- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Moving from a single PA500 to HA pair of PA820
- LIVEcommunity
- Discussions
- General Topics
- Re: Moving from a single PA500 to HA pair of PA820
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Moving from a single PA500 to HA pair of PA820
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-31-2017 01:27 PM - edited 05-31-2017 01:30 PM
As the subject states we are single PA500 shop now moving to Dual PA820 in HA.
What can I expect when moving to this type of setup coming from a single FW setup.
Is there anything I need to look out for any "Gotchas"? So far I know I am using 5 copper ports on the PA500 and the PA820 only has 4 so I know I will need a module. Can anyone think of anything else I may encounter, anything related to Policies, Objects, VPN config anything that you guys can think of.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-31-2017 01:49 PM
I assume that you are going to run in an Active/Passive setup. Not much really changes and there are not really any additional steps that you have to do to keep things working correctly. As far as VPN goes GP clients usually transfer over during a failover even fine, where IPSec site-to-site tunnels that I have generally need a few minutes to re-key with the other unit to start passing traffic again.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-31-2017 02:14 PM
Thank you very much for the response, how does HA handle user traffic passing out if one of the firewalls dies,
Do I need to flush arp anywhere or do they keep session tables to some degree?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-31-2017 10:01 PM
For IP addresses configured on interfaces, you shouldn't need to clear arp due to the firewall performaing gratuitous arp after an HA event.
Gratuitous arp is not done for NAT addresses so you might need to clear on external routers if you are doing NAT.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-31-2017 11:49 PM
@rmfalconer Hi,
If the Palo has DNAT configured on the external interface for let's say an external range of IPs, it will not send a GARP after failover?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2017 12:28 AM
@rmfalconer: the PA does proxy arp for IP addresses used in NAT policies
The HA cluster uses a virtual MAC address which is moved over to the active member if there is a failover event, so the GARP will trigger any switches to learn where the MAC is located and any upstream devices will already have a mapping for the NAT addresses to the virtual MAC. if an IP is not known yet, the active member (wether primary or secondary) will simply proxy arp for the IP using the virtual cluster MAC
@CTaveras: the HA cluster (via the HA2 interface) shares all information regarding active sessions (tcp sequence, NAT, QoS, content scanning status,...) , so if there is a failover event all sessions are immediately 'active' on the secondary firewall and can continue as if nothing happened
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2017 01:14 AM - edited 06-01-2017 02:42 AM
Ok so floating MAC address shared between the HA members. All ARP requests for any DNAT IP address that Palo owns will be replied by an active member with its floating MAC address?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2017 01:42 AM
correct
- a HA cluster switches to a floating MAC on all interfaces (based on the cluster ID)
- upon HA failover GARP is sent out for all interfaces
- PA performs proxy ARP for any IP used in NAT policies (in case of HA, the floating MAC is shared)
so normally all connected devices will automatically switch everything over to the active HA peer
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2017 01:46 AM
Such a clear answer! Thanks as always
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-02-2017 05:51 AM
First thank you all for the info/Insight great info!!
A few more quetions
1. Any benefit going Active/Active over Active Passive, Pros and cons?
2. We have the public and private keys of a trusted Certificate Authority imported into the firewall such that the firewall can issue certificates as that CA. I’m assuming exporting and importing the config won’t also migrate over certificate information such that we would have redo those configurations on the new firewall.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-02-2017 05:58 AM - edited 06-03-2017 03:15 AM
1) No benefits, l know it adds only complexity through l never done it before. Only useful as a temp fix while you dealing with the asymmetric routing on the network.
2) Keys and certs will be migrated (keys are encrypted with the master key on palo)
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-02-2017 09:23 AM - edited 06-02-2017 09:25 AM
@CTaveras Just be aware that PAN-OS 8.0.x is the minimum OS version for the new platforms 220, 800 series and 5200 series.
Other than that, I agree with some of the other comments such as:
1. Be aware of potential proxy arp configuration on upstream routers. it may break the NAT functionality. If you have static or proxy arp on upstream routers make sure to remove it before starting to test especially the NAT rules.
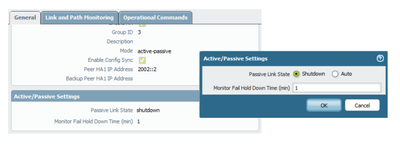
2. Make sure to configure the Active/Passive Settings as Auto instead of Shutdown. The reason for that is because in the shutdown state, upstream and downstream devices connected to the passive device will not see a valid path until the passive firewall becomes active. That may be a little frustrating because the failover may be delayed a few seconds longer, which may be unnaceptable for some businesses.
3. Also be aware of the preemption feature. If your firewalls are connected to two different ISPs and both have different bandwidths, typically you want the firewall connected to the higher bandwidth to always be the Active firewall in the HA pair. In this case you may want to enable the preemtion feature and configure a timer on it.
For more advises on HA optimization and configuration please refer to the following document:
I hope this helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2017 01:04 PM
We will def have 2 ISP but using both simultaniously.
Some one mentioned something about Virtual MAC when in HA...I assume that was for the External interface?
What about the Trusted port does that also get a Virtual MAC?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2017 11:07 PM
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-08-2017 06:23 AM
@acc6d0b3610eec313831f7900fdbd235 I notice that although I set the Passive link state on the Active FW to Auto, the Passive has not sync'd this change.
Is this expected behavior or does the passive device also need this setting? I read the Doc you linked and it doesnt mention anything about the passive device.
- 8069 Views
- 15 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Can Cortex XDR fully substitute for Microsoft Defender Attack Surface Reduction (ASR) rules? in Cortex XDR Discussions
- When setting up HA from a stand-alone...how should I configure LAN ports on the switch? What state are links on the passive node? in General Topics
- Design recommendation for PAN NGFW in AWS in VM-Series in the Public Cloud
- Site to Site IPSEC Clarification in General Topics
- Global Protect authentication happened twice while LDAP and Okta Auth in GlobalProtect Discussions