- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Using App-ID to block
- LIVEcommunity
- Discussions
- General Topics
- Using App-ID to block
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Using App-ID to block
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-18-2020 12:46 PM
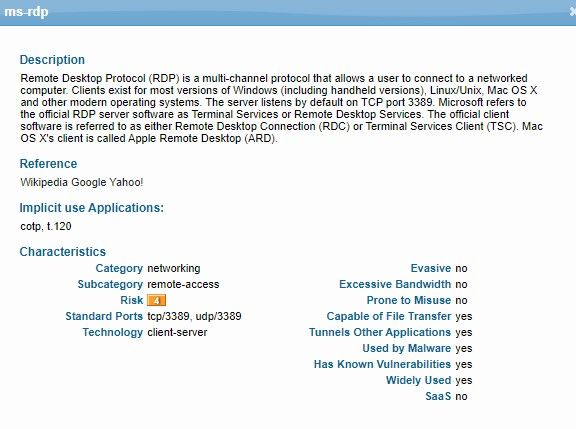
I have a question about using App-ID. Can you block an application just by using APP-ID. I have a situation where my firewall is in a default allow environment. I know this isn't a best practice but it is a complex environment and there are a lot of politics so it is what it is. Anyway, I tried to block a service based on App-ID and it is not working as I had hoped. The request was to block RDP regardless of port. In theory App-ID should be able to do this right, if it is identifying the applications regardless of port, it should be able to block them. However what I get is it seems to block them on port 3389 (default RDP port) but everything else it just marks as incomplete or insufficient data either way blocking it. So it kind of creates the default block which won't work in the situation. If I add application default then it only looks at 3389 and blocks that. But if someone is using a non standard port for RDP then they go on business as usual and the FW won't block that. All the documentation I can find about this doesn't spell out that App-ID only works in a positive enforcement model with a default deny. I would love to find something that says that so I can block 3389 and move on with life and possibly push towards positive enforcement, but that's another story.
Thanks for any help in advance!
Joe
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-18-2020 02:55 PM
Hello,
Yes, the PAN can do this. However there are a few things you have to remember.
1. the applications the PAN knows have a list of default ports
- https://applipedia.paloaltonetworks.com/
So in your case the firewall is working as expected only blocking the RDP application on port 3389.
Since you want top block it on all ports, you'll need to change the 'Service' to ANY. What the 'Service' is the 'Port'. If you list only the application, it will use what the PAN has builtin. Selecting ANY will block ms-rdp on all ports.
Hope that helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-19-2020 02:03 PM
Thank you for the response. Maybe I wasn't clear which part I was having trouble with. The problem was when I had the service on any port it was seeing everything as RDP (not port but service.) The problem was I didn't have any rules looking at App-ID above this rule so it was the first rule to try to use App-ID and the last rule before the allow all. So what I did was put some rules above it to start the App-ID, ping as a service on any port and ping as a service with application default in allow and that seems to work to identify a lot of the traffic. I think I need to do some fine tuning but this is what I was looking for.
Thanks
Joe
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-19-2020 02:13 PM - edited 05-19-2020 02:13 PM
Hello,
In your current RDP policy, does it have ms-rdp and any as the service? Maybe a snippet of the policy you are working with.
Please advise,
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-09-2020 11:55 PM
Hello,
When using APP-ID default port is recomended also you can set service port to force allowed application to use specific port.
My suggestion Create a application based rule with identical action before your old rule and monitor them what is hitting.
After your rule table is clean you can create and enfor application filter and groups to block unwanted application which your company requires.
- 8528 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Geo blocking after GP login in GlobalProtect Discussions
- Custom BIOC Rule won't apply to Prevention Profile in General Topics
- Create a IOC without incident in Cortex XDR Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Detect and Block Openclaw with XDR!? in Cortex XDR Discussions