- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Forward Proxy Edge Browser problems
- LIVEcommunity
- Discussions
- General Topics
- Re: SSL Forward Proxy Edge Browser problems
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-20-2018 03:12 AM
Hello,
We have a problem at one of our new locations with the Edge Browser when using SSL Forward Proxy (PA-220).
The problem is as following: When we activate the SSL Forward Proxy, the Edge browser takes very long and sometimes even disconnects when trying to open a normal webpage with TLS. Chrome, Mozilla & Internet explorer are OK. Certificates are also trusted and there are no GPO rules for the Edge browser which could cause problems.
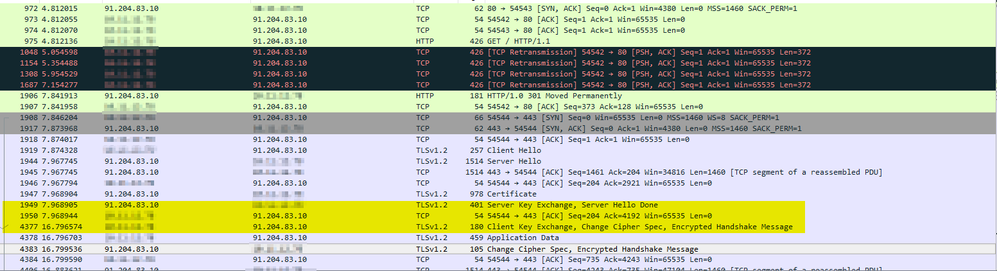
I made a packet capture and noticed following: The server key exchange packet comes in, and then the client takes a long time to respond with the client key exchange (~10seconds). Does anybody have an idea what could cause there a problem? As I wrote, other browsers are OK.
Thanks and regards
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-05-2018 06:41 AM
After some more troubleshooting we (my collegue 🙂 ) found the cause for the problem:
The forward-trust certificate name was a hostname which the Firewall could resolve from external. The FW then tried to verify the CRL, but as the FW resolved it to an external address, the verification could not happen as the CRL verification should happen internally. After creating a new forward trust cert with a random name, the decryption was running smoothly.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-20-2018 06:58 AM
What Decryption Profile options do you have enabled on the Policy?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-21-2018 08:00 AM
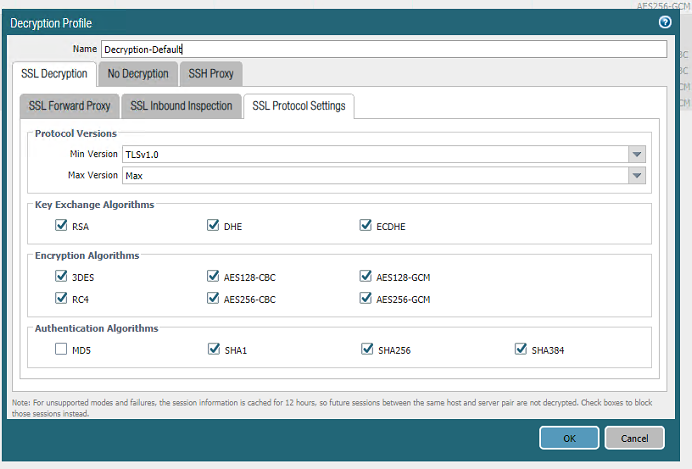
Only default values are enabled:
I tested today again and the internet explorer is also affected. Chrome is OK. Seems like Microsoft Browsers have some problems with it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-05-2018 06:41 AM
After some more troubleshooting we (my collegue 🙂 ) found the cause for the problem:
The forward-trust certificate name was a hostname which the Firewall could resolve from external. The FW then tried to verify the CRL, but as the FW resolved it to an external address, the verification could not happen as the CRL verification should happen internally. After creating a new forward trust cert with a random name, the decryption was running smoothly.
- 1 accepted solution
- 6301 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- web file blocking in Next-Generation Firewall Discussions
- Global Protect being interrupted by Copilot? in GlobalProtect Discussions
- Admin GUI Login Fails on WAN Interface - Slow Load & "Single Sign-On" Error on PA-410 in Panorama Discussions
- How to trigger a "Response page" on Palo Alto NGFWs using URL filtering & Decryption in Next-Generation Firewall Discussions
- Enhanced split tunnel configuration tips in Prisma Access Discussions