- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
MS Windows Store Download Troubles
- LIVEcommunity
- Discussions
- General Topics
- MS Windows Store Download Troubles
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
MS Windows Store Download Troubles
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-08-2020 03:47 AM
Dear Community,
I'm looking for the best practice to allow user to download apps over the ms windows store. But sometimes the download is successfully and sometimes i get an error.
Why?
No Decryption on which ip or url?
Which Apps I need to allow - ms-store and others?
I hope you can help me
cu
Wolfgang
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-08-2020 12:15 PM
If this is only happening over the VPN then this is a known issue and is also a Microsoft issue that impacts any and all/other VPN clients. This is fixable with some GPO changes, we made these changes (did not require a reboot) and everything worked with the app store 100% of the time immediately.
I do not have the original post link that I found the fix on but I *think* this is the same fix here: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000PNL5CAO
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-08-2020 12:33 PM
If this is not over the VPN and you are not doing decryption all of this traffic is going to be primarily identified as ms-store, which works with or without encryption.
If this is while you are connected to GlobalProtect then @shawnhafen is 100% correct and you'll want to make the Group Policy changes described in the KB article so that this starts functioning correctly again.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-08-2020 10:06 PM
Hi BPry and shawnhafen,
Thanks but thats not my question/solution. I also had Troubles with Downloads/Updates over normal lan. Sometime I can download apps.
I think the problems are the palo settings - no decryption, apps - but which one?
I hope you understand my correct and you have other ideas?!
Thx
cu
Wuff
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2020 07:20 AM
If it's happening even on the LAN connection it's more than likely a security rulebase problem.
First and foremost make sure that you have logging enabled on your interzone-default policy, or are otherwise capturing denied traffic to the untrust (internet) interface. By default you won't have logs for this, and if you aren't allowing required traffic you may not have the associated threat logs to look at. Store traffic should be getting identified as ms-store and ssl.
You mention no decryption but I'm unsure exactly what you mean on this. Are you not performing decryption on traffic at all, or are you wondering what URLs should be set to not decrypt? By default, the firewall already has most of what you will need present in the ssl decryption exclusions automatically.
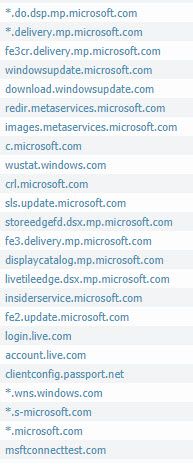
The following URLs can also be excluded for decryption to prevent any store related issues:
- login.live.com
- account.live.com
- clientconfig.passport.net
- wustat.windows.com
- *.windowsupdate.com
- *.wns.windows.com
- *.microsoft.com
- *.s-microsoft.com
- msftconnecttest.com
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2020 10:33 PM
Hi BPry,
Thanks for your Response 🙂
I allowed app ms-update and ms-store. I filled in under ssl-decryption exclussion following urls:
I think it works..
Thank you
cu
Wolfgang
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-10-2025 08:55 AM
Thank you, we've been having issues with the ms-store blocking downloads and adding these additional URLs to the no-decrypt list finally fixed the issue!
- 14265 Views
- 6 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect VPN Client windows 11 crash in GlobalProtect Discussions
- False positive detection (Generic.ml) - Sunshine in VirusTotal
- Windows-Update configuration PA-1410 in Next-Generation Firewall Discussions
- Flood protection (SYN) blocking/failing file downloads in Next-Generation Firewall Discussions
- Whitelist our backup software in Cortex XDR Discussions