- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL/TLS vs. Chrome [missing_subjectAltName]
- LIVEcommunity
- Discussions
- General Topics
- Re: SSL/TLS vs. Chrome [missing_subjectAltName]
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-26-2017 02:28 PM
I'm trying to get rid of the warning when I open the PA GUI from Chrome. I'm getting the following warning:
- This server could not prove that it is 192.168.10.4; its security certificate is from [missing_subjectAltName]
First of all, IE is fine, no errors!
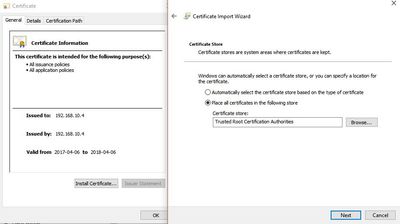
I have generated the certificate and imported it as my trusted Root CA:
I have also created a certificate profile (called it GUI) under "Device -> Certificate Managemenet- > SSL/TLS Service Profile", which used the ceriticate above.
Then I went to "Device -> Setup -> Managemenet -> SSL/TLS Service Profile" and chose "GUI" (the cerifcate profile above).
However, Google Chrome does not like it. Off course if I ignore the warning, it works no problem.
Any ideas what I'm missing, or why google doesn't like me?!
Thanks!
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-26-2017 03:43 PM - edited 07-26-2017 03:44 PM
When you generate your certificate, it needs a Subject Alternative Name field for Chrome to play nicely with it. As far as I know, Chrome is the only browser to officially deprecate the Common Name, but Safari and Opera are both based on WebKit, the guts behind Chrome, so I imagine it will be soon that they follow suit.
Internet Explorer, Edge, and Firefox don't enforce this, so they'll likely be fine for a while.
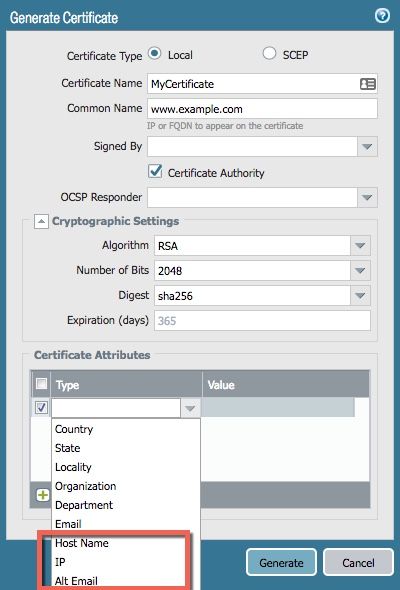
On the firewall, you can generate that by using the two available fields in the certificate generation section:
The Host Name, IP, and Alt Email fields are all Subject Alternative Name fields, and adding any of them is sufficient to avoid that error. I would recommend matching the CN that you created, unless you really do want to access it with a DNS name, in which case just put that DNS name in the "Host Name" field.
If you're generating the cert elsewhere, you will need to figure out how to add the SAN field with that certificate provider.
Best regards,
Greg Wesson
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-26-2017 03:43 PM - edited 07-26-2017 03:44 PM
When you generate your certificate, it needs a Subject Alternative Name field for Chrome to play nicely with it. As far as I know, Chrome is the only browser to officially deprecate the Common Name, but Safari and Opera are both based on WebKit, the guts behind Chrome, so I imagine it will be soon that they follow suit.
Internet Explorer, Edge, and Firefox don't enforce this, so they'll likely be fine for a while.
On the firewall, you can generate that by using the two available fields in the certificate generation section:
The Host Name, IP, and Alt Email fields are all Subject Alternative Name fields, and adding any of them is sufficient to avoid that error. I would recommend matching the CN that you created, unless you really do want to access it with a DNS name, in which case just put that DNS name in the "Host Name" field.
If you're generating the cert elsewhere, you will need to figure out how to add the SAN field with that certificate provider.
Best regards,
Greg Wesson
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-26-2017 06:29 PM
Ha! That was easy! Thanks a lot. I've had this issue for months, but I just kept postponing it.
PS: since I'm using the PA as DNS Proxy, I created a static entry for the name I created (pa.local) and as used that for CN and Hostname. Works like a charm!
- 1 accepted solution
- 6050 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!