- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
NAT rule to change internal IP to another on same subnet?
- LIVEcommunity
- Discussions
- General Topics
- NAT rule to change internal IP to another on same subnet?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 09:29 AM
Hi folks,
I have created a internal zone IP address I want to use as generic for FTP communications 192.168.1.9.
I want to NAT this IP to our current FTP server 192.168.1.19. This way when our FTP server changes we just change our NAT rule rather than the rest of our partner companies firewalls, routes, etc.
I've created a DNAT rule and able to ping 192.168.1.9 and get a response from 192.168.1.19, but unable to connect via ftp.
I've done this before successfully between network zones (subnets) but not on the same zone (subnet) so far.
Any suggestions?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2017 07:37 AM
For it to work from outside you need:
From zone - Untrust
To zone - Untrust
Destination Address - 96.68.102.139
Service - create new tcp-21 with protocol tcp and port 21
Destination translation - 192.168.32.19
NB! Place this new wan rule above WebServer1 rule because otherwise WebServer1 will NAT all ports to 192.168.1.9
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 09:37 AM
Hey do I understand correctly that clients and FTP server are both internal in 192.168.1.x subnet?
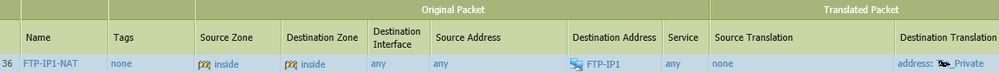
Can you show your DNAT rule?
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 09:42 AM - edited 09-13-2017 09:49 AM
Thanks. Maybe I should create a source bi-directional rule. But do not want to disturb regular traffic to 192.168.1.19.
FTP-IP1 = 192.168.1.9
Private = 192.168.1.19
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 09:52 AM
You have to add source nat also to the rule.
Traffic must source from firewall internal IP.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 10:19 AM
Thank you. Do you know if that would effect communications with clients that are currently connecting and using IP 192.168.1.19 directly?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 10:49 AM
This does not affect users connecting directly to .19
Issue is that if client from 192.168.1.x network connects to 192.168.1.9 that is DNATed further to 192.168.1.19 then reply packet is sent directly to original source IP because 192.168.1.19 identifies that source is in it's own subnet and does not need to send this packet to gateway.
Client who received reply packet from 192.168.1.19 will drop it because it does not know anything about 192.168.1.19 as client initiated connection to 192.168.1.9
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2017 12:25 AM
I will come back to this one. Unfortunately other projects, tasks, and priorities are totally interupting what I was doing here, but still need to confirm. I will schedule some time soon to finish this thread.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-03-2017 09:36 AM
Thanks Raido,
I would like to resolve this thread this week.
I have my DNAT rule in place and I can ping 192.168.1.9 (VIP) and get a response from 192.168.1.19 (FTP server), but ftp does not work when I try ftp://192.168.1.9.
How would I set up the correct SNAT rule for this to work? I just tried this SNAT rule, but not working so far.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-03-2017 02:47 PM - edited 10-03-2017 02:50 PM
Your original DNAT rule was fine.
All you were missing was Source NAT field.
Do not change other fields in your initial rule.
You need to have both Source NAT and Destination NAT configured in this single NAT policy.
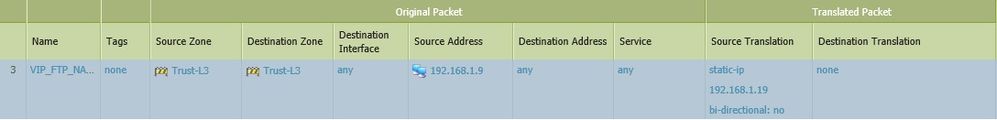
Assume that your firewall internal IP is 192.168.1.1
In this case Source NAT is from this 192.168.1.1 IP
From zone - Trust
To zone - Trust
Source address - Any
Destination address - 192.168.1.9
Source translation - Dynamic-ip-port 192.168.1.1 (assuming this is your fw internal IP)
Destination translation - 192.168.1.19
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-09-2017 05:27 AM - edited 10-09-2017 05:51 AM
Thanks Raido,
That is working for me internally now. Still trying to wrap my head around it. 🙂
However, it does not work externally. I have a security rule that opens everything to my public IP. I have a NAT rule that translates public IP to 192.168.1.9 (and a source Dynamic IP and port to external interface IP). Neither http or ftp work, just times out. (I have a web server and ftp server here)
Curious if you comments about external connectivity?
Thank you for your guidance...
Internet = 96.68.102.140 (one of my public IPs I use for internet access)
Copperfield = 192.168.1.1 (IP of internal LAN Interface)
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2017 07:37 AM
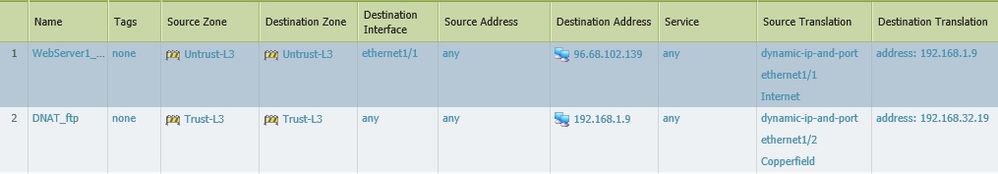
For it to work from outside you need:
From zone - Untrust
To zone - Untrust
Destination Address - 96.68.102.139
Service - create new tcp-21 with protocol tcp and port 21
Destination translation - 192.168.32.19
NB! Place this new wan rule above WebServer1 rule because otherwise WebServer1 will NAT all ports to 192.168.1.9
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-16-2017 08:20 AM
Wow, thanks Raido!
I starting to get it. I need to spend more time in wireshark to understand it better.
Thank you so much for your responses. Creating this internal "VIP" will help in communicating a long term IP to our IPSec VPN connections that will allow us to change servers and IPs without the need to have our partners update their rules, etc.
Final NAT rules.
- 1 accepted solution
- 8194 Views
- 11 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Rapid connecting/disconnecting after some time in GlobalProtect Discussions
- PA Global Protect in GlobalProtect Discussions
- Prisma Access with ECMP in Prisma Access Discussions
- Request Advice – BGP Failover Route-Based IPsec VPN With WatchGuard (WG) in Next-Generation Firewall Discussions
- Strata Cloud Manager with NGFW in Strata Cloud Manager