVEcommunity
- Discussions
- General Topics
- Re: Inter VLAN routing - best practices/suggestions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2018 08:11 AM - edited 06-20-2018 08:12 AM
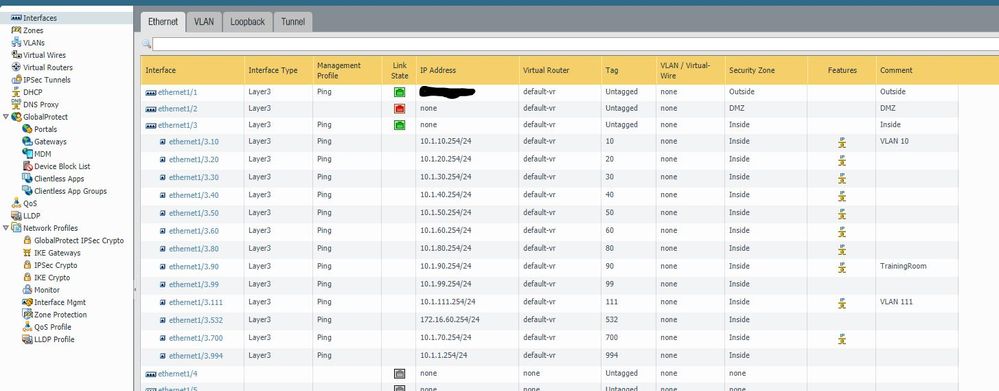
Hi guys, I've got about 7 or 8 VLANs that segregate my various departments. I want to inspect the traffic that goes from these VLANs to my server VLAN. What's the best way to do that? The only article I could find suggests creating a zone for each department. They are all currently configured as Layer3 subinterfaces on the same VR but this isn't production yet so I can move stuff around if need be.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2018 10:58 AM
Not that I'm aware of, as it all kind of depends on your general enviroment. You should be able to build a half decent config looking at what's currently allowed in the ASA however, the migration tool can assist with this in a rough fasion. System owners should have a rough idea of what they need open for internal clients accessing the server VLAN.
Depending on the security implications you could simply allow all traffic from the 'Inside' to the 'Server' zones and vise versa; as that is likely what you are doing now based on your configuration. You then have time to build out legitimate security policies and place them above your 'any' rule; once that 'any' rule is only getting hit by unknown or acceptable levels of traffic you simply remove it and let the policies you built out control traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2018 10:17 AM
You would either do what the article said and create a zone for each department; or you would override the intra-zone default security policy to 'deny' and build out security policies to permit what is required. Easiest solution from a maintenance perspective is going to be creating new zones.
One option as well is to create 1 sole additional zone specifically for your 'server' VLAN. You would then have your 'Inside' zone and your server VLAN interface would belong to the 'Server' zone. Therefore any traffic between the Server VLAN and the others would require a security policy.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2018 10:40 AM
Thanks for comment. Is there any kind of list with "typical" ports or applications (I guess in the case of the PA as it is app aware) that one can reference to help make this process go a little faster and smoother? For example I'd want DNS, DHCP, http/https as well as file server services to be allowed but the only way I can think of doing this is by doing a DENY and just slowly go through the logs and ALLOW each service/application that I want.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2018 10:58 AM
Not that I'm aware of, as it all kind of depends on your general enviroment. You should be able to build a half decent config looking at what's currently allowed in the ASA however, the migration tool can assist with this in a rough fasion. System owners should have a rough idea of what they need open for internal clients accessing the server VLAN.
Depending on the security implications you could simply allow all traffic from the 'Inside' to the 'Server' zones and vise versa; as that is likely what you are doing now based on your configuration. You then have time to build out legitimate security policies and place them above your 'any' rule; once that 'any' rule is only getting hit by unknown or acceptable levels of traffic you simply remove it and let the policies you built out control traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2018 11:15 AM
Oh I like that idea... Maybe start with a couple of my more tech-friendly users as well just to get a head start.
Thanks for the suggestions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-21-2018 07:48 AM
To add to BPry's recommendation, if you know the servers that will see traffoc (You probably do) you can implement rules for them that allow any application and let it run 30-60 days. You can then use the migration tool to assign app-ids from he logs (I do not have the instructions handy, but they should be out there) - I've done this a number of times with great sucess
Alternately, I've used Splunk to map the most common applications and endpoints from the logs, to begin building specific rules from that
- 1 accepted solution
- 11788 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Conditional Advertisement / BGP Failover with Dual ISP — How to Remove ISP1 Routes on Internet Loss? in Next-Generation Firewall Discussions
- Problem with downloading PAN OS in General Topics
- linux /etc/iproute2/rt_tables filled with 231 pangp.include and 232 pangp.exclude in GlobalProtect Discussions
- Prisma Access with ECMP in Prisma Access Discussions
- SCM Compatibility in General Topics