- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
U-Turn NAT with Port Address Translation in a DMZ
- LIVEcommunity
- Discussions
- General Topics
- Re: U-Turn NAT with Port Address Translation in a DMZ
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
U-Turn NAT with Port Address Translation in a DMZ
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-06-2016 07:10 PM
Hi Community,
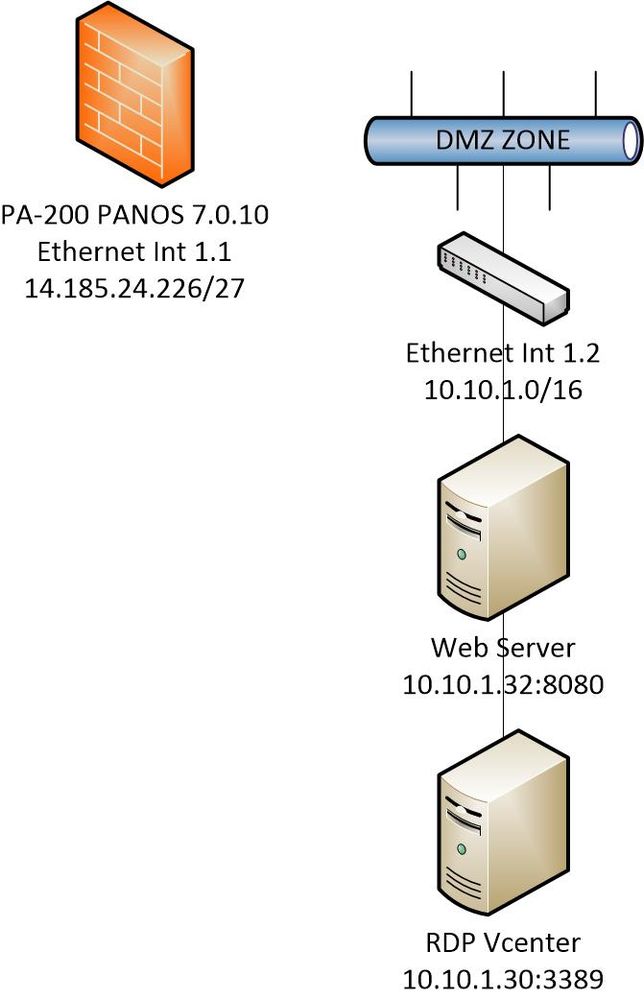
I am configuring my first PA-200 and having a difficult time. I have a /27 external network and have the PA-200 seeing the internet properly. I have internet untrust zone setup as l3 on Int 1.1, and a DMZ setup as l3. The DMZ zone is on eth 1.2 interface and has a few servers plugged into an unmanaged gigabit belkin switch as depicted below. At this time, I am not planning to use the firewall with Trusted users or any of the other intefaces, just to serve up publically facing servers in the DMZ with specific ports. I have found several articles/config example suggesting that I use U-Turn Nat to make this happen properly but none that consider PAT as well along with layer2 traffic from the unmanaged switch. I was hoping someone could please provide some help. Thank you very much.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-07-2016 02:10 AM
Hi @vazquezr1
you don't need u-turn nat to make this work (u-turn is used to reach internal servers, from the inside, on their external IP, you need regular inbound nat, with destination ports
as it happens, i wrote a little something about that : Getting Started: Network Address Translation
scroll down to 'Uni-directional policy', this should be the bit you need
hope this helps
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-07-2016 08:06 AM
Hi Reaper,
Appreciate the help and article. I had actually started with your suggested config originally since that is what I remember from the (3) day training. I still couldnt see the servers from the outside. I remember somewhere that someone had said you had to "tag" layer 2 traffic of it was not routed from a managed switch? Since all these servers are sitting on a dumb hub basically perhaps that is the problem? I am just using the "default" virtual router but perhaps that is not sufficient. Thank you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-07-2016 08:22 AM
are your interfaces _sub_ interfaces ? i'm assuming they're normal L3 interfaces, in which case you don't need tags
tags only come into play if you've got a managed switch connected to the firewall via a trunk interface (this causes the firewall to receive packets with the .1q header present, so you need to have tagged subinterfaces to diffeentiate between the vlan tags)
did you make sure to set the nat rule
from untrust to untrust, orig destination <external IP> destination translation <internal IP>
and then a security policy
from untrust to trust, destination <external IP> apps, ports, allow
are you seeing the sessions in your traffic log ? (if not, the external router may not be aware you're there and you may need to check arp settings on the router for example)
if you are, is the NAT represented as expected ?
you did set a default gateway on your servers pointing to your firewall's DMZ IP, and a 0.0.0.0/0 route in the firewall VirtualRouter, pointing to the external router, right ?
i got a whole bunch of articles that may be of interest 😉 Getting Started: The Series
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-07-2016 08:27 AM
Thanks Reaper! I originally had a VLAN and assigned it to the DMZ interface and it didnt work. I think I do have the servers and virtual router properly setup. Let me check these docs you sent over, delete the current config, and give it another go. Fingers crossed! Will advise shortly.
- 3684 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- NAT Translations Related to VPN Tunnels in Next-Generation Firewall Discussions
- Bi-direction Nat logic in Next-Generation Firewall Discussions
- Question regarding source NAT in S2S VPN in Next-Generation Firewall Discussions
- TYPICAL NAT QUESTIONS in General Topics
- Clarification Needed on Multiple Static NAT Rules with the Same Public IP Address in General Topics