- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL forward trust option
- LIVEcommunity
- Discussions
- General Topics
- Re: SSL forward trust option
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2018 04:42 AM
Hi,
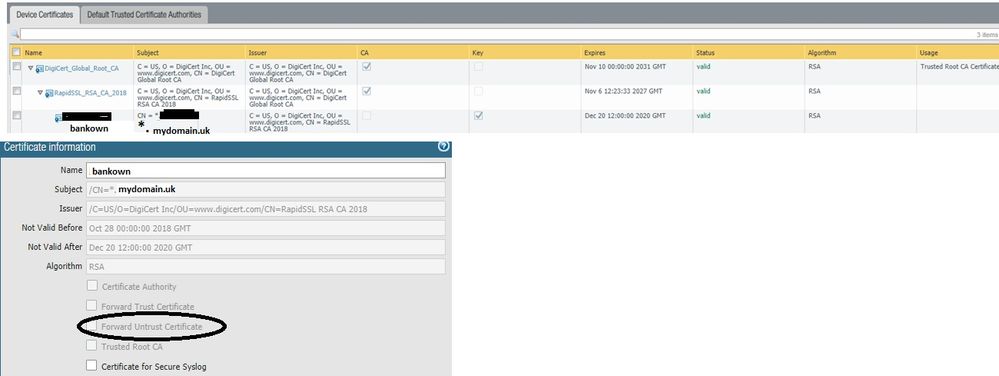
We have a certificate generated by RapidSSL as CA. but we can NOT set this certificate as a forward trust certificate to use in Decyption SSL, the option shows disable. Roots is in the list "default trsuted certificate authorities".
Why the option is disbled???
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2018 09:50 AM
@JW6224 wrote:
To do what you want to do, you can generate a self-signed certificate that is a Certificate Authority, and mark it as your Forward Trust certificate. Or you can generate a CSR (Certificate Signing Request) for a Certificate Authority, and have an internal CA sign that request. Once you import the signed certificate, it will be valid for marking as a Forward Trust certificate.
If you have an Internal CA, it is likely to be trusted by your clients and is the better choice. If you do not have an internal CA, the CA certificate generated by the firewall is probably the faster option, but you still need to make sure it is trusted as a Trusted Root CA certificate by all of your clients.
I hope this helps!
@BigPalo- this was from my earlier post and addresses the two options you have.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2018 04:53 AM
Because it is only a servercertificate and not a CA certificate
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2018 07:24 AM
We want to do this:
- (Recommended Best Practice) Enterprise CA-signed Certificates—An enterprise CA can issue a signing certificate that the firewall can use to sign the certificates for sites which require SSL decryption. When the firewall trusts the CA that signed the certificate of the destination server, the firewall can send a copy of the destination server certificate to the client, signed by the enterprise CA. This is a best practice because usually all network devices already trust the Enterprise CA (it is usually already installed in the devices’ CA Trust storage), so you don’t need to deploy the certificate on the endpoints, so the rollout process is smoother.
SSL-decrypt with a certificate signed by RAPIDSSL. Any procedure for that. We only see the procedure generating CA in Palo Alto.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2018 07:31 AM
Hi @BigPalo
You can either generate a CA cert on your firewall or use a cert sygned/generated by an enterprise CA, but you will not get a CA cert from any of the public trusted certificate authorities.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2018 07:43 AM - edited 10-29-2018 07:44 AM
To do SSL Proxy Decryption, you must have a Forward Trust certificate. To mark a certificate as a Forward Trust certificate, it must have an attribute that marks it as a Certificate Authority. Commercial Certificate Authorities, such as RapidSSL, do not typically sign CA certs for customers - because this will allow a customer to issue certificates under their trust chain, which could be for anything (e.g. you could issue a certificate for live.paloaltonetworks.com that you generate yourself, and anyone that trusts RapidSSL will trust your certificate as valid.) They would rather A.) that you not issue certificates signed by them, and B.) pay money for any certificates that you use that are signed by them. It's kind of their entire business model.
To do what you want to do, you can generate a self-signed certificate that is a Certificate Authority, and mark it as your Forward Trust certificate. Or you can generate a CSR (Certificate Signing Request) for a Certificate Authority, and have an internal CA sign that request. Once you import the signed certificate, it will be valid for marking as a Forward Trust certificate.
If you have an Internal CA, it is likely to be trusted by your clients and is the better choice. If you do not have an internal CA, the CA certificate generated by the firewall is probably the faster option, but you still need to make sure it is trusted as a Trusted Root CA certificate by all of your clients.
I hope this helps!
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2018 07:48 AM
We have this certificate, signed by RapidSSL. But we can not use it for SSL decrypt. I think it has all requisites.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2018 07:52 AM
As mentionned by @JW6224, to use a certigicate as ssl forward trust cert it needs to have the CA flag set ... your cert does not have this flag set (as you can see in the CA column kn your screenshot/cert list)
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2018 07:59 AM
I hear you...I doubt that it's a CA cert, but I believe you have the certificate. I just think it's the wrong type of certificate.
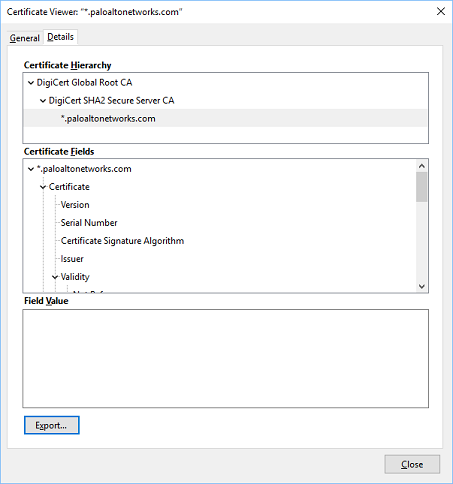
Let's look at it. Here are the certificates for live.paloaltonetworks.com.
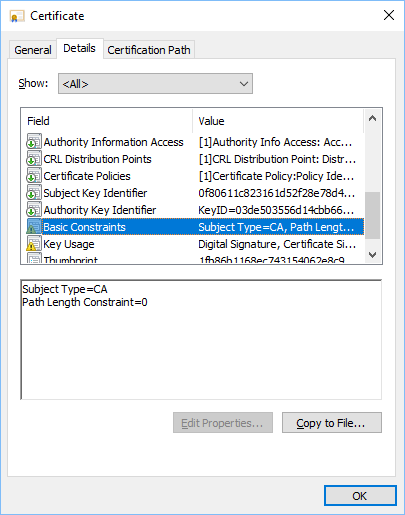
This is Palo Alto's wildcard certificate, signed by DigiCert. So let's look at the CA Certificate, and then inspect the Basic Constraints:
Notice that the Subject Type is listed as a CA. This certificate can be used to sign other certificates as part of their Public Key Infrastructure. Compare that to the actual certificate used by the website:
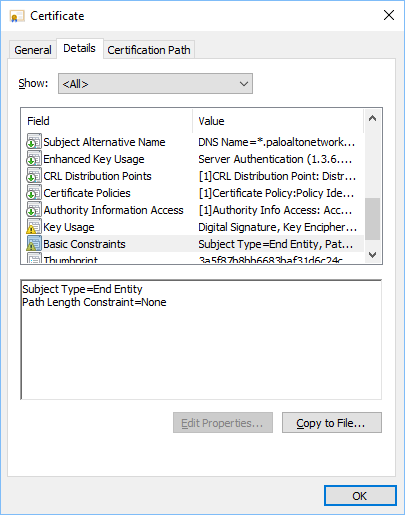
This certificate is for an End Entity. It can't sign other certificates. It is good to identify/authenticate anything that matches the subject name, which is a wildcard for anything on the paloaltonetworks.com domain. But it can't be marked as a Forward Trust certificate.
If you export your public certificate (the one you're trying to use as a Forward Trust) and inspect it, which does it look like? Does it identify as a CA?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2018 09:48 AM
SO how customer can create CA certificate company in order to import in PA?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2018 09:50 AM
@JW6224 wrote:
To do what you want to do, you can generate a self-signed certificate that is a Certificate Authority, and mark it as your Forward Trust certificate. Or you can generate a CSR (Certificate Signing Request) for a Certificate Authority, and have an internal CA sign that request. Once you import the signed certificate, it will be valid for marking as a Forward Trust certificate.
If you have an Internal CA, it is likely to be trusted by your clients and is the better choice. If you do not have an internal CA, the CA certificate generated by the firewall is probably the faster option, but you still need to make sure it is trusted as a Trusted Root CA certificate by all of your clients.
I hope this helps!
@BigPalo- this was from my earlier post and addresses the two options you have.
- 1 accepted solution
- 8655 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Log forwarding from Cloud NGFW in Azure to Log Analytics Workspace for Sentinel in VM-Series in the Public Cloud
- No "certificate used by" field when generating certs for SSL forward trust and untrust? in General Topics
- Azure "az" command and decryption in Next-Generation Firewall Discussions
- Renew of Self Signed SSL Forward Trust Certificate without Root CA in Next-Generation Firewall Discussions
- Forwarding Palo Alto Logs to s3 in Strata Logging Service Discussions