- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
PA incorrectly matching rule, lets C&C traffic out
- LIVEcommunity
- Discussions
- General Topics
- Re: PA incorrectly matching rule, lets C&C traffic out
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
PA incorrectly matching rule, lets C&C traffic out
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-18-2013 09:00 AM
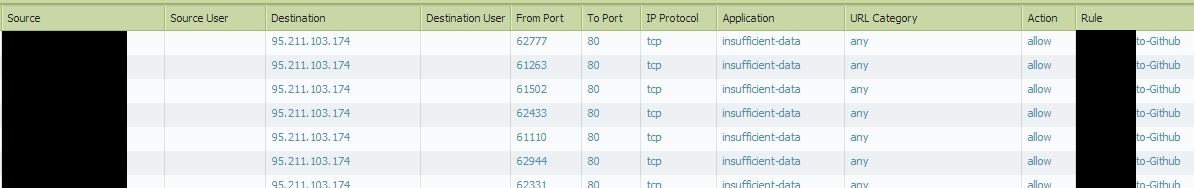
One of our other IDS tools detected C&C traffic outbound. After further investigation, this traffic was allowed out through the Palo Alto because it matched on a rule that should have allowed ONLY the App-ID "github". The App-IDs that the PA was detecting and allowing were...
-incomplete
-insufficient-data
-non-syn-tcp
...why did this C&C traffic match this rule which specifies ONLY the "github" App-ID?

- Labels:
-
App-ID
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-18-2013 09:19 AM
There are a few things that need to happen for an application to be identified, mainly for TCP traffic there needs to be at least the TCP handshake and another packet or more.
"non-syn-tcp" is blocked by default, so your firewall seems to have that enabled. Check the Device > Setup > Sessions tab. If you've got it set to allow, the firewall will let a connection be established, and if it's possible to identify the traffic it will do so.
"incomplete" is traffic that did not actually complete the TCP handshake. That you likely don't have to worry about.
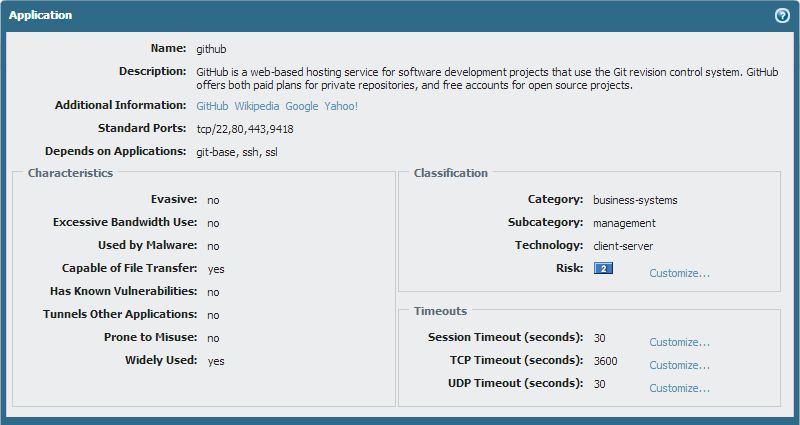
"insufficient-data" is traffic that has not had enough packets to identify what it is. Some traffic can be identified easily on the 4th packet (web-browsing, for example has an HTTP GET or similar as soon as the TCP handshake is done), but other traffic may take some time to identify. In the case of github, if it's going on port 80 as your traffic log shows, there has to be some additional traffic before it can be identified. It will have to go through git-base initially, and then be identified as github after git-base is identified.
In your screenshot, it never gets that far. Likely there are only a couple packets, which is common for C&C traffic, and so the firewall is unable to identify it positively as github by the time the traffic is done.
My recommendation is to disable non-syn-tcp in the session to start, but that may impact other applications so check to see why that was enabled to begin with. The rule in your screenshot doesn't have the last 2 columns, so if there is no AV/Vuln scanning, you'll want to add that as well. Beyond that, if you want to restrict the rule further by adding a URL category or a specific URL for the destination traffic, that may help.
Best,
Greg
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-18-2013 09:21 AM
Hello jambulo,
Yes this is expected for incomplete, insufficient data and non-syn-tcp. Before the 3-way handshake completes and the session's application is detected as incomplete the security policy lookup for the session will match the first security policy which matches all attributes except application. Once the 3-way handshake completes and the firewall sees a data packet which can be used to identify the app the session will shift the application to the appropriate value and do another security policy lookup.
If a session never completes the 3-way handshake the application will stay as incomplete and the session will be logged after the timeout with the policy which the session first hit.
Maybe an easier way to explain it. When the first TCP packet is received (SYN), the firewall must setup a session. Since the application can not be detected on a TCP session until at least one data packet traverses the device the application will be incomplete. For the firewall to determine if it should even allow the SYN packet through it must do a security policy lookup.
Because the application is not known when the SYN packet is received the application portion of the security policies can not be applied. As a result, the security policy lookup is performed against the 6 tuples of the session, source and destination IP and port, ingress interface (actually zone) and protocol. The first policy which matches these 6 tuples will be used to allow the SYN and any additional packets that traverse the firewall before the application is identified.
Hope that helps!
Thanks and regards,
Kunal Adak
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-01-2013 10:06 AM
Actually any ip based filters should be able to kick in BEFORE the handshake is completed.
- 4961 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Windows-Remote-Management & Implicit Use of Web-Browsing in General Topics
- Questions about PAN-303959 in General Topics
- Issue with call recording (flow_predict_convert_rtp_drop) in Next-Generation Firewall Discussions
- wrong traffic matching rule in General Topics
- Admin GUI Login Fails on WAN Interface - Slow Load & "Single Sign-On" Error on PA-410 in Panorama Discussions



