- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
IPSec / returning ESP packets dropped when terminating interface is in a different zone
- LIVEcommunity
- Discussions
- General Topics
- IPSec / returning ESP packets dropped when terminating interface is in a different zone
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
IPSec / returning ESP packets dropped when terminating interface is in a different zone
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-12-2019 03:20 AM
Hi all,
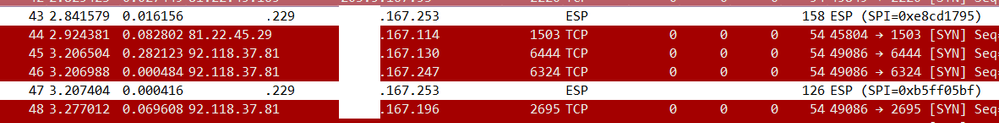
I have an IPSec tunnel connecting to an old SSG. Tunnel came up successfully and SSG can see the traffic and is returning correctly into the tunnel. However PAN's decrypt counter remains 0. When i did a packet capture, the returning ESP packet is dropped shown below Frame 43 and 47:
The setup i have is:
- eth1/1 - ISP WAN in zone "outside"
- loopback.1 - Public IP advertised by ISP in zone "dmz"
- IPSec create similar to https://blog.webernetz.net/ipsec-site-to-site-vpn-palo-alto-juniper-screenos/
- tunnel.1 - in zone "trust"
- both ends of tunnel is in "trust"
- IPSec statuses all showing green
- has policy from "outside" to "dmz" allowing any any from the two terminating IPs
When i change loopback.1 to zone "outside", everything works. Any suggestion or help is very much appreciated. Thanks in advance.
| Model | PA-820 |
| Software Version | 9.0.2-h4 |
Thank you,
Jason
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2019 02:51 AM
I'd recommend leaving the loopback on the untrust as that's the actual place where you want to terminate tunnels
Is there a specifc use case for having it in DMZ on a loopback (just curious)
have you captured any global counters? these could tell you what exactly is causing the drop
> debug dataplane packet-diag set filter match source <src> destination <dst> > debug dataplane packet-diag set filter match source <dst> destination <src> > debug dataplane packet-diag set filter on > show counter global filter delta yes packet-filter yes (establishes the delta start) > show counter global filter delta yes packet-filter yes
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2019 06:36 PM
Thanks @reaper
the only reason is that address (subnet) is supposed to be a DMZ range.
I just found this https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClsiCAC
CauseThe issue is the tunnel terminates on an interface in a zone different from where the ESP (Encapsulation Security Payloads) packets originate.
i'm curious as to why it is design this way.
and correct me if i'm wrong all IPSec tunnels have to terminate on the same zone as the one on the Internet?
i'll get those global counters just to confirm the exact drops and update later.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2019 04:52 AM - edited 07-19-2019 04:53 AM
if you can set the loopback in an IP range that is not configured on the external interface, this issue will likely not happen
I suspect there is a conflict when the packet is received, the destination zone will be determined by using the routing table, the external interface is the actual owner of the ip subnet
if you split up the external subnet and set one segment on the DMZ interface and then set up the loopback in that subnet with the dmz zone, there should not be an issue
PANgurus - Strata specialist; config reviews, policy optimization
- 8266 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Max number of units (aeX.Y subinterfaces) supported under a single AE interface? in Next-Generation Firewall Discussions
- How does the Azure Virtual Network discovers that there is Palo Alto Gateway Interface in VM-Series in the Public Cloud
- 'Redistribution Agent XXX(vsys1): details: close connection to agent in General Topics
- ION 1200 S Cellular Interface in Prisma SD-WAN Discussions
- Migrate model FW to virtualwith panorama for policies (recommended procedure) in General Topics