- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to create Custom Application Signature to identify WebRTC Application with Cisco Meeting Server
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- How to create Custom Application Signature to identify WebRTC Application with Cisco Meeting Server
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
How to create Custom Application Signature to identify WebRTC Application with Cisco Meeting Server
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-22-2024 02:31 AM
A Custom App-ID allows you to do two things:
- Create pattern-based signatures for traffic that doesn't match any of the pre-defined application signatures.
- Create a Custom Application for use in an Application Override Policy to override a pre-defined application signature.
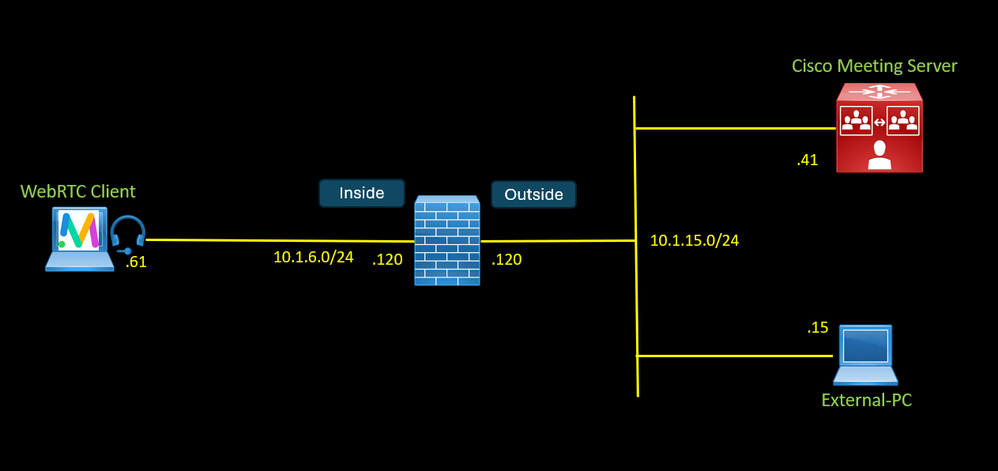
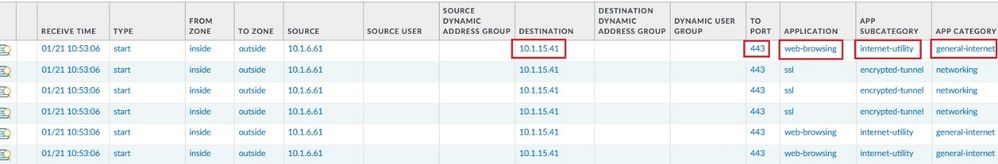
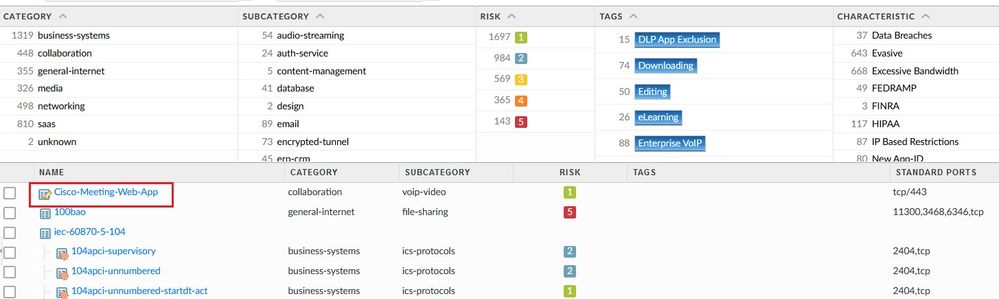
The Traffic Logs shown that a WebRTC connection using Cisco Meeting Web App is identified as a Web-Browser application.
Use wireshark to find a specific pattern to identify your application, in this case we want to identify any connection to the Cisco Meeting Server with WebBridge service enabled using Cisco Meeting App, the Cisco Meeting App uses the Web Browser and WebRTC to access any meeting hosted on Cisco Meeting Server.
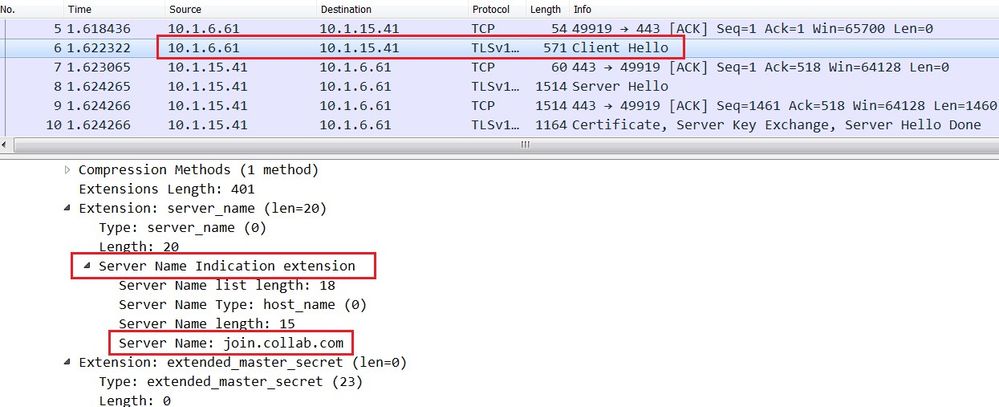
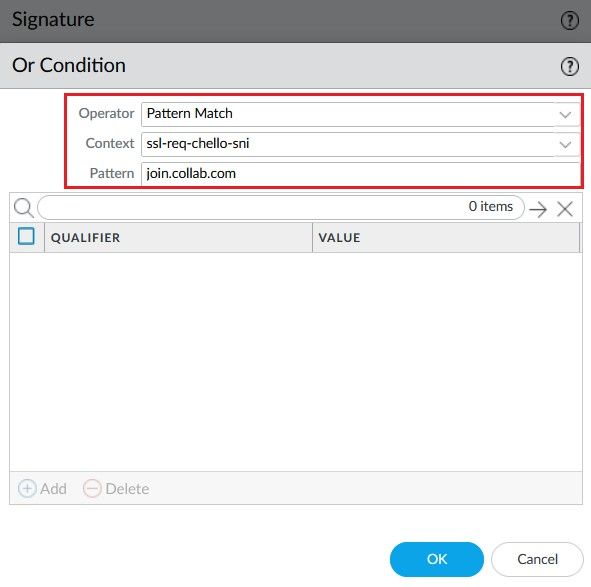
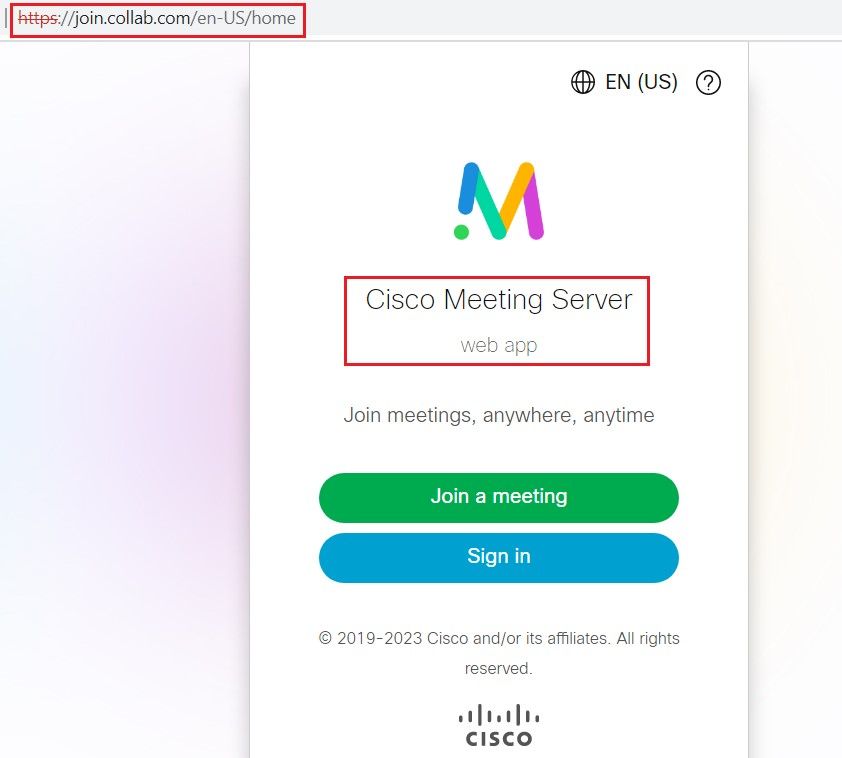
In the Wireshark you can use plenty of SSL informations to identify the application. In this scenario we will use the SNI Server Name Indication sent in the SSL Client Hello which join.collab.com.
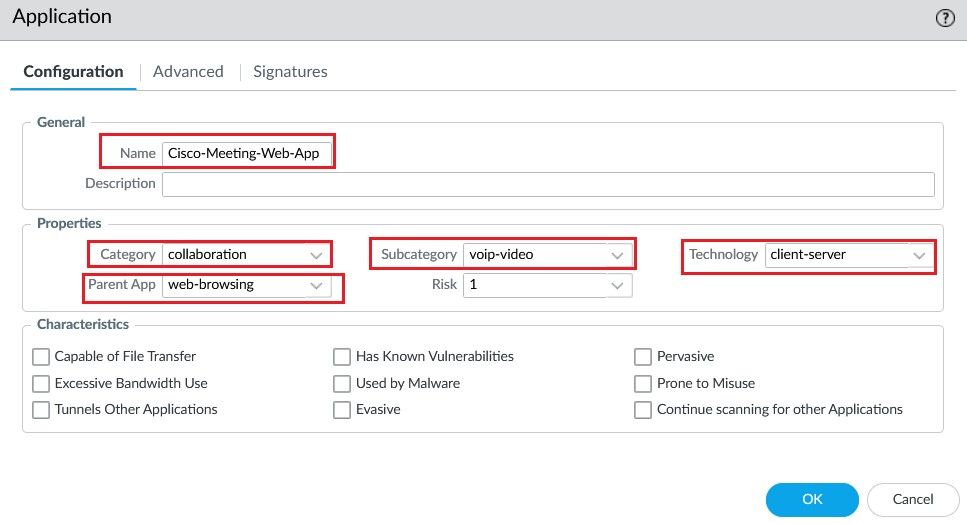
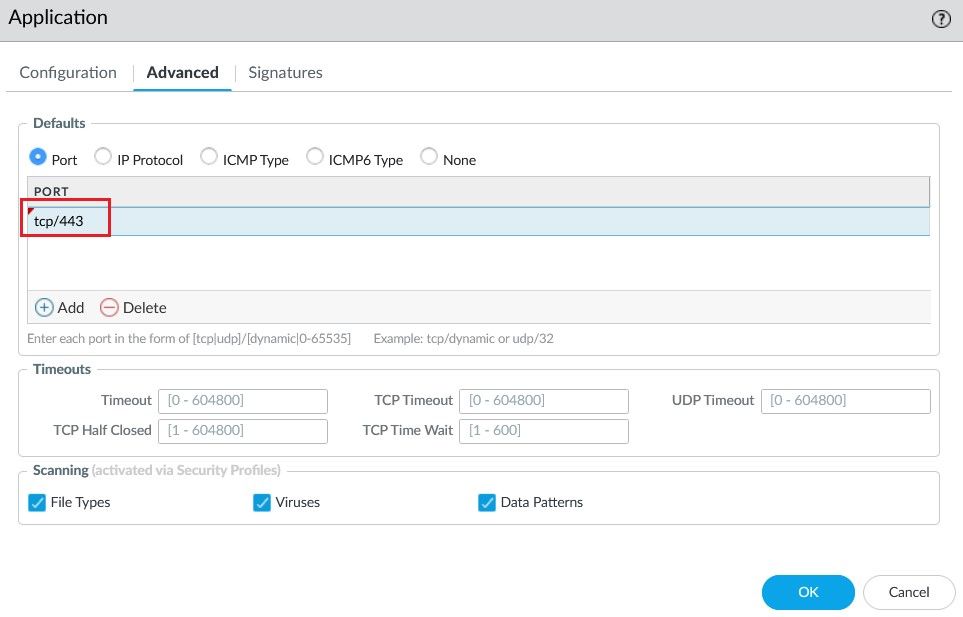
Create a Custom Application with the following settings such as Category, Subcategory, Technology and Parrent App.
Use the Layer 4 port number 443 for application port-based indentification.
Then in the Signature section, define a condition match based on Pattern Match, in the Context field, select the ssl-req-chello-sni, this context tells the firewall to look in the Server Name Indication inside the SSL Client Hello initiated by the client. In the Pattern field, type the pattern or the Guest URL used by the user to access meetings hosted on Cisco Meeting Server.
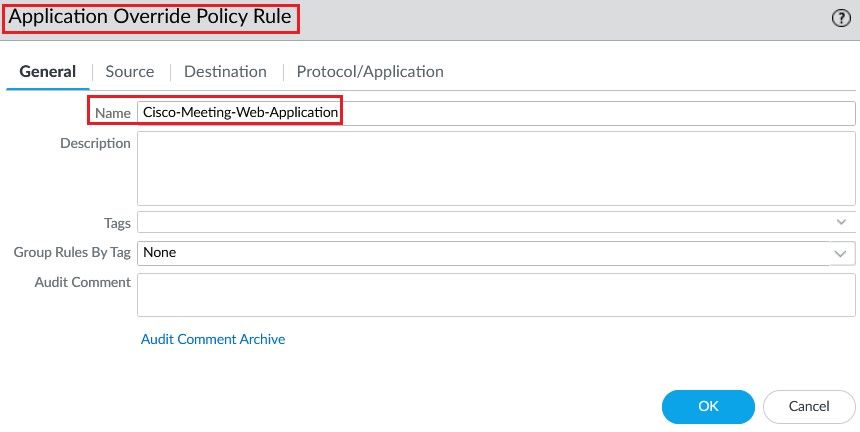
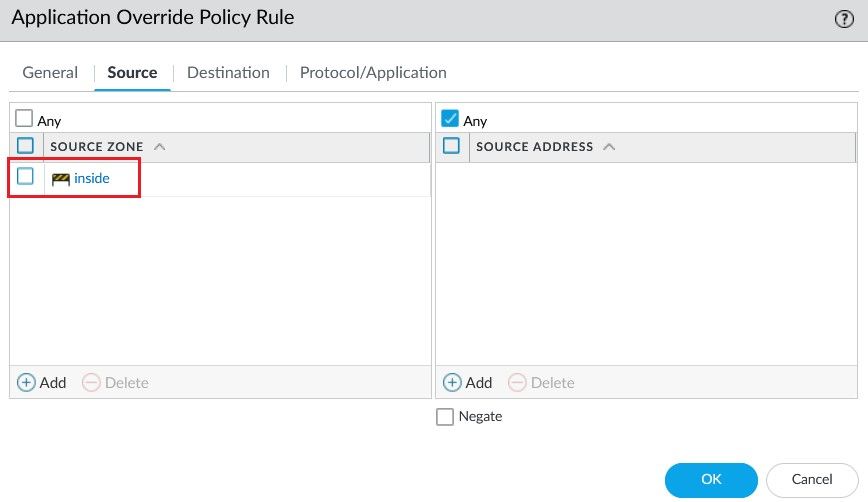
Now create an Application Override Policy.
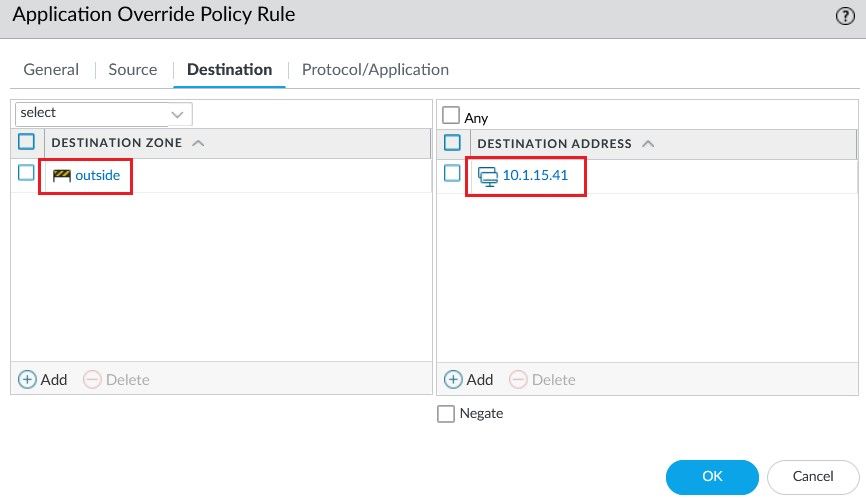
Select Inside as the source zone, Outside as the destination zone and Destination Address 10.1.15.41.
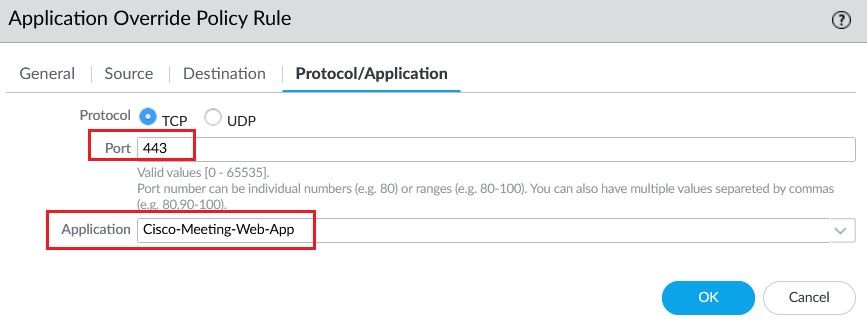
Then Enter the Layer 4 port number and associate the Custom Application created previously.
User accessing the Webbrdge to access a meeting using WebRTC.
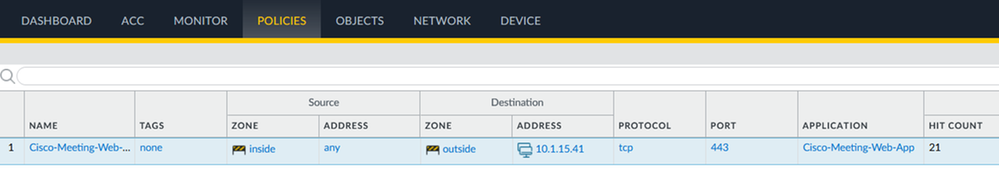
Navigate to Traffic Logs to confirm that the Custom Application identified the SSL Traffic to 10.1.5.41 as a Cisco-Meeting-Web-Application.
- 2957 Views
- 0 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Boradsign application not working when GP is connected in GlobalProtect Discussions
- Security Policy with Destination Criteria in Strata Cloud Manager
- Detect RC4 traffic in Strata Logging Service Discussions
- [SOLVED] - NGFW The Connection To Global Protect On The IPads Times Out!! in GlobalProtect Discussions
- DHCP Relay over SDWAN issue in Advanced SD-WAN for NGFW Discussions