- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
User-ID Connection Security Won't Work
- LIVEcommunity
- Discussions
- General Topics
- Re: User-ID Connection Security Won't Work
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
User-ID Connection Security Won't Work
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2020 06:44 AM
UserID Agent version 9.0.5-8
Firewall 9.0.8
Windows Server 2016 UserID Agent Servers x2
I've tried following this guide and numerous others (https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClGFCA0)
Keep getting 'Failed to validate client certificate, thread : 1 , 5-10054!' as shown at the very bottom of the aforementioned support article and seeing SSL failures in the system log of the firewall.
I've tried generating the cert about a hundred different ways and formats on the server/firewall, and I still get the issue. I've tried using IP, FQDN, Subject-Alternative-Name including IP, Hostname, FQDN, one all or any. Port 5007 is open and the server worked previously. Now my certificate is stuck in the User-ID software and I cant delete it or use the server any longer with the firewall for regular user ID which is annoying. There is no delete/remove button to take the cert back out of the software so I pretty much have to get this working now as I'm down to 1 User-ID box.
At this point I'm missing something fundamental, like a check box on the firewall or some hidden thing. I've installed certificates for Decrypt in and out, Management address, and all sorts of certificates and never had any problems until this. Has anyone successfully set this up and they can walk me through how you did it and maybe I can see my error? I have heard that IP address must be used in the SAN attribute, but that didn't work either.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2020 09:40 AM
Hello TylerHay,
There are really no tricks...
Here's a working config I just did in my lab. It might give you an idea of what went wrong with your setup.
On the PA Firewall:
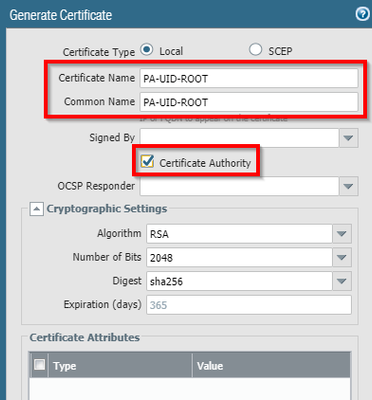
- Create a CA root:
No need to enter any other information as this is to create a self signed cert later
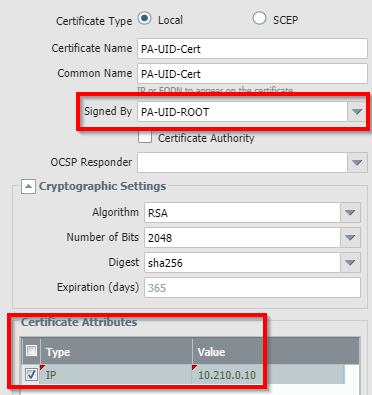
- Now, create the self signed certificate. Make sure you signed it with the CA we just created. Enter at least the valid IP in the attributes to make this certificate valid:
- You will end up with something similar:
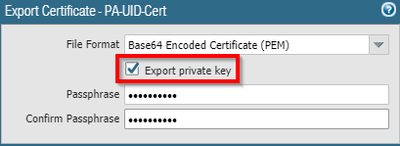
- Now, select the self-signed certificate (PA-UID-Cert in this case) and export it with the private key:
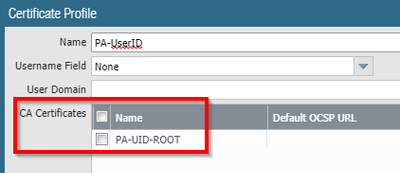
- Now, create a certificate profile with no other information than the CA root that has been created:
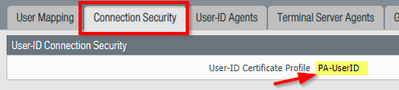
- Assign this Certificate profile too the "Connection Security" tab:
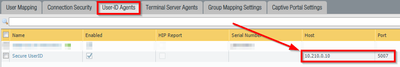
- You can now add the user ID agent configuration:
- Commit the changes.
On the UserID server:
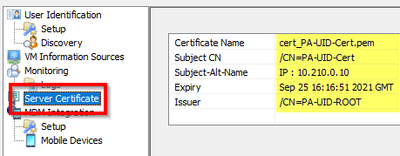
- Add the certificate :
- Save and commit the changes...
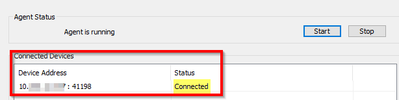
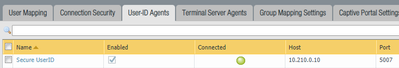
- Go to "User Identification". After a few seconds, it should change the status to connected:
- On the PA side, it says the same:
Hope that helps!
R.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2020 01:08 PM
Hello,
If this is mission critical I would say call TAC and get their assistance. While I have never set this up myself, I have setup other things and usually missed something simple, not saying you haven't gone over this a bunch of times.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2020 01:56 PM
Hi TylerHay,
I posted a full how-to earlier but it has never been published... There might be a delay or a bug somewhere in the forum...
Anyways, it should not be a issue.
Make sure the certificate you import in the client is fully recognized by the PA firewall (including the root CA that signed this certificate - the attached certificate profile should be linked to this root CA...). Regarding the SAN, I just added the IP address in the certificate. Worked well 1st time.
Hope that helps... and maybe the full description I did this morning will be posted eventually.
Regards.
X
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2020 09:58 PM
@Retired Member,
The example that @Rievax wrote up is great and definitely works perfectly fine. The one thing that I would say is that if you have this certificate signed by an external CA, be sure that you actually have the full cert chain in the certificate profile. You may have to manually chain the certificates if it's signed by an intermediary to get things to work properly.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-16-2021 10:01 PM
Hi Tylerhay To remove cert,
i had same issue and edited the UserIDAgentConfig.xml file in User-ID Agent directory, Remove the information between the server certificate tags in the XML file directly and restart the service. This removed the certificate form the user-id application and allowed my firewalls to connect.
Hope this helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-09-2024 01:40 PM
https://thedxt.ca/2024/10/palo-alto-user-id-and-terminal-server-agent-certificates/
On November 18th, 2024, the certificates that the Palo Alto User-ID agent and the Palo Alto Terminal Server agent use to communicate with a Palo Alto firewall will expire, causing all communication to fail.
Palo Alto Networks has made new versions of the User-ID and TS agents with updated certificates that will expire on January 1st, 2032.
You may just need to update your User-ID Agent
- 31977 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- [SOLVED] - NGFW The Connection To Global Protect On The IPads Times Out!! in GlobalProtect Discussions
- Questions Regarding Output Difference in "show ctd-agent status security-client" Command in General Topics
- About the output of the "show ctd-agent status security-client" command in Next-Generation Firewall Discussions
- ION Security Stack in Advanced SD-WAN for NGFW Discussions
- UserID periodic empty groups issue in General Topics