- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Global protect authentication
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Global protect authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Global protect authentication
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-31-2022 03:38 AM
Hi team,
In Global protect, is it mandatory for the user to authenticate in the portal and also in the gateway? I have tried to remove the authenticator in at least one of them so that it does not ask 2 times for user and pass without success.
Any idea? why do I need both? what happens if I use different authentication profiles? Is it possible to avoid at least one of them? What is the difference between the portal and the gateway?
Thanks so much
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-31-2022 05:26 PM - edited 03-31-2022 05:30 PM
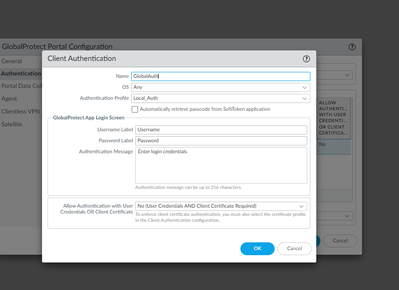
Yes, both the Portal and the Gateway require authentication (otherwise someone could connect without credentials). The Portal provides the GP configuration to the client (or a download of the client via HTTPS), the client then connects to the Gateway to actually setup the VPN tunnel and pass traffic. In most cases you will have the Portal and Gateway on the same interface, but in large setups they can be completely separate. Perhaps an east coast and west coast Portal, with Gateways spread all over the world (the config gives you some options to force a particular Gateway or allow the client to connect to different Gateways in a set based on what is the "best" connection seen from the client).
For authentication against both the Portal and Gateway you have 3 choices:
1) User/pass authentication via a variety of methods (SSO, Radius/LDAP, etc.).
2) User or machine certificate.
3) An authentication cookie.
How you choose which method gets pretty deep into the weeds based on a whole slew of different configuration options in the Portal/Gateway/client. But if you are doing a simple on-demand VPN setup the you will probably want to setup user/pass on the Portal and cookie authentication on the Gateway. A simplified view of the steps is:
- Create an Authentication Profile that will validate your VPN users (against LDAP/Radius/etc.).
- Create a root certificate on the PA for signing (if you already have one for decryption/etc. you can use that)
- Create a Portal on an interface and apply the user Authentication profile.
- Under the Portal -> Agent settings select "Generate cookie for authentication" and select the root certificate.
- Create a Gateway on an interface and apply the user Authentication profile.
- Under the Gateway -> Agent -> Client Settings create a client profile and under Authentication Override select "Accept cookie for authentication override" with the root certificate. You may want to limit the lifetime the cookie is valid.
After finishing the config with all the other options, your client should now be able to connect, prompt for user/pass against the Portal, download the config, and reconnect to the Gateway. The Portal should generate an authentication cookie for the GP client which will use it to automatically login to the Gateway. If the client disappears for away for a while and then tries to reconnect to the Gateway later, the cookie will no longer be valid and the client will be prompted from the Gateway for the user/pass again.
- 2029 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Can you configure clientless VPN in SCM ? in GlobalProtect Discussions
- global protect connection failed authentication failed !!! in GlobalProtect Discussions
- PAC Retention and URL Category Priority Behavior in Prisma Access in Strata Cloud Manager
- AWS vpc Global Protect terraform deployment in VM-Series in the Public Cloud
- Global Protect Portal / Clientless VPN does not recognize SAML username after update to 10.1.14-h20 in GlobalProtect Discussions