- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
User-ID two usernames being identified by User-ID servers
- LIVEcommunity
- Discussions
- General Topics
- User-ID two usernames being identified by User-ID servers
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
User-ID two usernames being identified by User-ID servers
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2020 09:32 PM
Hi,
I am having troubles with getting the Palo's in my network to only use the UPN of a user in our environment. I would like to start creating security policies to control staff members access to resources based on their AD user rather than IP address and then further to that leverage groups. Long term of course the idea is to leverage AD groups to control access to resources, however I need to prove that this will work on individual users first.
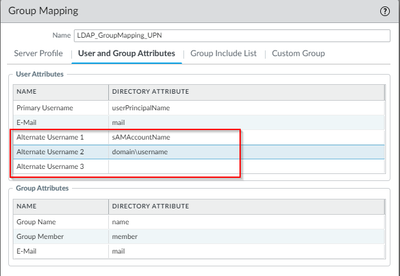
It is not working currently because what I am seeing in the monitor logs is either domain\user.name or user.name@domain.local and because of this whenever I make a security policy sometimes it works for the end user and then the next moment it doesn't work. It will work 100% of the time if I update the policy to domain\user.name and user.name@domain.local . This of course is not practical and scalable.
Currently we are using 2 Palo Alto Windows Server Agents to get the access data from our AD servers. Palo Alto monitor logs are reporting back connected and the User-ID log shows the source as being either of these servers.
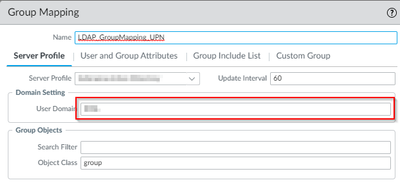
Here is some screenshots of our current configuration for the user & group mapping.
Are there additional settings, or things I need to be doing to resolve this and either only match on domain\user.name or user.name@domain.local
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-01-2022 07:12 AM
I bumped into this discussion and I believe I have an additional challange 😀
In our case the UPN and samAccountName are not the same. The samAccountName is the employee number. In the example below this is user1234
The user recognition works flawless on for example VPN connections and when I look at the group mappings it only shows UPN names.
Also when creating policies I can choose the user principal name.
The user data is fetched via Active Directory-WinRM
Looking at the "User-ID" logs it shows that the client (computer) provides the username.
In this case it is domain\sAMAccountName
I would guess that a user has logged onto with his employee number.
This is also shown in the Traffic Logs.
But there does not appear to be a match between short-domain\sAMAcountName and the UPN.
There is a match on FQDN-DomainName\sAMAccountName
Most likely I need to find the solution to this problem in the alternate UserName fields.
Any idea what needs to be set to find the correct match.
Example username
acme.com\user1234
acme.com\john.doe
needed:
ac\user1234
where ac is the short domain name instead of the FQDN
Any thoughts are most welcome.
- 20056 Views
- 17 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Concerns of Firewall 5250 dropping packets and enabled DSRI (Disable Server Respponse Inspection) relieve issues for a few hours but came back in Next-Generation Firewall Discussions
- Slow Download and Uploads From Various Cloud Providers in Next-Generation Firewall Discussions
- Prove the firewall innocent? in General Topics
- How to create Custom Application Signature to identify WebRTC Application with Cisco Meeting Server in Next-Generation Firewall Discussions
- Google meet/ hangout Stun servers aged-out in General Topics