- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Palo Alto Layer 2 bridging
- LIVEcommunity
- Discussions
- General Topics
- Re: Palo Alto Layer 2 bridging
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-24-2017 01:04 PM
Any idea on when or if PAN is going to produce the functionality to do layer 2 bridging (example, traffic on vlan 300 would be directed to vlan 3000...etc? Right now the function only seems to be possible when in conjunction with a physical interface per bridge which isn't scalable for lots of vlans like a DC. Another option is enabling the function to bridge in vwire mode 2 different vlan tags.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-02-2021 10:06 PM
I Found The Solution :
I am using topologi Like this. In Core Router i have VLAN10 with network 172.25.10.0/24. Between Distribution Switch and Server Switch I Installed Palo Alto to translate VLAN10 to VLAN1010. My Server Using VLAN1010 172.25.10.10 and still can connected to Gateway Core Router 172.25.10.1 with VLAN10.
1. Create Sub Interface in 2 Physical Interface with different vlan tag like this picture. In this Picture i translate vlan 10 to vlan 1010 with same network 172.25.10.0/24
2. In All Sub Interface create Vlan Group like this picture.
3. And result of the Vlan Group. In VLAN Group we can see there are two sub interface with different vlan tagging.
4. You can see in picture at point 1, I give two different zone at sub interface ethernet1/3.10 and ethernet1/4.1010.
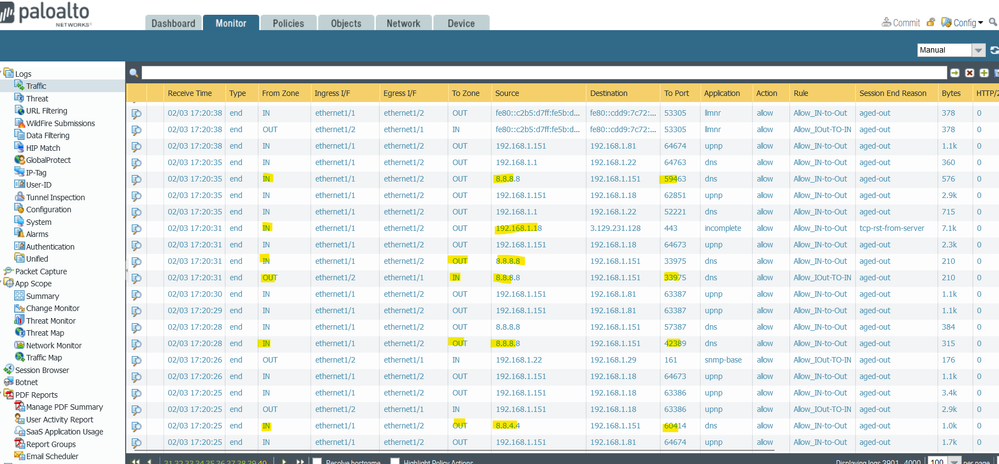
5. And the result we can inspect traffic inggress and eggress from ethernet1/3.10 and ethernet1/4.1010 like this picture. Look at hit count on policy rule number one. Same Network IP with Different Zone and different VLAN Tagging :
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2017 10:40 AM
This is doable today, by using 802.1q for the two vlans you mention, with subinterfaces. and use the same vlan number for both. In that way, these two vlans are connected. No redirect. No rewrite. But connected together.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2017 01:00 AM
This has been possible for a long time already, please check out this article : Getting Started: Layer 2 Interfaces
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-28-2017 12:54 PM
The problem I found with this however was the dependency on each bridge/rewrite interface group is per physical interface. For example if I create a vlan bridge between 2 different tagged sub-interfaces (aka e1/1.200 and e1/1.300) I have to create the bridge with not only .200 and .300, but with the physical interface e1/1 as well. This limits the scalability of this to the number of pyhsical interfaces available. It would be great if you could create bridges without the physical interface dependency.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-02-2021 10:06 PM
I Found The Solution :
I am using topologi Like this. In Core Router i have VLAN10 with network 172.25.10.0/24. Between Distribution Switch and Server Switch I Installed Palo Alto to translate VLAN10 to VLAN1010. My Server Using VLAN1010 172.25.10.10 and still can connected to Gateway Core Router 172.25.10.1 with VLAN10.
1. Create Sub Interface in 2 Physical Interface with different vlan tag like this picture. In this Picture i translate vlan 10 to vlan 1010 with same network 172.25.10.0/24
2. In All Sub Interface create Vlan Group like this picture.
3. And result of the Vlan Group. In VLAN Group we can see there are two sub interface with different vlan tagging.
4. You can see in picture at point 1, I give two different zone at sub interface ethernet1/3.10 and ethernet1/4.1010.
5. And the result we can inspect traffic inggress and eggress from ethernet1/3.10 and ethernet1/4.1010 like this picture. Look at hit count on policy rule number one. Same Network IP with Different Zone and different VLAN Tagging :
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-15-2021 04:25 PM
This screen shot is missing some important details. Line 2 shows IP 172.16.15.92 sending to 172.25.10.10 and it is allowed. Was this a successful 2 way communication? When the source and destination networks are different, the source arps for its default gateway. 172.25.10.10 would not be the gateway unless this was a /8 mask. I understand how this can work if all devices are on the same subnet. PAN is just modifying the tag and passing arp, and everything else to the other interface. Should that second session be blocked out to avoid confusion or am I missing something?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-08-2021 01:53 AM
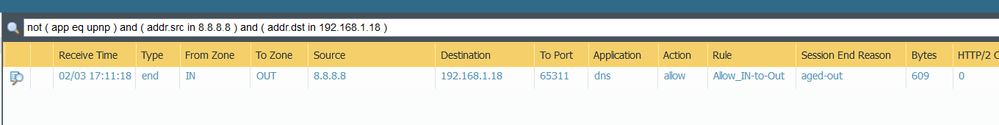
You must understand how it works from what I describe and please try it yourself. The second line is the rule that allows 172.16.15.92 access to 172.25.10.10. if you want 172.25.10.10 to be able to access 172.16.15.92 then you have to open access in reverse as in the third line. One more thing, even though 172.25.10.10 and 172.25.10.1 are on the same network they cannot ping each other and access service ports if they are not given permission because they are in different zones (remember this is a bridging vlan with different interfaces and zones). You have to be more careful and better understand the picture that I provide. Please do the simulation in your own lab and you will understand.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-29-2022 07:12 AM
I don't think Gun-Slingers question is answered here. The bridging shown is dependent on physical interfaces, which are limited. In a situation where all traffic is moving across one Aggregate Ethernet trunk, bridging would need to take place inside the firewall. As the OP indicated, supporting a data center would not be practical using physical interfaces for bridging. Our situation is the same, and it looks like we may need to use two Aggregate Ethernet interfaces, with common VLANs between different Zones, pruning VLANs as necessary on one of the AE interfaces.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-04-2023 04:30 PM - edited 02-04-2023 05:22 PM
Hello @ismunandi thanks a lot for your time and for your colaboration.
I confirm that the key point in layer 2 is to create the Network-Vlans and integrate both interfaces in and out ok, this in use of "Layer 2 interfaces" but then vwire with subinterfaces does not support retag or vlan translation? Only interfaces in layer 2? So it is not compatible vlan translation/retag vlan with taged vlan on Vwire with subinterfaces ?
Now a question I saw something similar with a client recently with PortChannel/subinterfaces-interfaces layer 2" It does not happen or does not happen to you that in the traffic-log-monitor, you see both the client to server and server to client flow of the session, the normal thing is only to see the c2s flow, save go to the browser session, but I have seen that the retag or address translation causes this, that you see example (and I do not mean log Star anda end policy) you see of a connection, the normal thing is to see: 10.10.10.10 to 192.168.1.100 SPORT 45650 to SPORT 443. The normal but in environments that I have seen with retag or vlan translation to see both flows in the traffic log is 10.10.10.10 to 192.168.1.100 SPORT 45650 to dport 443 and vice versa 192.168.1.100 to 10.10.10.10 SPORT 443 dport 45650, is the different behavior that I see with retag or vlans translation in production.
I have seen this behavior with Layer 2/Portchannel/Subinterface and applying a Retag/Translation ( Network-VLANs ).
Switch===IN==Subinterfaces VLAN TAG 100,200,300,400 ====PALO-ALTO-FW=====OUT==VLAN TAG 101,201,301,401.
Networks-VLANs: VLAN_100_101: AE1.100 and AE2.101 subinterfaces, VLAN_200_201: AE1.200 and AE2.201 subinterfaces, VLAN_300_301: AE1.300 and AE2.301 subinterfaces, etc.
In this environment with Translation-VLAN-Retag, it happens that in the traffic-monitor log, they look different, which does not happen with routed interface, with vwire or layer 2, without retag, but with retag/translation, as you exemplify this with an existing implementation that already has a client, you see in the traffic logs for a single connection, a single, single connection, where you typically only see 10.10.10.100 to 10.10.100.100 sport:45650 to dport:22, which It is normal to only see the flow from client to server, but in this case with retag you see a single connection, you see both flows in the traffic log (not session browser, I mean log traffic monitor), that is, you see c2s flow: 10.10.10.100 to 10.10.100.100 sport:45650 to dport:22 and also the s2c flow 10.10.100.100 sport:22 to 45650. This topic really has me very confused, because normally in the traffic log you only see how I say the flow c2s, but with ambient retag you see cs2/s2c.
Examples:
Thanks a lot
Cheers
- 1 accepted solution
- 22240 Views
- 8 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Request for VPN Capability Enhancement on Palo Alto Networks Firewalls in Next-Generation Firewall Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Unable to Ping Palo Alto Interface – Connectivity Appears One-Sided in Next-Generation Firewall Discussions
- Struggling to Unset Virtual Router from Interface via API – Manual Works, API Always Fails in General Topics
- When web proxy will support XFF header insertion and web cache ? in Web Proxy Discussions