- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
WinRM-HTTP Connection Refused
- LIVEcommunity
- Discussions
- General Topics
- WinRM-HTTP Connection Refused
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-02-2021 02:13 AM - edited 11-02-2021 02:14 AM
Hello,
I'm using agentless user-id with a Windows Server 2012 AD through WMI, we recently updated the server, and it started throwing Authentication Error 10036 flooding our Windows logs. We've searched and troubleshooted the problem for a long time and nothing worked, the only workaround that we think might work is to change the authentication protocol from WMI to WinRM-HTTP. (We cannot roll back the update for vulnerability requirements)
We used this guide https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/user-id/map-ip-addresses-to-users/configur... to set up the configuration, and once we committed we're getting "Connection Refused(0)". The user-id logs are not specifying the error, just a "connection failed, error=0"
Likewise, we also troubleshooted everything, from the configs to the service account having the correct permissions as per Palo Alto's recommendation, and still.
Any ideas?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2022 03:30 AM
Hello,
We weren't able to solve the issue using WinRM HTTP, we did however migrate from PAN-OS Integrated User-ID agent to Windows User-ID Agent which solved the Authentication Error 10036 isuue.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-02-2021 11:39 AM
I also changed from wmi to winrm and seems ok... have you tested your kerberos profile?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-03-2021 02:00 AM
Yes, and it was successful.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2022 02:46 AM
Hello,
happy new year !
We have exactly the same issue...
Everything is configured by following Palo's instructions, but always "Connection refused (0)"
Any ideas?
@echahine have you solved on your side ?
Thank's
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2022 03:30 AM
Hello,
We weren't able to solve the issue using WinRM HTTP, we did however migrate from PAN-OS Integrated User-ID agent to Windows User-ID Agent which solved the Authentication Error 10036 isuue.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2022 07:39 AM
Hi,
Thank you very much for the information, now it works with Windows User-ID Agent !
Why do Palo make PAN-OS Integrated User-ID agent available if it doesn't work ...
Have a nice day
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2022 08:03 AM
It's actually a Windows hardening issue. But you're right Palo Alto should be compatible with these hardenings already since it's an old recurring issue.
Glad to help!
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-22-2022 03:53 AM
Hello,
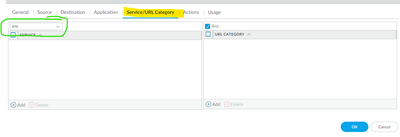
You'll need a policy rule from the management IP to the domain servers, remember that it does not use the default port, so you must define "any" in "service/url category".
bye,
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-21-2023 01:28 PM
Several of you have already gone through the winRM fixes under HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WinRM\Client & HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WinRM\Server fixes, the below settings in windows worked for me ( Panos 10.1.0 with win2k12 R2)
https://serverfault.com/questions/841689/changing-winrm-settings-from-script
- Edit Group Policy.
-
Administrative Templates -> Windows Component -> Winodws Remote Management(WinRM) -> WinRM Client -> make all as not configured enter image description here
-
Administrative Templates -> Windows Component -> Winodws Remote Management(WinRM) -> WinRM Service-> make Allow Basic authentication as not configured enter image description here
-Open powershell and run # gpupdate /force
Attaching my environment settings screenshots.
This will work the magic!
- 1 accepted solution
- 29425 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Backup Peer HA1 IP Address ? in Next-Generation Firewall Discussions
- Prisma Access Service Connection to Palo Alto FW in HA-AA in Prisma Access Discussions
- Cortex - many aged-out connections on 35.244.133.254 in General Topics
- Tuning Panorama HA Timers to Stop False HA1 Alerts over MPLS in Panorama Discussions
- Assistance with LDAP Authentication in General Topics