- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Security policy rule - allowing a specific host access to ftp.sophos.com
- LIVEcommunity
- Discussions
- General Topics
- Re: Security policy rule - allowing a specific host access to ftp.sophos.com
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Security policy rule - allowing a specific host access to ftp.sophos.com
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-04-2018 03:12 AM
Hello,
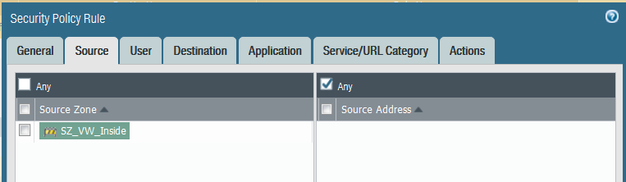
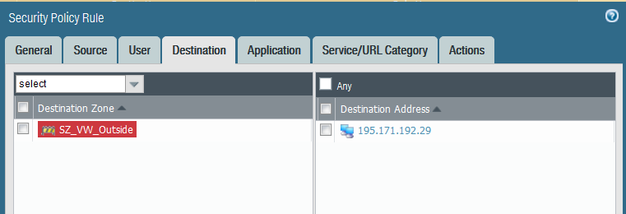
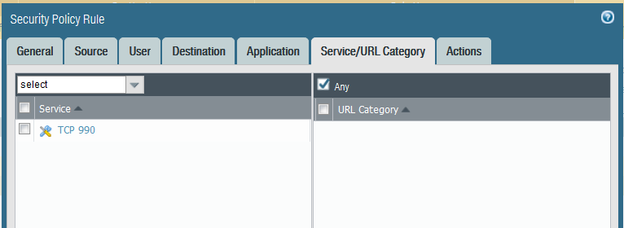
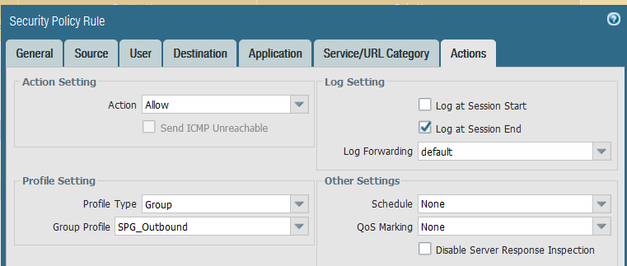
A colleague needs to access ftp.sophos.com (195.171.192.29) using Filezilla as their SFTP client, via TCP port 990. I set up the security policy rule as follows:
They could not log onto the ftp.sophos.com site. The password credentials they used are correct. Is the rule set up correctly? On a Cisco ASA I would have used the following ACL:
access-list aclinside extended permit tcp any host 195.171.192.29 eq 990
Any advice is much appreciated.
Regards,
Roberto
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-20-2018 04:17 AM
Hi DPoppleton,
I set the Transfer Settings to Active in the FTP client (I guess this what you meant), but still not working. I did what Rikkert_Kooy suggested too and still no joy. Is it because the Palo is not configured with SSL decrypt/encrypt?
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-20-2018 06:27 AM
Hi rchung54,
decrypting ssl traffic is not strictly needed to make this connection possible. I have configured passive ftp with explicit ssl in this way before.
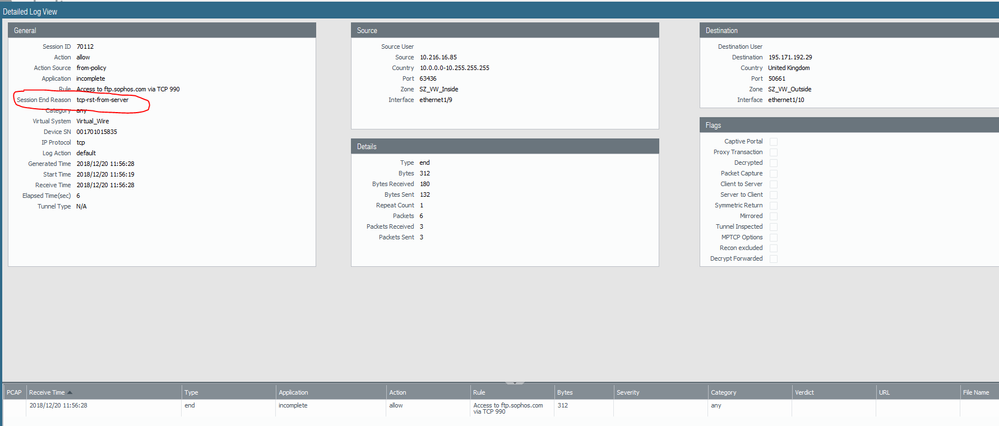
I see that your rule is being hit for the passive connection on port 50661 (your filezilla screenshot shows that the client is trying to connect to 195.171.192.29:50661 (197*156+227)), but your ftp client either says the connection has timed out or that the server denied the connection (were the three error messages at the same time?).
What does your Palo alto say is the reason for the session end reason?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-20-2018 06:40 AM
Hi Rikkert_Kooy,
Yes, i saw the three error messages at the same time on the Filezilla client.
The Session End Reason is 'tcp-rst-from-server'.
What does it mean where it says 'incomplete' under Application please?
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-20-2018 07:40 AM
incomplete means not enough packets have gone through the Palo Alto for it to recognise the application. So it doesn't know yet whether it is SSL (which the rule allows) or something else.
If I read the session end reason it seems like the ftp.sophos.com causes the disconnect, but likely because the client was trying to connect to it for 20 seconds.
Why your FTP client wasn't able to actually connect to the server in passive mode I do not understand.
- 12990 Views
- 18 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Syncing Specific Entra ID Groups to Cloud Identity Engine in GlobalProtect Discussions
- Max number of units (aeX.Y subinterfaces) supported under a single AE interface? in Next-Generation Firewall Discussions
- Cortex XDR – Unable to Assign Read/Write Permissions for Mobile Device (Detected as CD-ROM) in Permanent Exceptions in Cortex XDR Discussions
- Vulnerability Assessment in XSIAM 3.3 in Cortex XSIAM Discussions
- Inquiry Regarding Publishing Custom Third-Party IOC Feed via EDL Hosting Service in Next-Generation Firewall Discussions