- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Slack hooks server certificate invalid
- LIVEcommunity
- Tools
- HTTP Log Forwarding
- Log Forwarding Discussions
- Re: Slack hooks server certificate invalid
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Slack hooks server certificate invalid
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-15-2023 06:44 AM
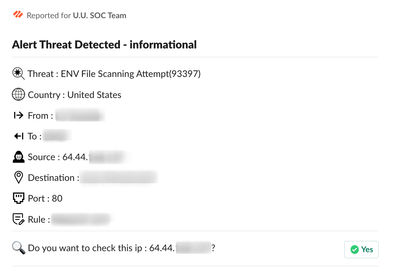
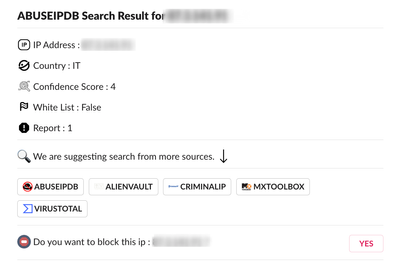
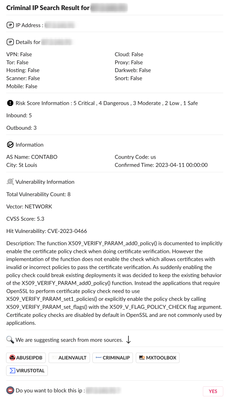
Our firewalls cannot send to hooks.slack.com since they refreshed their cert yesterday (3/14/2023).
I suspect a problem with the way their chain is signing X1 root CA but until they fix it, is there a way to allow the log forwarding service to ignore the invalid cert and send anyway? I see a kb article about doing this for decryption profiles, but not sure if it applies here.
Also is there any debugging that can be done on the palo to get more specific detail about what its problem is with the cert?
Thanks in advance for anyone who can advise.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-20-2023 10:35 AM
The feature request they're referring to from the closed case is not related to this problem. It's about avoiding the infinite loop of system logs trying to send to a dead log server, which fails & raises a system log which it tries to send to the log server, which fails & raises a system log..... etc forever.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-20-2023 10:39 AM
Ah, yes, now I'm the one confused. Either way, I also referenced your current active case and suggested that properly validating certificates should be a priority. We'll see how they respond.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 11:31 AM
Good news, TAC responded to me and called this an "outbreak globally for the slack integration users". They are looking into the cause. My guess is this will be fixed in a future update, but they'll let me know.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 11:33 AM
Well acknowledging the noise we're making is a good first step. They need to band-aid it right away, though.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2023 02:45 PM
Joining with same issue, Pan-OS v10.1.3
TAC working on a workaround, no proper ETA yet
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2023 07:33 AM
Welcome to the party @VladimirL please share any progress you're able to make on your case.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2023 06:55 AM
Hi @onercan - no, not at this time. I've been advised by Palo Support that PanOS 10.2 does not have the issue, but can't verify that as we're on actively-supported v9.1.15.
I saw 9.1.16 dropped this week --the release notes mention expired root cert handing for ssl decryption but not specifically with HTTPS log forwarding process..
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2023 08:23 AM
@rlarosedo you think PanOS support team tested it on v10.2? We will upgrade from v10.0 to 10.2 if it works on v10.2.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2023 10:54 AM
The *impression* I got was that someone over there had tested in on 10.2 and decided it didn't have the same problem. But I can't swear to that. The fact that it's a problem at all suggests they have not been thorough with their testing/validating.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2023 02:13 PM
Hello everyone,
We upgraded from 10.0.8 to v10.2.4. It's working fine. Our SOC is active. we are leaving to party 😂
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-19-2023 08:01 AM
@onercan congratulations, that's good news.
I was away last week but did receive a reasonable RCA from Palo, as well as a workaround to restore successful connectivity in PanOS versions prior to 10.2. Early test of their workaround was successful and I'll be deploying today.
Did y'all also get the email I got from Slack saying that by May 9th all clients will need to have a working X1 Root certificate? That to me suggests they are going to switch from LE long-chain to LE short-chain after all, which will presumably render this problem moot. I have not received direct contact from my Slack account or support folks about this, though, so only speculating what the broadcast email means.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-04-2023 08:58 AM
Following this - Running 10.1.9-h1 and still having this issue. Has anyone received a workaround or ETA on fix?
- 21521 Views
- 30 replies
- 3 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!