- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
S2S VPN Between PA and Cisco ASA
- LIVEcommunity
- Discussions
- General Topics
- S2S VPN Between PA and Cisco ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
S2S VPN Between PA and Cisco ASA
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-10-2017 02:42 PM
Hello!
I've spent the last 2 days trying to get an IPSec tunnel working between a PAN 200 and Cisco ASA5505 but all my attempts have failed. I am not sure what the issue is and would reall appreciate any assistance to point me in the right direction.
This is a very simply setup. I've configured both sides properly but for some reason the tunnel won't come up. Here are the config of both the PA and ASA:
PA 200:
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-10-2017 04:05 PM - edited 07-10-2017 04:13 PM
Hi,
l am not sure if your Proxy IDs look right (host with /24 subnet mask and the whole subnet from ASA side).
@BPry will be able to help, l am sure 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-10-2017 04:37 PM
Honestly there is a bit here that I wouldn't say is 'right' in the way that I setup site-to-site tunnels, that being said I'm not going to say that the way I configure them is the 'correct' way either. @TranceforLife is correct though your proxy IDs I would say are wrong, I generally would use the actual network ranges, so for example 10.191.0.0/16 or 192.168.100.0/24 and so on.
Without knowing what your configuration actually states the following bugs me a bit on the IKE Gateway configuration; but that's probably just because I can't see the entire device config and it's likely fine.
What does your ike logs say on both devices, that should give you a fair insight into what is actually going on? The easiest way to really troubleshoot any of this is the logs on both devices as it will generally get you pointed in the proper direction.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-10-2017 05:09 PM
A few things I noticed on my end here when looking at your configuration. Although you are not showing the Phase 2 configuration on the PAN side, it is easy to spot how it should look like by looking at your ASA config.
As @BPry mentioned,
Unless there is a specific reason you should not have to specify the Local and Peer ID if the VPN is between gateways with static IP addresses. In other words, unless your two firewalls are using dynamic IP address for the public IP, you should not define a Local and Peer IP whatosever, otherwise, it will mess up the phase 1 negotiation. If that's the case for you, and you really need to use this configuration, make sure that it is also properly defined on the remote side of the connection, in this case the ASA.
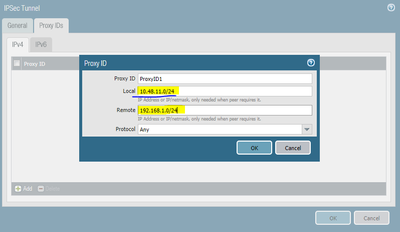
PAN200 - IPSEC Phase 2:
ProxyID1
Local: 10.48.11.0/24
Remote: 192.168.1.0
https://live.paloaltonetworks.com/t5/Featured-Articles/Getting-Started-VPN/ta-p/68931
Also, run the following commands to troubleshoot and if you can post the output that would help us to assist you:
Step 1: Open two Putty sessions to your PA-200. On Screen One, run the follwoing command:
tail follow yes ike tail follow yes mp-log ikemgr.log
Step 2: On Screen two run the following command:
Test Phase 1
test vpn ike-sa
Step 3: Go back to Screen One and read the outputs. if you can copy and post in this thread that would be help us to analyze the messages.
Let us know how it goes.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2017 03:48 PM
Thanks all for the input.
@acc6d0b3610eec313831f7900fdbd235, I tried to use this command but it was inavliad.
tail follow yes ike tail follow yes mp-log ikemgr.log
The PAN's side Phase 2 config is as follows:
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2017 03:54 PM
My apologies for my fat finger. The command is:
tail follow yes mp-log ikemgr.log
The phase 2 ProxyID is a crucial piece of this configuration, and it would be important for us that you ensure it configured properly. The concern is not the Phase 2 paramenters, but the Proxy ID configuration at this point.
That's how your Proxy ID should be configured on the PA-200 side.
Run the above command and post the output for us, then maybe we can shine some light on it for you 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2017 04:07 PM
@acc6d0b3610eec313831f7900fdbd235.. Thanks for the prompt response. I did change the Proxy IDs to what you specified. Here's the output after executing the command:
rbash@PA-200> tail follow yes mp-log ikemgr.log
2017-07-11 16:13:36 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:13:46 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:13:56 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:14:06 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:14:16 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:14:26 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:14:36 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:14:46 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:14:56 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:15:06 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:15:16 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:15:26 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:15:36 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:15:46 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:15:56 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:16:06 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:16:16 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:16:26 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:16:36 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:16:46 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:16:56 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:17:06 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:17:16 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:17:26 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:17:36 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:17:46 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:17:56 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:18:06 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:18:16 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:18:26 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:18:36 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:18:46 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:18:56 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:19:04.175 -0700 ikemgr: panike_daemon phase 1 started, config size 17633
2017-07-11 16:19:04.178 -0700 ikemgr: panike_daemon phase 1 step 2 finished
2017-07-11 16:19:04.329 -0700 ikemgr: panike_daemon phase 1 step 4 finished
2017-07-11 16:19:04.329 -0700 pan IKE cfg phase-1 triggered.
2017-07-11 16:19:04 [INFO]: loading new config from /tmp/.rtoFSH
2017-07-11 16:19:05.130 -0700 ikemgr: panike_daemon phase 1 step 5 finished
2017-07-11 16:19:05.130 -0700 ikemgr: panike_daemon phase 1 config change detected
2017-07-11 16:19:05.130 -0700 ikemgr: panike_daemon phase 1 finished with status 1
2017-07-11 16:19:06 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:19:16 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:19:25.090 -0700 ikemgr: panike_daemon phase 2 started
2017-07-11 16:19:25.090 -0700 pan IKE cfg phase-2 triggered.
2017-07-11 16:19:25 [INFO]: VPN tunnel IPSec_Tunnel:ASA_LAN_TO_LAN(S2S_VPN_To_ASA) changed, deleting SA
2017-07-11 16:19:25 [INFO]: VPN tunnel IPSec_Tunnel:ASA_LAN_TO_LAN(S2S_VPN_To_ASA) changed, deleting SA
2017-07-11 16:19:25.091 -0700 ikemgr: panike_daemon phase 2 finished
2017-07-11 16:19:26 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:19:36 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:19:46 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:19:56 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:20:06 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:20:16 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:20:26 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:20:36 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:20:46 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:20:56 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:21:06 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:21:16 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:21:26 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:21:36 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:21:46 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:21:56 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:22:06 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:22:16 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:22:26 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:22:36 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:22:46 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:22:56 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:23:06 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:23:16 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:23:26 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:23:36 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:23:46 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:23:56 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
2017-07-11 16:24:06 [PROTO_NOTIFY]: notification message 36136:R-U-THERE, doi=1 proto_id=1 spi=7d59e57bd6c54727 c40ffc76ee828c4e (size=16).
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2017 04:22 PM
Hi,
Disable DPD for now. Enable debug mode so we can get more info:
> debug ike global on debug
xxxxxxxxxx> debug ike global show
sw.ikedaemon.debug.global: debug
then
> test vpn ike-sa gateway (your gateway)
then
> tail follow yes mp-log ikemgr.log
Configure debug back to "normal" mode:
> debug ike global on normal
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-12-2017 12:21 PM
What version is PA-200 running?
- 10810 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Panorama API - get content of dynamic address group in Panorama Discussions
- Issue with call recording (flow_predict_convert_rtp_drop) in Next-Generation Firewall Discussions
- Console cable coming with ION 1200S in Prisma SD-WAN Discussions
- Palo Alto CGNAT block issues with GeoBlock rule in Next-Generation Firewall Discussions
- [Proposing Solution] Failure to extract zip file downloaded from ThreatGrid integration command in Cortex XSOAR Discussions