- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
URL Filtering log with action allow
- LIVEcommunity
- Discussions
- General Topics
- URL Filtering log with action allow
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
URL Filtering log with action allow
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2023 02:14 AM
Hi Folks,
It seems my whole life is a lie... Apparently PAN FW will generate URL log for category with action set to allow.
Yep, and the funnier thing is that you don't even need URL filtering profile applied on the rule. Someone may say I am crazy or I don't understand how PAN FWs work, probably both is true...But how would you explain the following:
Quick background we have IPsec VPN between two PAN fw and we manage both. We have decided to create "trust-all" rule on one end the tunnel and have specific rule only on one of the FWs. For that reason on the far end of the tunnel the rule is "allow any, without any security profile". Today something got my attention - you guess it - the rule without security profile was generating URL allow logs
Here is how the logs from both firewall looks like
And here is the rule without any security profile, that is generating URL log with action allow
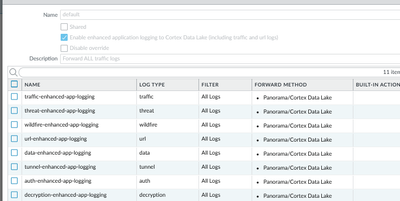
It seems the cause of this phenomena is the Log Forwarding profile.
I was not able to find any other reference to this behavior, but I hope someone prove me wrong and provide any other documentation mentioning this behavior of Log Forwarding.
Please tell me I am not the only one who was not aware of this, I am flipping tables around here...
I am now more curious how this works, if no URL filtering profile is applied why FW is inspecting the SNI. For me this sounds like FW is still performing some kind of inspection (event without any security profile, nor decryption rule also), but will do it silently without generating any log. Until you apply log forwarding for all logs...
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-25-2023 12:58 AM
Is that rule positioned at the very top of your rulebase? if not, can you try putting it there to see if it still logs URLs?
do you have decryption set up (even no-decrypt) that could be matched?
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-27-2023 05:45 AM
Hey @reaper ,
- The firewall that is generating the URL allow rule, doesn't have any decryption rule at the moment.
- Matching rule is actually around the bottom, but moving it higher, shouldn't make difference, because the matching source and destination objects are matching only that rule.
Hey @kat3xx ,
Indeed the log forwarding is set to forward any log
But this still doesn't explain why rule with no security profile will generate URL log?
- 3719 Views
- 3 replies
- 4 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex Management Report in Cortex XDR Discussions
- About threatID action. in General Topics
- PAC Retention and URL Category Priority Behavior in Prisma Access in Strata Cloud Manager
- looking to block google ai mode in Advanced URL Filtering Discussions
- XSIAM Dynamic filtering in exclusions in Cortex XSIAM Discussions