- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Subinterfaces and Policy based routing
- LIVEcommunity
- Discussions
- General Topics
- Re: Subinterfaces and Policy based routing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2018 09:20 PM
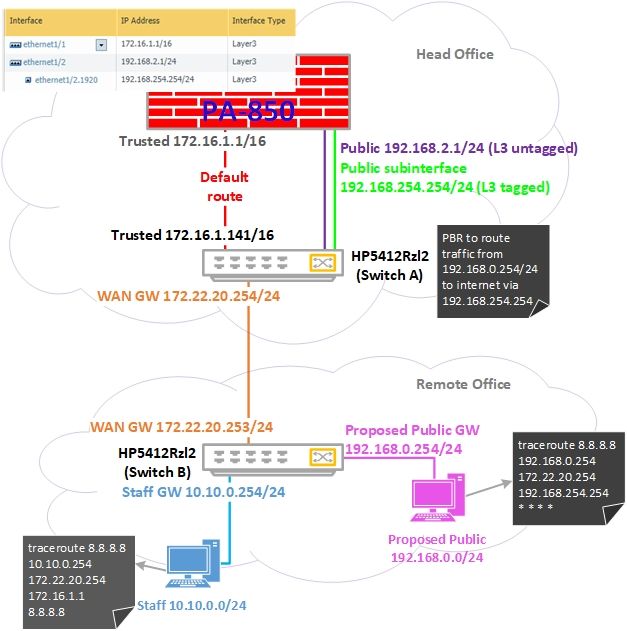
Hi, so I've configured a new L3 subinterface on an existing L3 interface, both with IP addresses and I thought it was going to work. I've got a PBR rule in place on the previous hop, a HP switch, which diverts some traffic to this new subinterface. I can see the selected traffic allowed out from the Palo's traffic monitor logs but, from the client end, routing through the new subinterface I'm not getting responses back. A traceroute from the client to outside (or even the subinterface's primary interface) result in a response from the subinterface but no further.
Out of desperation I added a static route on the Palo to ensure the return packets know how to get back but it's still not working. I've added a snippet of the network for a visual representation. Any ideas what I might have missed?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2018 12:25 AM
Since you enabled PBR on the switch behind the firewall, you may need to add routing or PBF with symmetric return on the firewall (192.168.0.0/24 via 192.168.254.<switch interface>)
The firewall may now want to try and route return packets out of 172.16.1.141 which will cause all kinds of problems
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2018 12:25 AM
Since you enabled PBR on the switch behind the firewall, you may need to add routing or PBF with symmetric return on the firewall (192.168.0.0/24 via 192.168.254.<switch interface>)
The firewall may now want to try and route return packets out of 172.16.1.141 which will cause all kinds of problems
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2018 12:39 AM
Just a couple of questions for clarity for me and hopefully others:
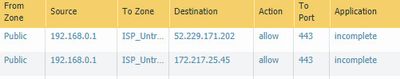
1) Is the outgoing traffic having NAT applied to it? It wasn't clear from the logs or config you provided whether the new subnet is being hidden correctly behind your external address.
2) Have you performed a packet capture to confirm that the traffic is being received back to the firewall and then what interfaces its leaving on the firewall (looking at the source mac of the return packet on the transmit pcap)?
3) Have you checked the counters on the firewall (apply packet capture filters then run 'show counter global filter severity drop packet-filter yes delta yes' whilst generating traffic to make sure none of it is being dropped silently.
4) If the above fails, have you looked at performing a flow debug basic to confirm if the return traffic is leaving the correct interface and doesn't show an drops?
Just a couple of ideas for next steps for you. Please leave an update with what you find
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-04-2018 08:05 PM - edited 03-04-2018 08:17 PM
Hi JamesWW,
Thanks for taking the time to respond. Sorry it's taken a while to get back to you, I'm only part time here.
As per the post by reaper, I ended up adding a PBF rule to the Palo to route traffic destined for the public subnet through to the public interface and that's worked. Thanks again for the time you took to help.
Cheers,
Michelle
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-04-2018 08:14 PM
Hi reaper, I had suspected that this might be the case but wasn't really sure if it would be necessary. Anyways, I tried it and it works you little ripper!
- 1 accepted solution
- 6612 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Issue after onboard Azure VM into SCM in Strata Cloud Manager
- Asymmetric Routing - Palo Edge Firewall Active/Passive to Nexus Core in General Topics
- Unable to Ping Palo Alto Interface – Connectivity Appears One-Sided in Next-Generation Firewall Discussions
- Zscaler IPSec tunnel over Palo alto SD WAN in Advanced SD-WAN for NGFW Discussions
- Admin GUI Login Fails on WAN Interface - Slow Load & "Single Sign-On" Error on PA-410 in Panorama Discussions