- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
LDAP authentication profile not listing in authentication settings
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- Re: LDAP authentication profile not listing in authentication settings
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2023 01:19 AM - edited 05-26-2023 01:19 AM
Hi,
I have a problem in adding LDAP authentication profile to the authentication settings in Device>Management. I have also tried creating a new authentication profile with LDAP in it. But getting the below error
"system -> authentication-profile 'LDAP_AUTH_WEBGUI' is not a valid reference
system -> authentication-profile is invalid"
Please advice if I have to do any changes somewhere.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2023 05:10 AM
Hello @jeromej
could you please check logs from CLI: tail follow yes mp-log authd.log? This should give definitive answer what the issue is.
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-29-2023 07:54 AM
Connection reset by peer is expected because with ssh command you try to initiate ssh not ldap.
As mgmt and ldap are in same subnet then next step is to take packet capture on mgmt interface.
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CleECAS
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2023 04:28 AM
Man I had found what I did wrong... I had not given the LDAP service route source in the Service route configuration. After giving that our box had connected with the LDAP server and everything works fine now. But earlier it was the same when the LDAP works without any such configuration. I wonder how it worked.
Anyways, thanks for the support and assistance.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2023 05:02 AM
Hello @jeromej
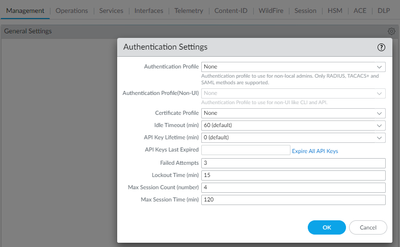
the authentication profile under: Device > Management > Authentication Settings only supports RADIUS, TACACS+ and SAML. If you need to use LDAP to authenticate accounts accessing Firewall, you can do it from: Device > Administrators, then add account and select LDAP profile from drop down list.
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2023 07:17 AM
Authentication Settings droppdown supports using authentication sequences.
You can try to put LDAP profile into auth sequence (Device > Authentication Sequense) and try if choosing auth sequence instead works (I have not tested).
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2023 07:42 AM - edited 05-26-2023 07:47 AM
Hi @PavelK
Thanks for the response.
I tried that already but didn't work and thought that the issue could be with the authentication settings in the management window.
And I have configured the LDAP authentication and started using the LDAP account for logging in to the PA Webgui for the past couple weeks. There was some changes done by my colleague yesterday and when I tried login to the web console today, I started getting authentication error.
And I felt something must be something wrong with connection with the LDAP connectivity. So I tested the connectivity and got the connection error. There is no LDAP configuration issue and I double checked the same.
Is there anything that I am missing to check?
Thanks,
Jerome
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2023 07:46 AM
Thanks for the response.
I have configured the authentication settings the same way that you have mentioned and was using the LDAP account for logging in to the PA Webgui for the past couple weeks. But there was some changes done by my colleague yesterday and when I tried login to the web console today, I started getting authentication error.
And I felt something must be wrong with connection with the LDAP connectivity. So I tested the connectivity and got the connection error. There is no LDAP configuration issue and I double checked the same.
Is there anything that I am missing to check?
Thanks,
Jerome
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2023 07:51 AM
Monitor > System
Filter "( subtype eq auth )"
Any events about LDAP server there? Like auth-server-down for example.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2023 02:41 PM
Hello @jeromej
thank you for reply.
To drill down root cause for failure, could you please follow this KB: How to Troubleshoot LDAP Authentication? Also, make sure that Bind-dn username and password are up to date.
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2023 12:19 AM
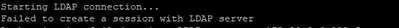
The logs shows the "auth-server-down". But when checking the connectivity between the firewall and the server is good as they both communicate with each other. Please find below the error log.
| Type | Threat/Content Type | Config Version | Generate Time | Virtual System | Event ID | Object | fmt | id | module | Severity | Description |
| SYSTEM | auth | 2816 | 5/27/2023 11:45 | auth-server-down | 0 | 0 | general | critical | LDAP auth server is down !!! | ||
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2023 12:52 AM
Hi @PavelK
I have tried the steps given in the KB and got the below result.
1.1 #show shared server-profile lda - Invalid syntax
1.2 The Base DN not listing automatically. It wasn't listed when I had it configured previously but the LDAP authentication worked until couple days back.
1.4 Couldn't browse the LDAP tree browser when configuring Group-Mapping.
The Bind-DN Username and password are up to date. Yet I am getting this connectivity issue.
Please advice.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2023 05:10 AM
Hello @jeromej
could you please check logs from CLI: tail follow yes mp-log authd.log? This should give definitive answer what the issue is.
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-29-2023 04:17 AM
Hi @PavelK
When checking the logs, I get the above error. It seems that there is some issue with the connectivity.
Is there a way to check if the ldap server receives the request on the port 389 from Palo alto? Since PA has removed telnet from PANOS 5.0, I couldn't find a way to know that.
Thanks,
Jerome
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-29-2023 04:49 AM
Is Palo mgmt interface and ldap server in same subnet or does traffic from Palo mgmt interface traverse Palo dataplane so you could see logs?
To test tcp 3way handshake you can use command "ssh port 389 host <ldap server ip>"
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-29-2023 05:34 AM
Yes @Raido_Rattameister , PA mgmt interface and ldap server are in the same subnet.
When test the handshake, I get the below result.
Thanks,
Jerome
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-29-2023 07:54 AM
Connection reset by peer is expected because with ssh command you try to initiate ssh not ldap.
As mgmt and ldap are in same subnet then next step is to take packet capture on mgmt interface.
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CleECAS
Palo Alto Networks certified from 2011
- 3 accepted solutions
- 11465 Views
- 15 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GP and multi factor auth in GlobalProtect Discussions
- Global Protect Portal / Clientless VPN does not recognize SAML username after update to 10.1.14-h20 in GlobalProtect Discussions
- Global Protect Connectivity Issue in GlobalProtect Discussions
- Okta Verify window behind GP login window fix in GlobalProtect Discussions
- PA Global Protect in GlobalProtect Discussions