- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Problem configuring rules for our mail server using anti spam cloud service
- LIVEcommunity
- Discussions
- General Topics
- Re: Problem configuring rules for our mail server using anti spam cloud service
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-08-2018 07:14 PM
Hi
I think I<m not on the right track and search documentation to help. i tried to replicate the logic from my olf checkpoint fw. I guess it is not a good idea.
Please HELP!
My configuration is the following (no real IP addresses)
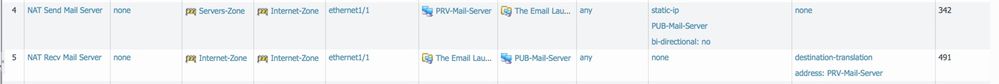
Mail Private Server in a trusted zone (Servers-Zone) PRV-MAIL-SERVER 10.10.5..3 on Interface1/3
The Public Address PUB-MAIL-SERVER 70.34.125.2 (1 of 5 addresses on Interface1/1)
The anti-spam cloud service ANTISPAM-ADDR_GROUP (3 IP addresses range on port 25)
The WebMail Public Addrees WEBMAIL 70.34.125.2 (same as the mail server but port 443) on Interface1/2
I have the following NAT rule for outgoing mails
src-zone : Servers-Zone
dst-zone : Internet-Zone
dst-interface : Internet1/1
src-addr : PRV-MAIL-SERVER
dest-addr : any
Service : smtp
Src-translation: static-ip: PUB-MAIL-SERVER, bidirectional : yes
and the following NAT rule for then incoming mails
src-zone : Internet-Zone
dst-zone : Servers-Zone
dst-interface : Internet1/3
src-addr : PUB-MAIL-SERVER
dest-addr : any
Service : smtp
Src-translation: static-ip: PRV-MAIL-SERVER, bidirectional : yes
The Security Rules are (Outgoing email):
src Zone : Servers-Zone
src Address : PRV-MAIL-SERVER
dst Zone : Internet-Zone
dst-Addr : ANTISPAM-ADDR_GROUP
application : smtp and Service : application-default
Action : Allow
The Security Rules are (Incoming email):
src Zone : Internet-Zone
src Address : ANTISPAM-ADDR_GROUP
dst Zone : Source-Zone
dst-Addr : PRV-MAIL-SERVER
application : smtp and Service : application-default
Action : Allow
I can send email from the mail server to gmail and the action is successful and logged
The reply is not working and nothing in the logs.
Thanks,
Michel
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-09-2018 01:06 AM - edited 03-09-2018 01:09 AM
Hi @MichelD
I would deactivate the 'bidirectional' option on your first NAT rule since you're building NAT policy in both directions (you can either do bidirectional, or do 2 policies, 1 for each direction... I recommend doing the 2 policy method as this is more readable and less prone to mistakes)
your second policy needs to be internet-zone to internet-zone, this is because the original packet's zones are determined by a route lookup: the source is located on the internet (0.0.0.0/0) and the original destination is also on the internet (external interface ip)
your destination also needs to be the IP PUB-MAIL-SERVER, not any, the source should probably be the ANTISPAM-ADDR-GROUP (so you only allow inbound NAT from those addresses)
your outbound security policy is fine, but for the inbound security policy the destination IP also needs to be PUB-MAIL-SERVER, instead of the private one
Here's a little article + video about NAT which may be helpful : https://live.paloaltonetworks.com/t5/Tutorials/Getting-Started-Network-Address-Translation-NAT/ta-p/...
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-10-2018 05:45 PM
I would recommend that when you are trying to get this to work, you override the interzone-default policy to enable 'logging-start' so that you can see any traffic that is getting dropped due to your security policy configuration. This will allow you to then build out the security policies as needed.
Both of the security policies that you have displayed are showing hits, and your NAT policies are indicating that they are getting used as well. With the interzone-default logging enabled, you should be able to view the traffic logs and see where exactly things are breaking down.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-09-2018 01:06 AM - edited 03-09-2018 01:09 AM
Hi @MichelD
I would deactivate the 'bidirectional' option on your first NAT rule since you're building NAT policy in both directions (you can either do bidirectional, or do 2 policies, 1 for each direction... I recommend doing the 2 policy method as this is more readable and less prone to mistakes)
your second policy needs to be internet-zone to internet-zone, this is because the original packet's zones are determined by a route lookup: the source is located on the internet (0.0.0.0/0) and the original destination is also on the internet (external interface ip)
your destination also needs to be the IP PUB-MAIL-SERVER, not any, the source should probably be the ANTISPAM-ADDR-GROUP (so you only allow inbound NAT from those addresses)
your outbound security policy is fine, but for the inbound security policy the destination IP also needs to be PUB-MAIL-SERVER, instead of the private one
Here's a little article + video about NAT which may be helpful : https://live.paloaltonetworks.com/t5/Tutorials/Getting-Started-Network-Address-Translation-NAT/ta-p/...
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-10-2018 01:17 PM
I changed the configuration as your recommendations. I also read the article. Since I changed the values. the behaviour is a little bit different, but cannot receive emails. The Send is working.
In the Log/Traffic does not show any information about what's going wrong.
I checked all the adresses with the values in our firewall we are replacing. I also tried different scenarios based on what you explain.
Regards,
Michel
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-10-2018 05:45 PM
I would recommend that when you are trying to get this to work, you override the interzone-default policy to enable 'logging-start' so that you can see any traffic that is getting dropped due to your security policy configuration. This will allow you to then build out the security policies as needed.
Both of the security policies that you have displayed are showing hits, and your NAT policies are indicating that they are getting used as well. With the interzone-default logging enabled, you should be able to view the traffic logs and see where exactly things are breaking down.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2018 08:08 AM - edited 03-11-2018 08:08 AM
@BPrywrote:Both of the security policies that you have displayed are showing hits,
This brings up a good point...Embedded rule usage is a feature set of PAN-OS 8.1.X. I'm not trying to jump and say merely the code base is the issue, but for the sake of stability to a production environment running an established / stable code release would also be a good idea?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2018 08:13 AM
@Brandon_Wertz brings up a rather good point, and one that I kind of didn't think about. While 8.1.0 is released I would hesitate to use it in a production enviroment where you are actually publishing services. So far, I've only deployed 8.1.0 on LAB equipment, and the PA-220s that I utilize for our IT department to make a tunnel back to our main office from their houses.
I'm not going to go as far as to say that 8.1.0 is your issue here, because I don't actually believe it is, but I wouldn't be running 8.1.0 in this capacity just yet.
I just want to stress here though, I don't think 8.1.0 is your actual issue. I think if you do as I stated you'll see something that you aren't allowing in your security policies that is getting denied by the interzone-default policy.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2018 02:54 PM
Thank you everybody for your input.
My problem is now solve. In my case, 8.1 was not the culprit.
Here are my final configuration and working great going through the anti-spam cloud service in both directions.
Line with the (MODIFIED) are the corrections to my original configuration.
To find out what was wrong, I had created an any-to-any temporary (5 minutes max) rule with the risk (i know). So I got the information in the trafic log. Logging is not enabled in the default 2 security rules.
As a documentation, my physical configuration is like that:
My MX records points to the ANTISPAM-CLOUD service.
INBOUND EMAILS ---> ANTISPAM-CLOUD ---> FW ---> MAIL-SERVER (Trueted Zone(
MAIL-SERVER (Trusted Zone) ---> FW ---> ANTISPAM-CLOUD ---> OUTBOUD EMAILS
I have the following NAT rule for outgoing mails.
src-zone : Servers-Zone
dst-zone : Internet-Zone
dst-interface : Internet1/1
src-addr : PRV-MAIL-SERVER
dest-addr : outbound-mail-to antispam solution (MODIFIED)
Service : any (MODIFIED)
Src-translation: static-ip: PUB-MAIL-SERVER, bidirectional : no (Bidirectional=NO)
and the following NAT rule for then incoming mails
src-zone : Internet-Zone
dst-zone : Internet-Zone (MODIFIED)
dst-interface : Internet1/1 (MODIFIED)
src-addr : ANTISPAM-ADDR-GROUP (MODIFIED)
dest-addr : PUB-Mail-Server (MODIFIED)
Service : any (MODIFIED)
Src-translation: static-ip: PRV-MAIL-SERVER, bidirectional : no (Bidirectoional=NO)
The Security Rules are (Outgoing email):
src Zone : Servers-Zone
src Address : PRV-MAIL-SERVER
dst Zone : Internet-Zone
dst-Addr : outbound-mail-to antispam solution (MODIFIED to go through the ANTISPAM)
application : smtp and Service : application-default
Action : Allow
The Security Rules are (Incoming email):
src Zone : Internet-Zone
src Address : ANTISPAM-ADDR_GROUP
dst Zone : Server-Zone
dst-Addr : PUB-MAIL-SERVER (MODIFIED)
application : smtp and Service : application-default
Action : Allow
Thank you again,
Michel
- 2 accepted solutions
- 6388 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect Agent constantly 'Not Responding'. in GlobalProtect Discussions
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- Cortex XDR triggers Code 10 on USB Audio despite exception - Vendor not selectable, need per-device allow without vendor or something in Cortex XDR Discussions
- After the Cortex XDR agent is installed, there is a volume shadow copy issue on the endpoint. in Cortex XDR Discussions